Cybersecurity specialists report the detection of various malicious campaigns based on the abuse of a component in Microsoft Build Engine (MSBuild) in order to execute a Cobalt Strike payload on compromised systems. As you may already know, MSBuild is an implementation for building applications on Windows that includes a component known as Tasks, designed to designate components that run in development phases.
Renato Marinho, a researcher at cybersecurity firm Morphus Labs, reports detecting at least two malicious campaigns dedicated to engaging Tasks and other MSBuild components for remote code execution on exposed systems.
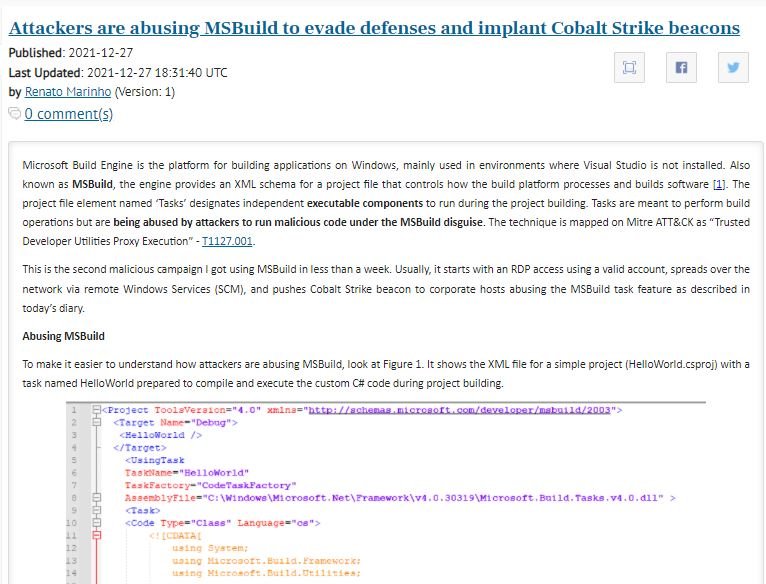
According to Marinho, threat actors gain access to the affected systems using Remote Desktop Protocol (RDP), leveraging remote Windows Services for lateral movement, and abusing MSBuild to run the Cobalt Strike Beacon payload. This malicious MSBuild project was designed to compile and execute specific C# code that subsequently decodes and executes the payload on the victim’s system.
The expert adds that, after confirming that the Cobatl Strike payload was used in the attack, he was also able to decrypt the communication with the C&C server employed by the hackers, which was encrypted with SSL.
Finally, Marinho mentions that as a protection measure against this variant of hacking, organizations must enable the Windows Defender Application Control (WDAC) policy, which will block the ability of Microsoft-signed applications to execute other forms of code: “There is a note for MSBuild.exe that, when the system is used in a development context to create managed applications, the recommendation is to allow MSBuild.exe in code integrity policies,” concludes the expert.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
