Foxconn, a major electronic company, has confirmed a ransomware attack that hit one of its facilities in Mexico during Thanksgiving weekend. Apparently, threat actors would have managed to extract sensitive files before encrypting the victims’ systems.
This company has become a giant in its field worldwide, employing more than 800 ml people through the parent company and its subsidiaries Sharp Corporation, Innolux and FIH Mobile.
Just a few days ago, the operators of the DoppelPaymer ransomware published files belonging to Foxconn on their site dedicated to publishing leaks as a product of their attacks. The compromised information includes internal business documents, although there does not appear to be any personal information from employees. Soon after, some members of the cybersecurity community confirmed that the company was dealing with an incident detected at Foxconn CTBG MX, based in Ciudad Juarez, Mexico, where electronic equipment is assembled and shipped to various locations in America.
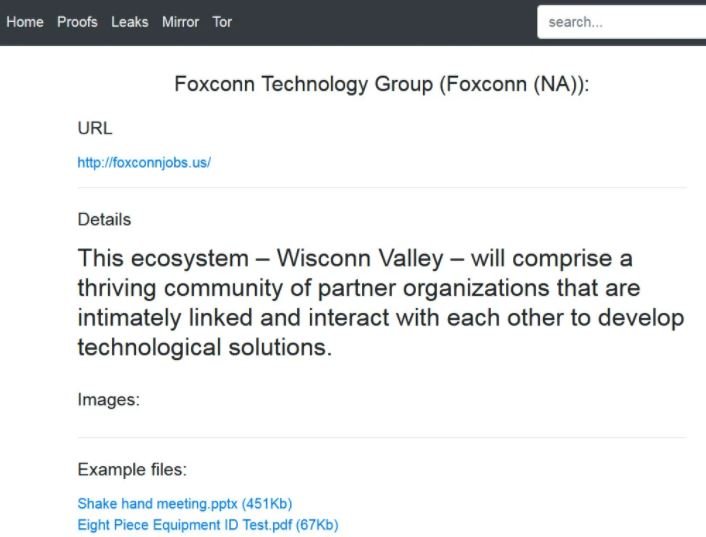
Since the attack, the affected installation website has remained inactive, displaying only one error message.
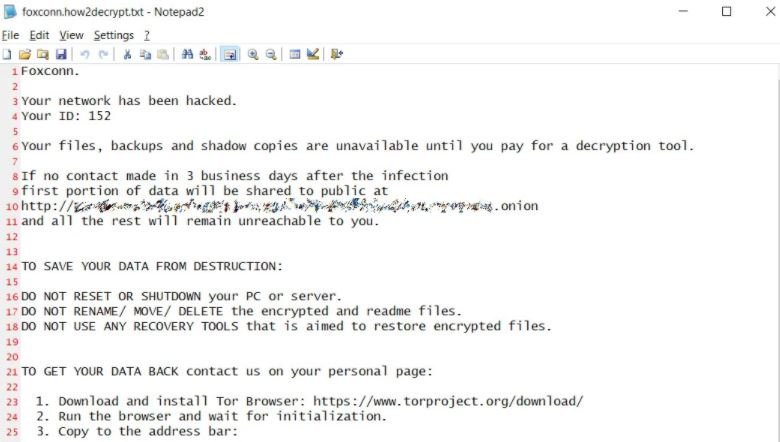
A source close to the company shared the ransom note sent by threat actors:
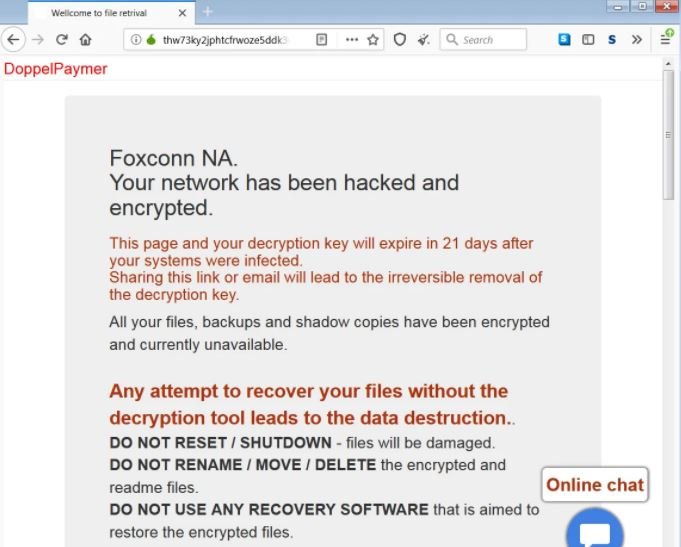
The message includes a link to the doppelPaymer operators’ payment website, hosted on Tor. In this case, the attackers demand a ransom of 1804 Bitcoin, equivalent to almost 35 million dollars.
A researcher managed to contact one of DoppelPaymer’s members, who confirmed that hackers infected Foxconn’s networks in North America in late November, although they did not attack the entire company. During the incident, attackers managed to infect nearly 1200 servers, stealing 100 GB of information and removing more than 20 TB of backups.
The company has not added additional details despite having received multiple requests for information. DoppelPaymer hackers have been linked to multiple recent security incidents, registering among their victims to organizations such as Petroleos Mexicanos (PEMEX), Compal, University of Newcastle, Banijay Group, among other public and private companies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
