The exploit information code for CVE-2022-32898 in iOS 16 was made public by a researcher. A security researcher by the name of Mohamed Ghannam (@ simo36) has made public the exploit code for a flaw in the iOS kernel that, if exploited, might allow an attacker to run arbitrary code while maintaining kernel privileges. The security flaw, logged as CVE-2022-32898 (CVSS 7.8), was found when analyzing how the Apple Neural Engine loads a model at the kernel level. A fix has been made available since the release of iOS 15.7 and iPadOS 15.7, iOS 16, macOS Ventura 13, and watchOS 9.
“While reverse-engineering the process of which the Apple Neural Engine loads a model in the kernel level, I identified two interesting memory corruption vulnerabilities in the code responsible for processing the neural network features in H11ANEIn::ANE_ProgramCreate_gated(). These kind of vulnerabilities, in my opinion, are easy to find when manually auditing the kernel driver, but nearly impossible to catch with fuzzers unless you build something incredibly sophisticated” said Mohamed in his blog.
If the vulnerability could be successfully exploited, the attacker would be able to run any code they wanted on the target machine with kernel privileges.
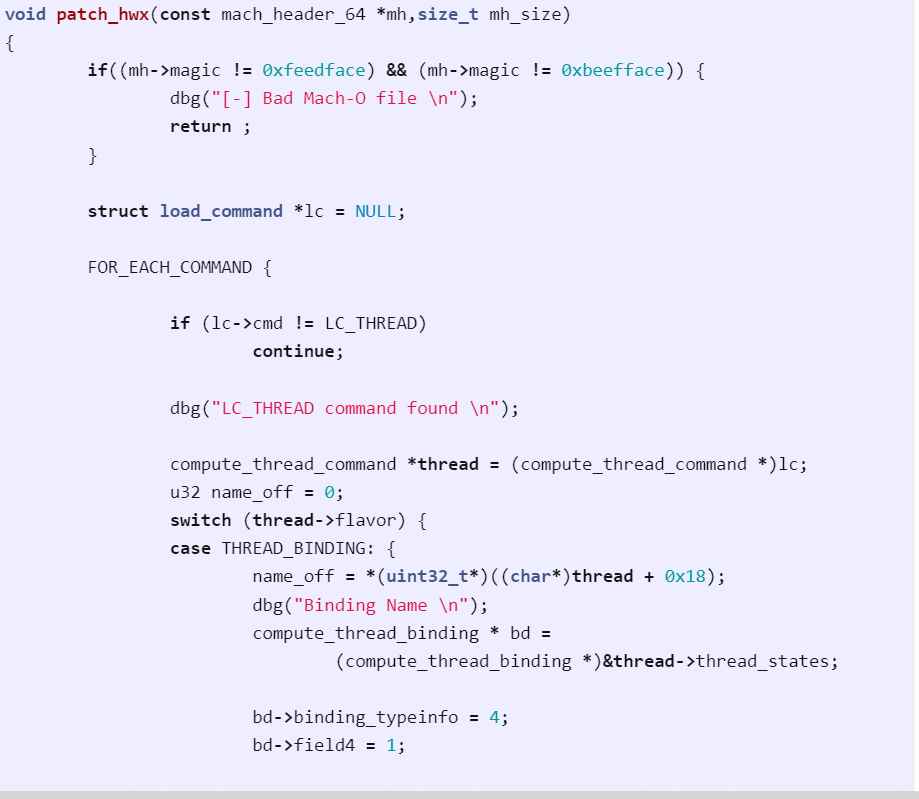
In iOS 16, Apple added certain validation checks to both susceptible routines to resolve CVE-2022-32898, reducing the provided plane count to four elements.
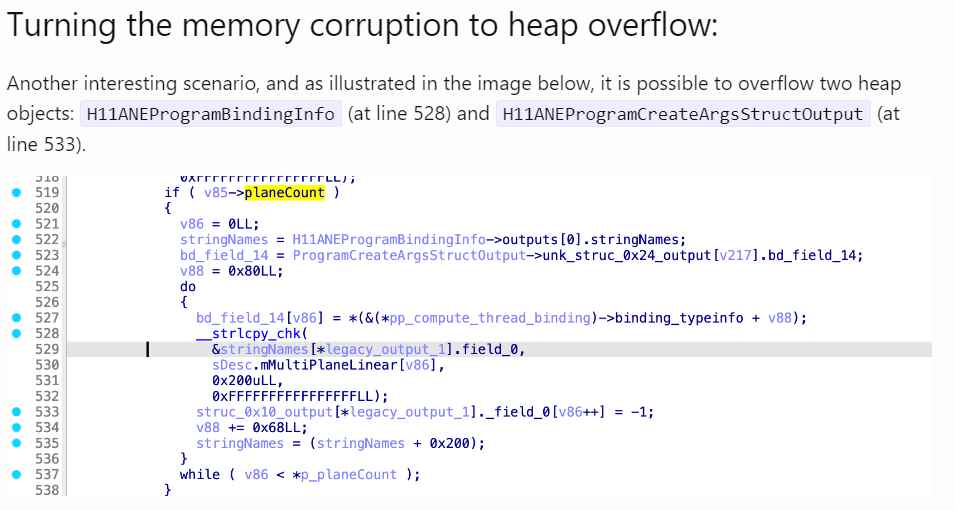
These flaws are intriguing because they don’t need the hacker to communicate with the kernel directly; in other words, he doesn’t need to establish a UserClient connection; instead, all he has to do is build (or create) a malicious model, load it, and then exploit it.
To reduce potential threats, users are advised to upgrade to the most recent version as soon as feasible.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
