A couple of weeks ago, Proofpoint researchers detected a new malicious campaign identified as OiVaVoii employing hijacked Office 365 accounts and a sophisticated combination of phishing tactics, data theft, and malicious websites. In the reported cases, the use of malicious applications for the theft of OAuth tokens, deployment of persistent phishing campaigns, lateral movement attacks and malware distribution have been detected.
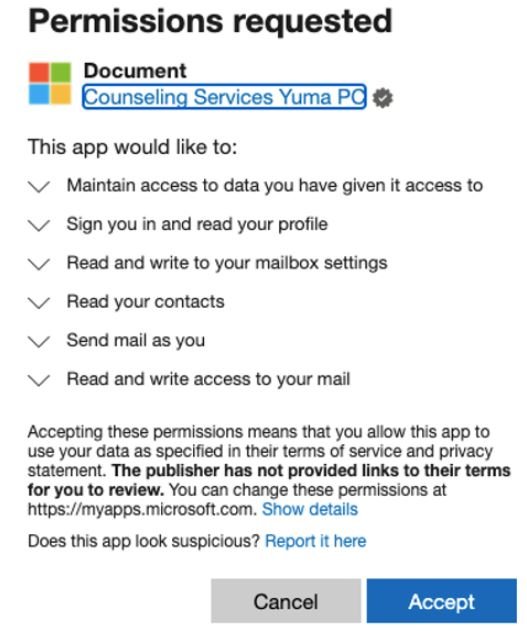
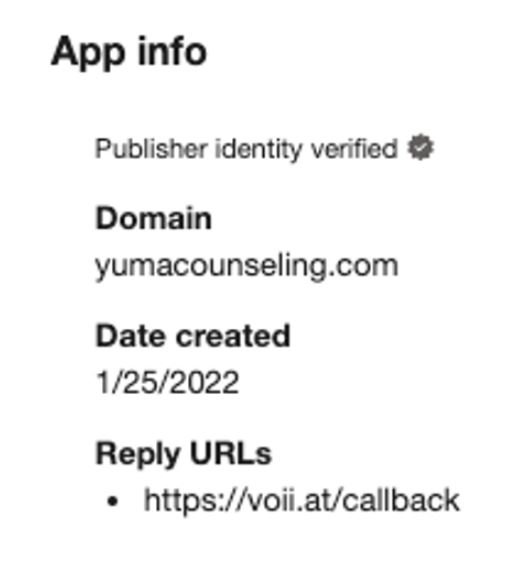
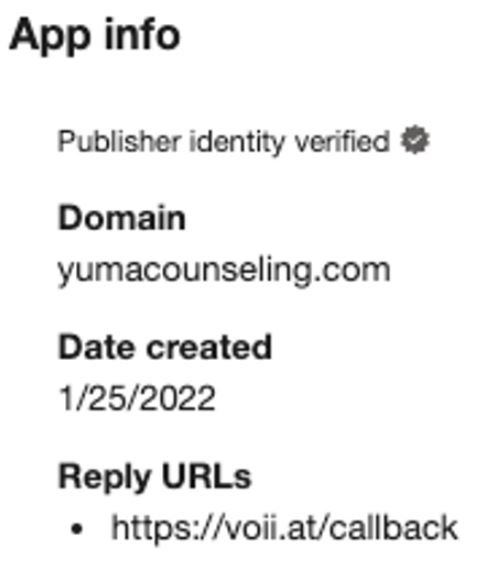
In their report, the researchers pointed to the detection of five malicious OAuth applications related to this campaign. These applications were developed by Yuma Counseling Services, a supposed verified provider; at least three of these third-party apps were created by two verified publishers, suggesting that app owners are controlling a compromised user account in a legitimate Office account.
When applications are ready, authorization requests are sent to specific Office users, indicating that this is a spear phishing campaign. The attack relies heavily on trust in the apparent legitimacy of the malicious email, allegedly sent by a publishing organization; going forward, hackers just have to wait to complete the OAuth token theft.
According to the report, the OiVaVoii attack can be divided into the steps listed below:
- Hackers use the reply URL to redirect the user to a standalone screen, which means that just one click in any area is enough to reload the same page, locking the user into a loop
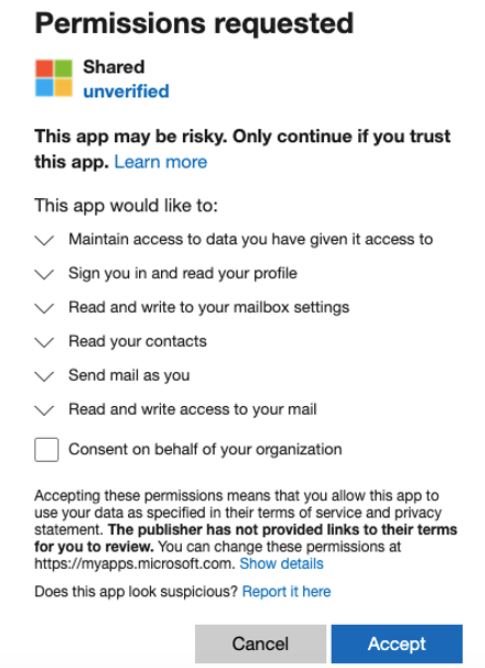
- Microsoft software is supplanted using counterfeit icons
- Malicious applications use Man-in-The-Middle (MiTM) attacks for credential theft and as a tactic to generate persistence
- The attack specifically targets high-level users in private organizations around the world, allowing attackers to gain an ideal access point to the affected networks
- Detected applications requested similar permissions, mainly related to inbox access, allowing the sending of internal and external malicious emails, theft of sensitive information and creation of inbox rules
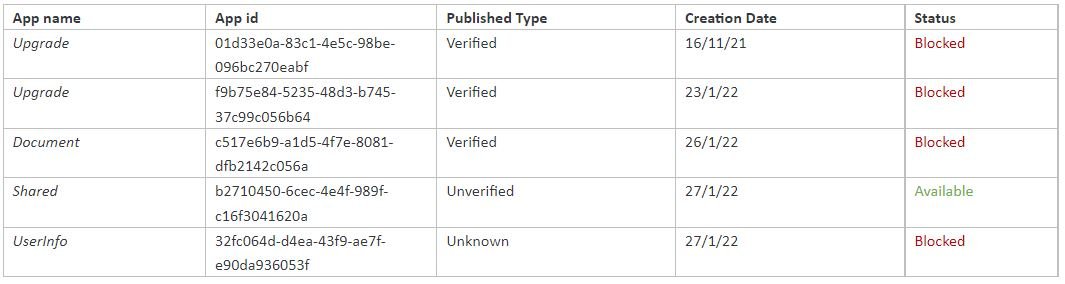
The following table shows the malicious apps linked to the campaign:
Faced with this security risk, Microsoft recommends implementing some preventive measures, including limiting for third-party applications and using additional security solutions, in addition to maintaining a strict email security policy for all members of an organization.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.