A recent vulnerability in the OverlayFS subsystem of the Linux kernel has been found as CVE-2023-0386, with a CVSS score of 7.8. The flaw, which is caused by the careless handling of user copies of a capable file from a nosuid mount to another mount, permits unauthorized access to the execution of setuid files with capabilities. This uid mapping flaw creates a serious security risk by enabling local users to increase their privileges on the system.
A proof-of-concept (PoC) attack for this vulnerability was created by researcher Xkaneiki, highlighting the possible dangers CVE-2023-0386 poses. On Ubuntu 22.04, the PoC vulnerability was tried out, and root access was obtained. The presence of the proof-of-concept (PoC) exploit code for CVE-2023-0386 emphasizes how urgent it is for developers and system administrators to prioritize security updates to fix this Linux kernel privilege escalation flaw and stop prospective attacks.
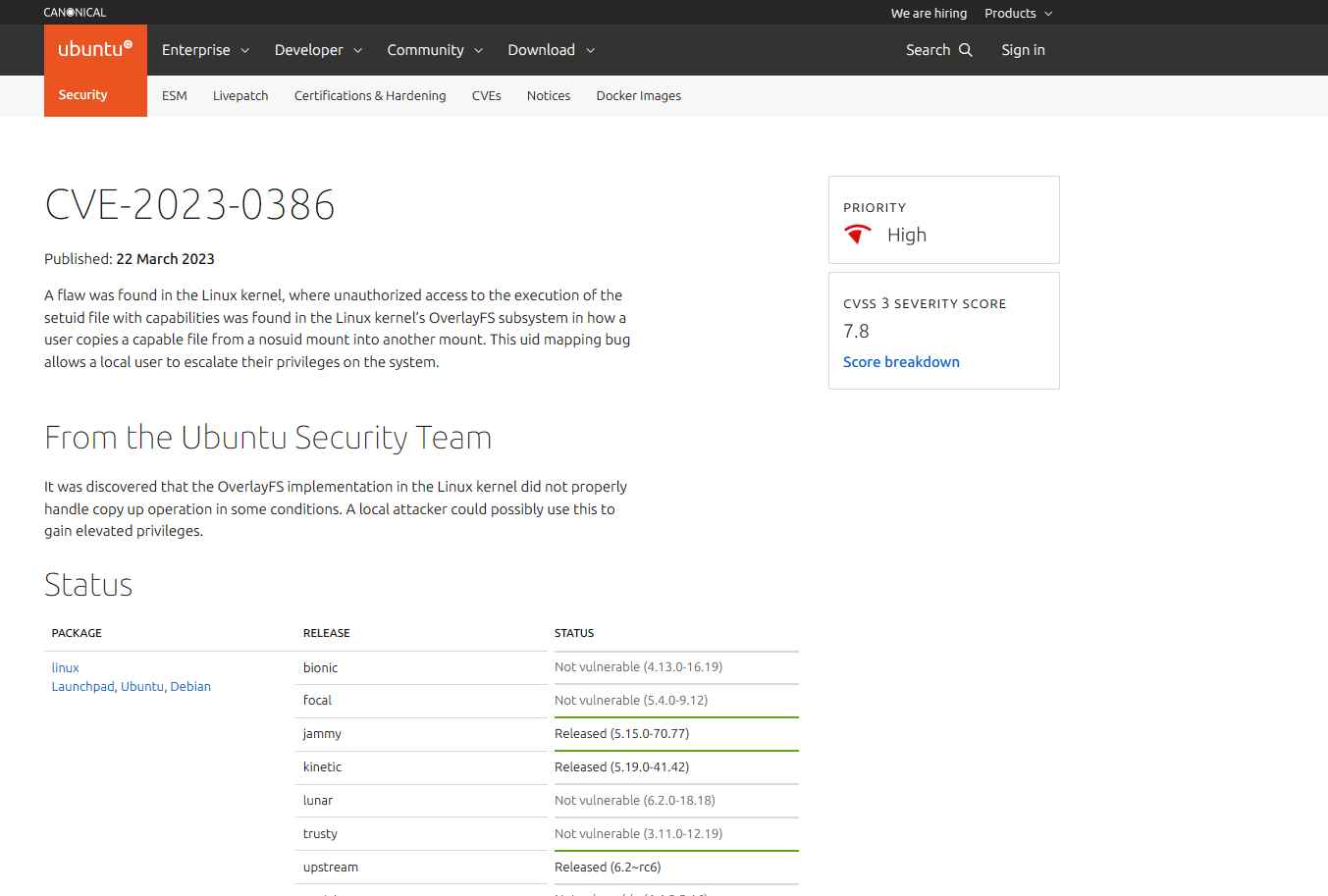
An attacker with low-privileged user access to a Linux computer with an overlay mount that has a file capability in one of its layers may escalate their privileges up to root thanks to the Linux kernel privilege escalation problem, identified as CVE-2023-0386. A capable file from a nosuid mount may be copied onto another mount by the attacker to do this. This vulnerability is comparable to CVE-2021-3847 but has a higher priority since it may be exploited with less permissions.
Reproduction procedures:
- Mount a FUSE filesystem that exposes a root-owned, world-writable setuid/setgid binary.
- Disable sharing of user/mount namespaces.
- Mount an overlay with a user-writable higher directory and the FUSE filesystem as the bottom directory. Make sure the top directory is mounted on a disk without using the ‘nosuid’ command.
- To update the file’s mtime and initiate a copy-up, touch the file on the merged path.
- Because the kernel does not clear the setuid/gid bits, a copy of the binary with the setuid bits will be present in the higher directory.
- If you run the binary from the top directory, root will be the user who is executed.
In contrast to CVE-2021-3847, which includes file capabilities (xattrs) that are subject to unique restrictions inside user namespaces, CVE-2023-0386 attacks setgid/setuid bits, which are not user-namespace-specific. Furthermore, FUSE does not need physical access and is present in many production situations, in contrast to CVE-2021-3847, which relates to USB mounts that need physical access and are often blocked in such contexts.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
