In the tech realm, the unsettling words ‘zero-day vulnerability’ can send shivers down the spine of even the most hardened IT veterans. The recent discovery and the swift action against such a vulnerability in Atlassian’s Confluence software suite have once again brought to light the constant battle between cybersecurity measures and malicious actors.
On October 4, 2023, Atlassian, a leading provider of team collaboration and productivity software, released a security advisory announcing a critical zero-day privilege escalation vulnerability identified as CVE-2023-22515 in its Confluence Data Center and Server. This zero-day flaw, which was previously unknown to Atlassian, had already been exploited against a limited subset of customers.
The vulnerability is remotely exploitable, allowing external attackers to create unauthorized administrator accounts and gain access to Confluence servers. The flaw doesn’t impact Confluence versions prior to 8.0.0 or Confluence sites accessed via an atlassian.net domain, indicating a limited scope of potential exploitability but a significant risk within that scope.
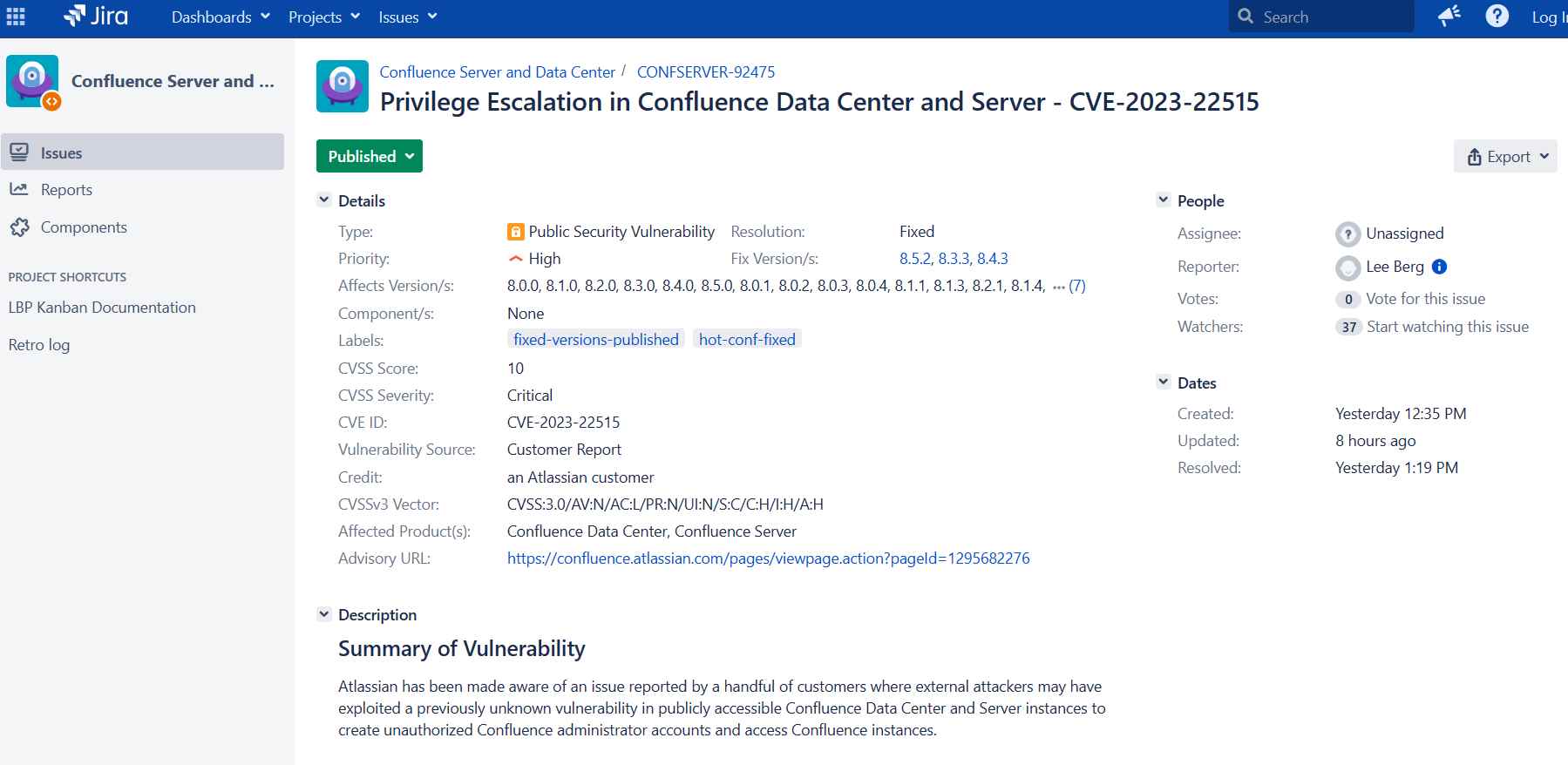
Atlassian promptly disclosed and patched this vulnerability on the same day, reflecting the critical nature of the flaw. It specifically impacts the self-managed versions of Atlassian’s Confluence Data Center and Server, which are components of Atlassian’s popular workspace suite. The vulnerability was reported by a handful of customers where it was used by external actors to create unauthorized Confluence administrator accounts and access Confluence instances on publicly accessible servers.
The company described CVE-2023-22515 as a critical privilege escalation vulnerability and confirmed that it affects Confluence Data Center and Server versions 8.0.0 and later. Instances on the public internet are particularly at risk, as this flaw is exploitable anonymously, emphasizing the potential for widespread unauthorized access if left unaddressed.
In the wake of this discovery, organizations using affected versions of Confluence Data Center and Server are urged to apply the patches or follow the mitigation steps recommended by Atlassian promptly. The swiftness in Atlassian’s response underscores the importance of timely vulnerability management and patch deployment in the face of zero-day threats.
The technical details regarding CVE-2023-22515 indicate a privilege escalation vulnerability in Atlassian Confluence, affecting versions from 8.0.0 onwards. Atlassian recommends upgrading to the fixed versions or implementing mitigations if an immediate upgrade is not feasible. Additionally, engaging security teams and checking for indicators of compromise is advised. The flaw has been rated a critical 10.0 on the CVSS scale, reflecting its severe impact and exploitability. The affected platforms are on-premises instances of Confluence Data Center and Server versions 8.0.0 and later.
This event also accentuates the need for robust security postures and continuous monitoring to detect and respond to vulnerabilities before they can be exploited. The cloak and dagger nature of zero-day vulnerabilities requires an ever-vigilant approach to cybersecurity, highlighting the continuous cat and mouse game between attackers and defenders in the digital realm.
Moreover, it reiterates the essence of community-driven vulnerability reporting and the significance of a collaborative approach towards a more secure digital ecosystem. The rapid disclosure and remediation of the CVE-2023-22515 flaw exhibit a promising stride in the ongoing battle against cyber threats, setting a precedent for other tech giants to foster a culture of prompt response and transparency in handling security vulnerabilities.
The indicators of compromise (IoCs) for CVE-2023-22515, as per Atlassian’s guidance, include detecting unexpected members in the confluence-administrators group which could signify unauthorized access to the Confluence instances. This detection can help in identifying whether the vulnerability has been exploited in your environment.
As the dust settles on this particular incident, the tech community and the myriad of organizations using Atlassian’s suite of tools can breathe a sigh of relief, yet the incident serves as a stark reminder of the relentless evolution of cyber threats and the indispensable role of proactive security measures in safeguarding digital assets.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
