A report by security firm CrowdStrike details the detection of a hacking campaign using containers to launch distributed denial of service (DDoS) attacks against critical computing infrastructure in Russia and Belarus.
Thanks to a honeypot, the researchers discovered two different Docker images targeting Russian and Belarusian websites for the deployment of DoS attacks. The two images have been downloaded more than 150,000 times and the domains appear to be targets of Ukraine’s IT Army, recently made up of cybersecurity researchers and developers dedicated to cyberwarfare tasks stemming from the Russian invasion.
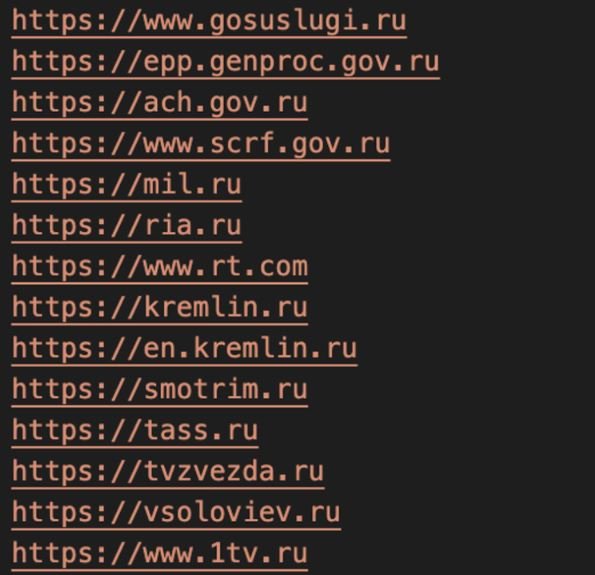
For CrowdStrike’s senior vice president of intelligence, Adam Meyers, this is a potential threat to organizations that may discover that their IT infrastructure is being used to help launch these attacks without their knowledge. Once cybersecurity analysts inside Russia and Belarus determine the source of the attacks, they could launch powerful counterattacks against critical infrastructure in Ukraine, creating new attack escalations.
Between February and March 2022, Docker Engine honeypots set up by Crowdstrike were compromised four times to run two different Docker images targeting Russian and Belarusian websites. Honeypots were compromised through an exposed Docker Engine API, a technique commonly used to compromise incorrectly configured container engines.
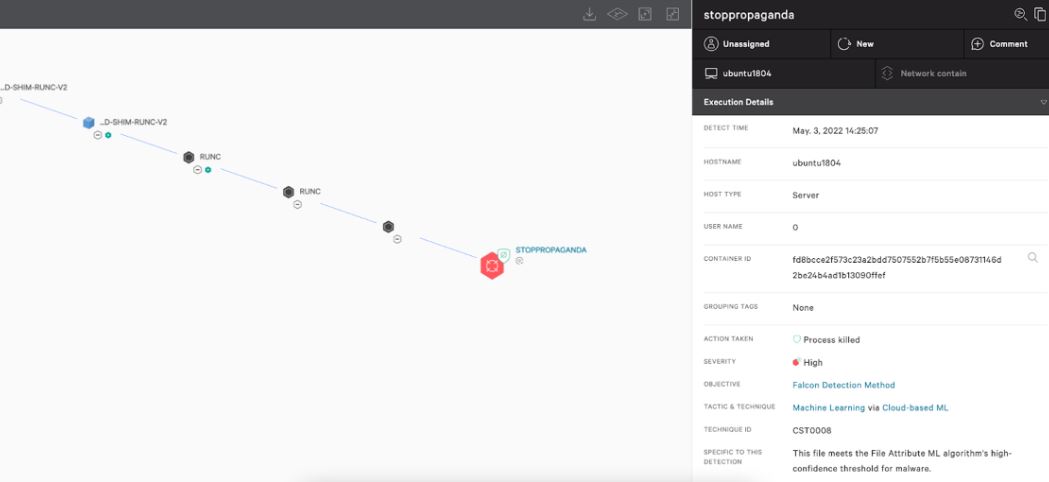
The first Docker image was identified as abagayev/stop-russia and is hosted on Docker Hub. The Docker image contains a Go-based HTTP benchmarking tool called bombardier and is identified with the hash 6d38fda9cf27fddd45111d80c237b86f87cf9d350c795363ee016bb030bb3453. Threat actors abused this tool as a DoS utility that starts automatically when a new container based on Docker images is created. When starting, the target selection routine chooses a random entry from a coded target list. Later versions of this Docker image alternately select one of the first 24 entries from the target list based on the time of the attack.
The second image was identified as erikmnkl/stoppropaganda and has been downloaded more than 50,000 times from Docker Hub. The image contains a custom Go-based DoS program called stoppropaganda with the hash 3f954dd92c4d0bc682bd8f478eb04331f67cd750e8675fc8c417f962cc0fb31f and sends HTTP GET requests to a list of affected websites until they are overloaded.
Most containers are configured by developers with no cybersecurity training and who assume that these implementations are not very vulnerable to cyberattacks, which facilitates the deployment of silent hacking campaigns. In addition, there are more and more malicious tools for the compromise of the IT infrastructure on which legitimate containers depend, which greatly increases security risks.
Relatively little information is still known regarding this campaign, although Crowdstrike could publish new updates in the coming days.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
