Recent events have revealed the existence of a widespread cybercriminal group going by the name “Lemon Group,” which is responsible for the widespread distribution of malware on thousands of Android devices. This virus, known as “Guerilla,” has been pre-installed on about nine million Android-based TV boxes, TVs, watches, and smartphones. All of these devices run Android. Guerrilla is being used by the fraudsters who are behind this operation to carry out a variety of nefarious acts, including as intercepting single-use passwords, hijacking the user’s WhatsApp sessions, and setting up reverse proxies.
The illicit activities carried out by the Lemon Group have been laid bare in a detailed study that was recently published by the cybersecurity firm Trend Micro. During the course of their study, experts from Trend Micro uncovered a link between the infrastructure of the Lemon Group and the infamous Triada Trojan campaign that has been running since the year 2016. The Triada Trojan was a piece of malicious software that was developed expressly for the purpose of committing financial fraud. It was found to be pre-installed on a number of Android devices that were manufactured in China by low-cost companies.
The in-depth analysis compiled by Trend Micro offers more insights into the operating tactics used by the Lemon Group. In spite of the fact that the organization is active in a variety of endeavors, such as big data research, marketing, and advertising, the group’s primary goal is to make effective use of the potential offered by big data. They use this data to evaluate the shipments that the manufacturers send out, obtain detailed data for the purpose of creating targeted promotions for software, and compile ad material that has been gathered from a variety of users. The Lemon Group is able to facilitate the illegal sale of stolen SMS messages, hacked social media accounts, and active involvement in fraudulent advertising schemes by infecting millions of Android smartphones. This essentially transforms the devices into mobile proxies.
The specific approaches that Lemon Group uses to infect devices are not now public knowledge. However, Trend Micro has clarified that its researchers have proven that infected devices have been through a process called re-flashing, in which the original ROMs have been replaced with modified versions carrying the Guerilla virus. This procedure was performed by replacing the original ROMs with modified versions containing the Guerilla malware. The researchers found more than 50 unique infected ROMs that targeted a variety of Android device manufacturers.
Guerrilla operates as a plugin that combines the functionality of a number of other plugins in order to do a variety of tasks. Intercepting one-time passcodes that are delivered over SMS for commonly used platforms like WhatsApp and Facebook is one of the functions that comes with these capabilities. An additional plugin installs a reverse proxy, which gives attackers the ability to get illegal access to the network resources of the victim. In addition, other plugins are capable of stealing Facebook cookies, hijacking users’ WhatsApp sessions in order to send unwanted messages, displaying invasive adverts while users are interacting with legal programs, and stealthily downloading or removing apps in accordance with the malware’s instructions.
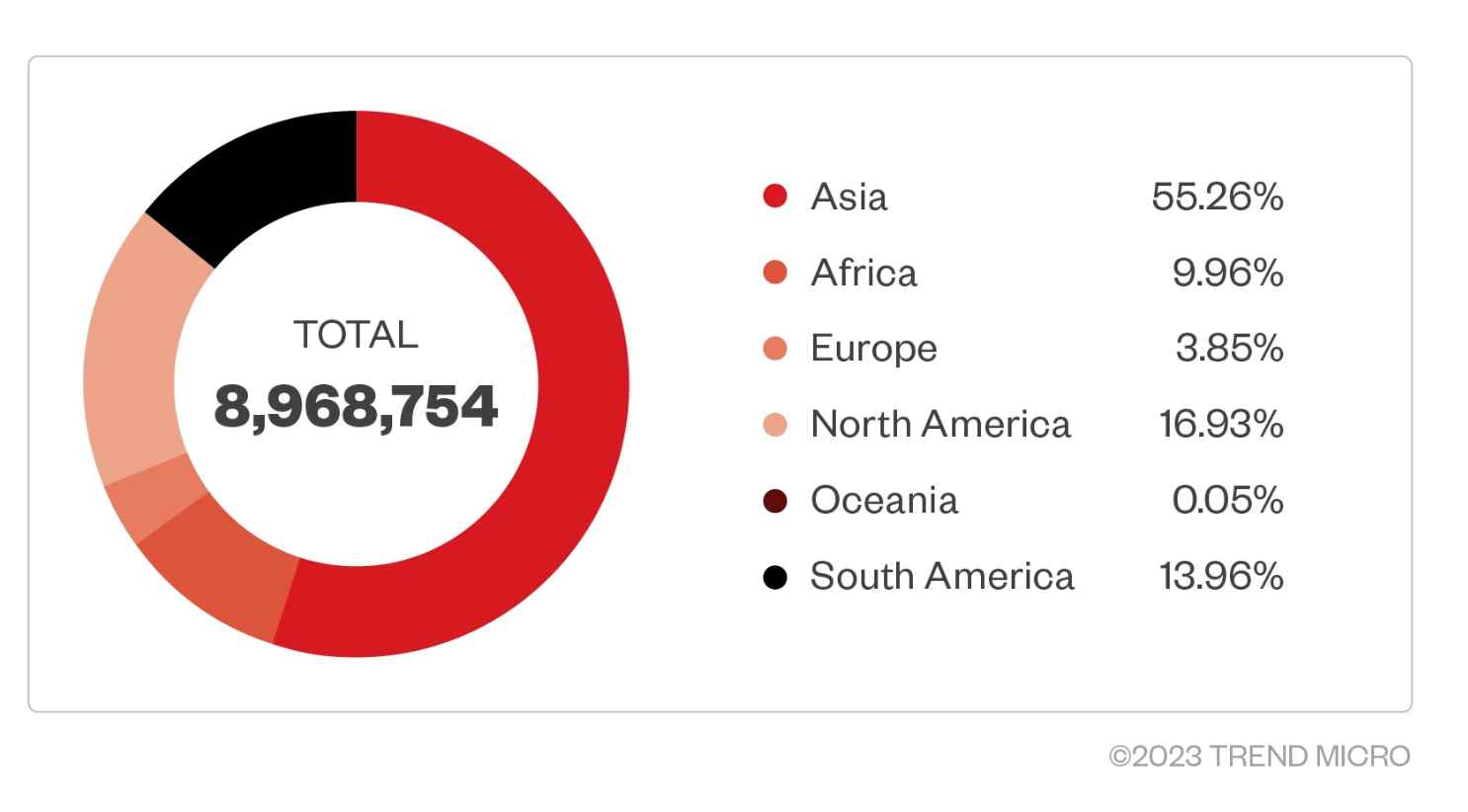
At least 8.9 million Android smartphones had their security penetrated by the threat actors, the vast majority of them were inexpensive phones. The United States, Mexico, Indonesia, Thailand, Russia, South Africa, India, Angola, and the Philippines have the largest number of infected devices, followed by Argentina, Angola, and the Philippines. On the other hand, the precise number of Android devices that have been infected with the Guerilla virus is not known for certain. This is due to the fact that some devices have not yet established links with the command and control servers used by the cybercriminals.
A stunning discovery was made by cybersecurity professionals from Trend Micro as a result of their attentive surveillance of the operations of the Lemon Group. They have found an astounding total of more than 490K mobile numbers that are tied to requests for one-time passwords used in SMS-based applications like as JingDong, WhatsApp, QQ, Line, Facebook, and Tinder. This is a startling amount of mobile numbers. The staggering number of infected devices, all of which are connected to a single service, is a stunning witness to the global effect and extent of the malevolent operations carried out by the cybercriminal gang.
The Guerrilla virus has a structure that is modular, and each plugin was developed to support a particular purpose. These features include the following:
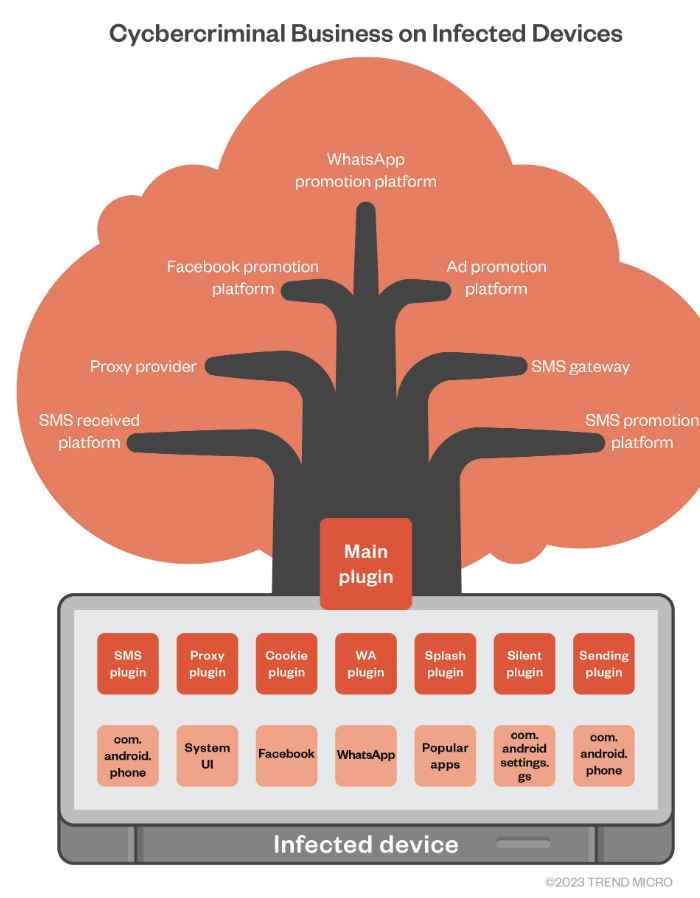
Intercepts one-time passwords that are transmitted through SMS with the help of the SMS Plugin. It goes after a variety of sites, including Facebook, WhatsApp, and JingDong, among others.
Plugin for selling proxies and proxies themselves: to establish a reverse proxy connection from inside an infected phone and to make advantage of the network resources offered by the compromised mobile device in return for revenue generated by their DoveProxy operation.
This plugin hooks into Facebook-related applications and intercepts particular activity to launch events. It is also known as the Cookie plugin, the WhatsApp plugin, and the Send plugin. In addition to this, the plugin takes over WhatsApp sessions in order to deliver unwanted messages.
Hook popular applications to intercept certain activity, such as initiating event request advertising from adverts, with the help of the Splash Plugin. When victims are trying to use genuine programs, it will start showing them invasive adverts.
This plugin is responsible for carrying out the quiet installation and starting the application that was previously installed.
The analysts have a hunch that the attack vector that the Lemon Group used was one that targeted the supply chain. Threat actors exploited vulnerabilities in third-party applications or installed malware-infected firmware to compromise the system.
The Lemon Group is primarily concerned with the usage of large amounts of data that have been obtained from hacked devices in order to keep an eye on consumers who may have been previously infected with additional harmful payloads that have been specifically tailored for certain fraudulent actions, such as displaying adverts to app users who are located in particular locations.
“We detected over fifty distinct images originating from a wide range of sellers that carried initial loaders. When downloading and injecting additional payloads, more current versions of the loaders make use of fileless approaches. As a result of this most recent turn of events, public repositories of threat information no longer include these updated loaders, and the forensic examination of such devices and images has become noticeably more difficult,” the paper adds. “When comparing the number of devices being analyzed to the number of devices that Lemon Group is said to have reached, 8.9 million, it is highly likely that additional devices have been preinfected but have not yet exchanged communication with the C&C server, have not been used or activated by the threat actor, or have not yet been distributed to the targeted country or market. Shortly after presenting at Black Hat, they saw that the website had been taken down.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
