Cybersecurity specialists report a sudden increase in the detection of phishing emails specially designed to steal the Office 365 credentials of affected users. According to the report, presented by Kaspersky, the actors behind this campaign are using two different phishing kits, identified as Iamtheboss and MIRCBOOT.
According to the researchers, these messages are presented as supposed fax notifications, which could be striking for users because they take the image of various recognized companies, including Kaspersky itself, giving the message a legitimate appearance.
Experts mention that one of the targets of the campaign is the abuse of Amazon Simple Email Service (SES), which allows developers to send emails from Amazon applications. This campaign is based on a stolen SES token used by an outside contractor during testing of the 2050.earth website; this website was part of a Kaspersky project that featured an interactive map hosted on Amazon’s infrastructure, making it a target of interest to hackers.
For now, it is unknown which other companies have been affected by a similar campaign, although the report suggests that threat actors are in possession of other SES tokens. After identifying this campaign, Kaspersky’s SES token was revoked as a security measure.
As mentioned above, the phishing emails associated with this campaign are usually hidden under the façade of a “fax notification” that redirects users to a platform where their Office 365 credentials will be extracted. The following is an example of these messages:
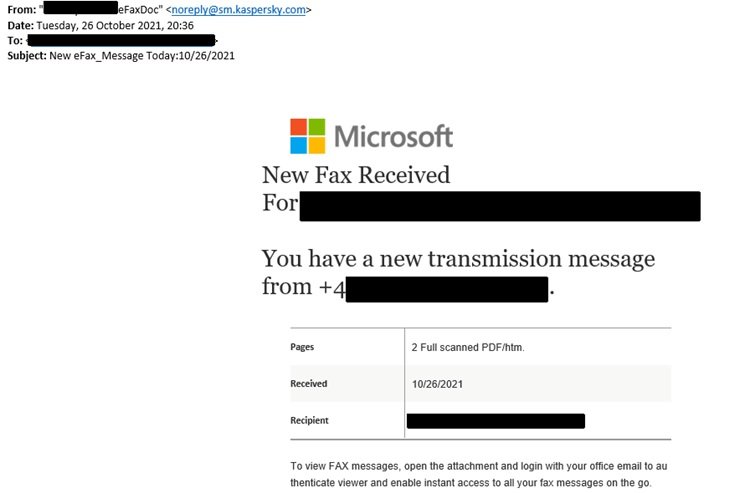
Kaspersky identified the tools used by the campaign operators, finding the use of the malicious kits Iamtheboss and MIRCBOOT.
MIRCBOOT is a phishing kit recently detected as part of a phishing platform as a service (PhaaS), operations that offer its affiliates all the tools and advice necessary to deploy phishing campaigns in exchange for monthly subscriptions. A little less is known about the Iamtheboss phishing kit, although researchers are still analyzing its components.
Years go by and phishing remains one of the most effective and lucrative attack tactics for threat actors. Faced with this risk scenario, the best option that organizations have is prevention, as a phishing attack becomes more effective as hackers can deceive a target user.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
