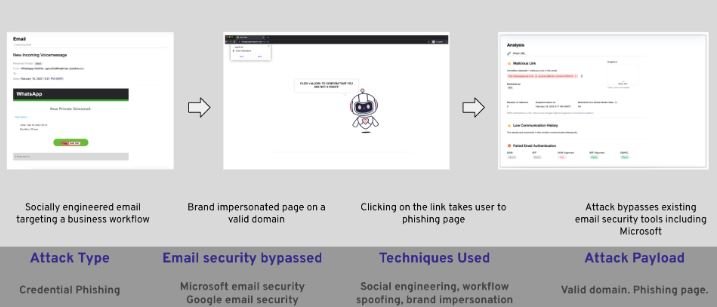
Researchers from the firm Armblox report the detection of a phishing campaign in which threat actors use a false voice message notification on WhatsApp in order to install a malware variant for data theft on the target system. The attack has been identified in at least 28,000 Office 365 and Google Workspace mailboxes.
The hackers use a social engineering email titled “New Incoming Voice Message”. As shown in the screenshot below, in the body of the email was an alleged WhatsApp message, suggesting the victim click a “Play” button to listen to the message.
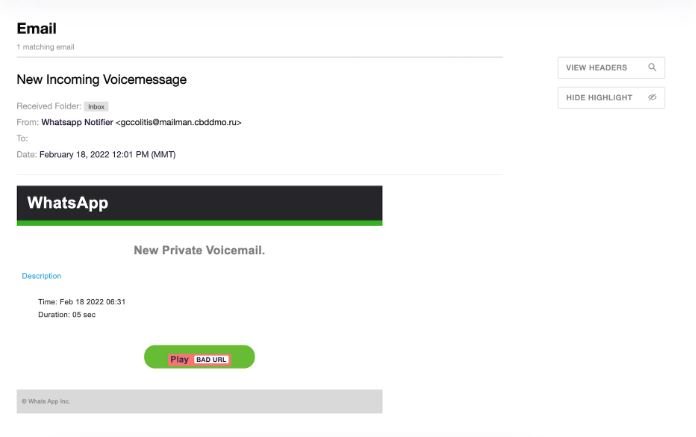
The domain from which the message was sent (mailman.cbddmo.ru) appears to be associated with a road safety website in Russia. According to the website, this organization is dedicated to providing roadside assistance to Moscow and belongs to the Russian Ministry of Internal Affairs.
Researchers believe that threat actors exploited a vulnerability to take control of this platform and use it to launch phishing attacks, so these messages do not raise suspicions on the affected systems.
If users fall into the trap and click on the fake “Play” button, they are redirected to a page from which they will try to install a JS/Kryptik Trojan. This is obfuscated JavaScript code embedded in HTML pages that redirects the browser to a malicious URL and implements a specific exploit.
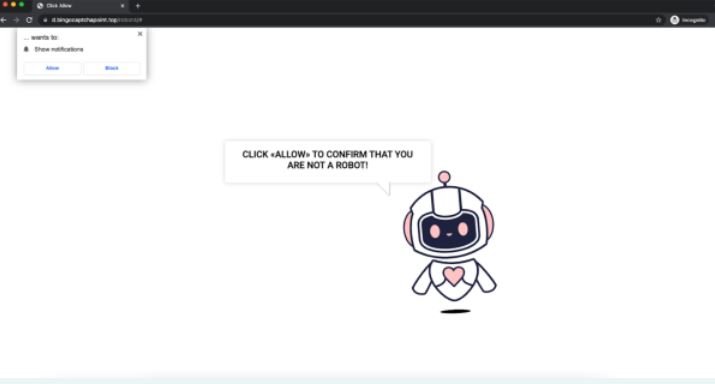
Affected users encounter a CAPTCHA-like verification message, which is the trick used by threat actors to install the payload on the affected system. By installing the Infostealer malware variant, hackers will begin to collect sensitive information stored in the user’s browser, mainly access credentials.
This is a powerful and highly effective campaign, so users of Office 365 and Google Workspace deployments should remain on the lookout for potential attack attempts. As with any other phishing campaign, users can protect themselves by ignoring unsolicited emails, trying not to visit unknown websites, and enabling all possible security mechanisms to detect potential security threats.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
