The use of email addresses for malicious purposes is a practice that has existed for more than 20 years and has since continued to grow, with phishing and spam as the main and most common problems for users of these services.
A recent trend is the use of legitimate email addresses for malware deployment through an attack known as session hijacking. This practice seems to have no end, besides that it has a much greater degree of success than other cyberattacks, so users need to learn about the most essential security measures and even tools that help prevent these attacks.
Fortunately there is a free tool so that any user can very easily check if their email addresses or web domains are being used by threat actors.
Emotet operators have developed a gigantic botnet through one of the most effective email malware campaigns ever registered. Although it started as a banking Trojan, this malware moves using phishing emails that redirect users to sites controlled by threat actors.
The group of operators, allegedly established in Russia, also employs some tactics to make their attacks more credible, such as using responses in a wire of emails, making it difficult for victims to detect malicious activity.
To find out if Emotet operators have managed to compromise their email account, you can use the haveIbeenEMOTET website, a platform that provides users with up-to-date information about currently active cyberattack campaigns similar to Have I Been Pwned, an initiative promoted by security specialist Troy Hunt.
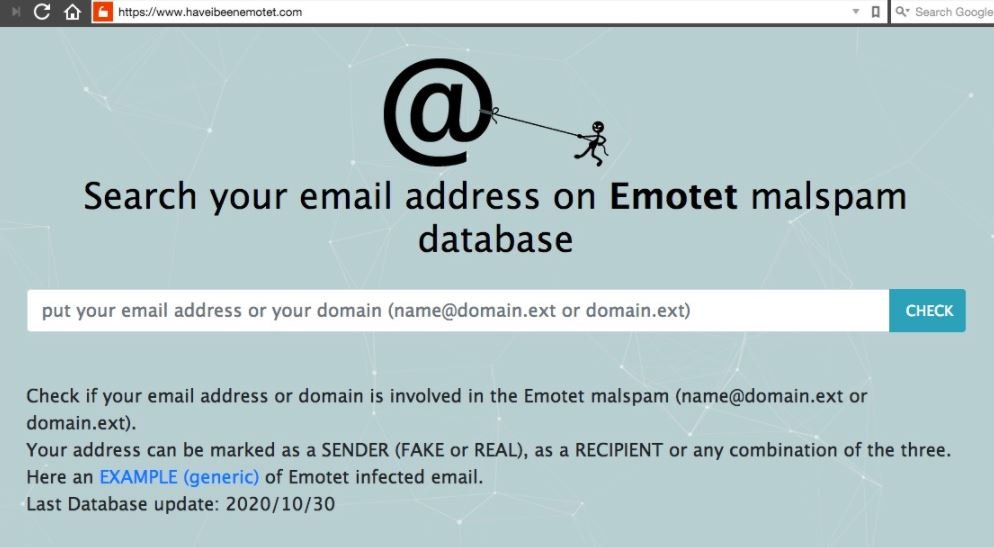
Verification process
- Log in to the haveIbeenEMOTET website and, once inside, provide your email address or domain name and press ENTER
- You will get one of the following results:
- Confirmation that your email address has not been used in an Emotet spam campaign
- Confirmation that your address has been used in an Emotet campaign
- If threat actors have used your email address or domain, it will be marked as “Fake Sender”, “Actual Sender” or “Recipient”
- If you get one of the latest results, you should take steps to repair the possible damage
The platform will also advise you in case your online resources have been compromised.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
