Cybersecurity specialists report the detection of a new attack variant that would allow exploiting the security weaknesses of Adobe Creative Cloud users to deliver malicious content.
In late 2021, Avanan researchers observed a new wave of hacking in which attackers created accounts at Adobe and imported PDF files capable of redirecting users to malicious websites to collect their login credentials.
As mentioned above, the attack involves creating a user account in Adobe Cloud Suite, from where the malicious PDF file will be imported. The file should contain a link to redirect the target user to a website with a form, which upon completion will send the entered data to a location controlled by the attackers.
For end users of products like Adobe Created Cloud, it’s quite common to receive these kinds of messages in their inbox, so hackers could easily evade protections in their email system considering Adobe is a trusted sender.
In the following example, we see an email containing a seemingly harmless PDF file sent through Adobe Acrobat:
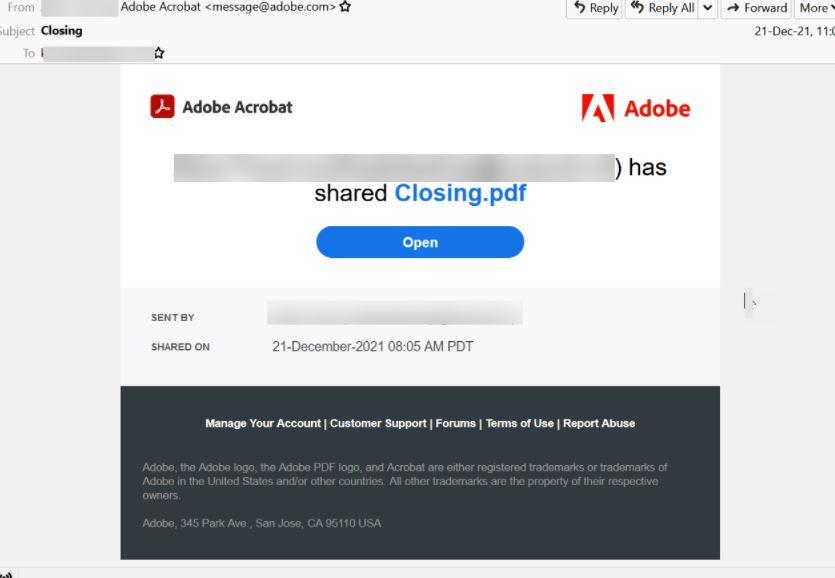
If the user selects “Open”, they will be redirected to an Adobe Document Cloud website:

A classic credential collection format, hosted outside the Adobe suite, will appear on this page:
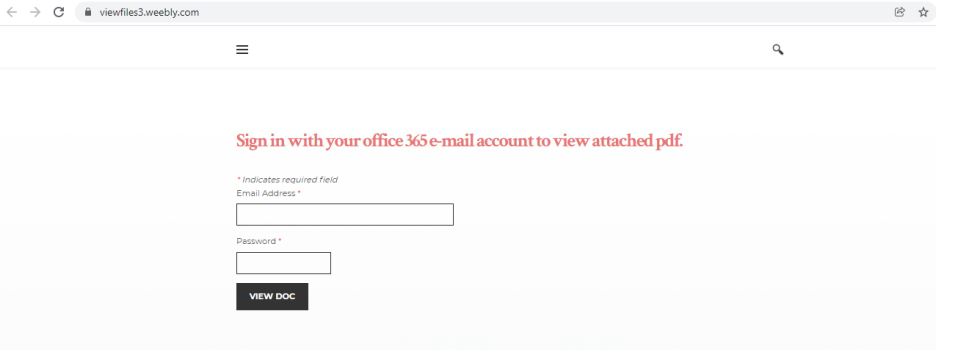
This attack variant allows threat actors to abuse Adobe’s suite in order to host and hide credential-harvesting websites. Since the end of 2021, Avanan experts detected nearly 400 attack attempts linked to this campaign.
Threat actors can also apply other mechanisms to make this email address difficult for antivirus scanners and end users to detect. However, in most cases it is enough for users to see that the email comes directly from Adobe to fully trust the content of the message, without even suspecting that it is a hacking attempt.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
