Understanding the business impact of vulnerabilities is crucial in prioritization because it aligns the security efforts with the most critical assets and operations of the organization. This approach ensures that resources are allocated to address vulnerabilities that pose the greatest risk to the business’s core functions and objectives. Let’s delve into this concept with a real-world example:
Example: A Large Retail Corporation
Situation:
- A large retail corporation operates both physical stores and an online shopping platform. Their IT infrastructure is a mix of on-premises and cloud-based systems, handling everything from inventory management to customer data processing.
Vulnerability Identification:
- The security team identifies several vulnerabilities through regular scanning:
- A critical SQL injection vulnerability in their online shopping platform.
- A moderate-severity vulnerability in the employee email system.
- A low-severity issue in an internal tool used for scheduling staff shifts.
Business Impact Analysis:
- Online Shopping Platform Vulnerability:
- Impact: High. Exploiting this vulnerability could lead to a data breach, affecting customer trust and potentially resulting in significant financial losses due to fraud or regulatory fines.
- Business Criticality: The online platform is a major revenue source and crucial for customer engagement.
- Employee Email System Vulnerability:
- Impact: Moderate. While not directly affecting revenue, a breach here could lead to information leakage and operational disruptions.
- Business Criticality: Essential for internal communications but does not directly impact customer-facing services.
- Internal Scheduling Tool Vulnerability:
- Impact: Low. Exploitation might cause minor disruptions but is unlikely to result in significant business impact.
- Business Criticality: Low, as it’s an internal tool with no direct customer or revenue implications.
Prioritization Decision:
- The corporation prioritizes the patching of the online shopping platform vulnerability first, given its high business impact and direct relation to revenue and customer trust.
- The employee email system vulnerability is addressed next, considering its potential for operational disruption.
- The low-severity vulnerability in the internal scheduling tool is scheduled for a regular update cycle, as its business impact is minimal.
Outcome:
- By prioritizing the vulnerabilities based on their business impact, the corporation effectively mitigates the most significant risks to its operations. The critical vulnerability in the online shopping platform is addressed swiftly, preventing a possible data breach that could have resulted in substantial financial and reputational damage.
- This approach allowed the organization to efficiently allocate resources and efforts, ensuring the protection of key assets while maintaining normal business operations.
Real-World Effectiveness:
In real-world scenarios, organizations that align their security measures with business priorities are better positioned to handle threats effectively. By understanding which systems and data are most critical to their operations, they can make informed decisions on where to focus their security efforts. This not only optimizes the use of resources but also minimizes the potential impact of security incidents on the organization’s key operations and objectives.
Effective cloud security vulnerability prioritization is essential to maintain the integrity and safety of cloud-based systems. Here are key steps and strategies to achieve this:
- Risk Assessment: Begin with a thorough risk assessment. Identify all assets within the cloud environment and evaluate their criticality to your business operations. Understand the sensitivity of the data they handle and their exposure to potential threats. Example: A company evaluates its cloud-based customer database and identifies it as a high-value asset because it contains sensitive customer information. A breach in this database could result in significant financial and reputational damage.
- Vulnerability Identification: Continuously scan and monitor your cloud environment for vulnerabilities. This includes known vulnerabilities in software, configuration errors, and security misconfigurations. Example: An automated scan reveals an unpatched SQL injection vulnerability in a web application hosted in the cloud. This vulnerability could allow attackers to access or modify data in the database
- Threat Intelligence: Leverage threat intelligence to understand the current threat landscape. This involves staying informed about new vulnerabilities, exploits, and attack trends relevant to your cloud environment. Example: The security team subscribes to a threat intelligence service and learns about a new exploit targeting a specific version of a web server used in their cloud environment. They prioritize this information for immediate action.
- Prioritization Criteria: Develop a set of criteria for prioritizing vulnerabilities. Factors should include the severity of the vulnerability, the criticality of the affected system, the potential impact of an exploit, and the likelihood of an attack. Example: The company prioritizes vulnerabilities based on their severity rating (e.g., CVSS score), whether the vulnerability is public and being actively exploited, and the sensitivity of the data at risk.
- Automated Tools and Solutions: Utilize automated vulnerability scanning and management tools. These tools can help in continuously identifying and assessing vulnerabilities, thereby speeding up the prioritization process. Example: The company uses a cloud security posture management (CSPM) tool that continuously scans their cloud environments and automatically flags misconfigurations and vulnerabilities.
- Patch Management: Implement an effective patch management strategy. Prioritize patches for critical vulnerabilities, especially those that are being actively exploited in the wild. Example: The company uses a cloud security posture management (CSPM) tool that continuously scans their cloud environments and automatically flags misconfigurations and vulnerabilities.
- Customized Risk Scoring: Customize risk scoring models to your organization’s specific context. This involves considering factors unique to your business, such as specific regulatory requirements or industry-specific threats. Example: The company uses a cloud security posture management (CSPM) tool that continuously scans their cloud environments and automatically flags misconfigurations and vulnerabilities.
- Stakeholder Communication: Clearly communicate with relevant stakeholders about the vulnerabilities and the prioritization. This includes IT teams, security teams, and business leaders. Example: The IT department regularly reports to the executive team about the status of vulnerabilities in the cloud environment, emphasizing those that require urgent attention and potential business impact.
- Incident Response Planning: Prepare an incident response plan for vulnerabilities that can be exploited before a patch or mitigation can be applied. This plan should include steps for containment, eradication, and recovery. Example: The company has a predefined plan for incidents like a ransomware attack on their cloud servers, including immediate isolation of affected systems, communication protocols, and steps for data recovery.
- Continuous Improvement: Regularly review and update your vulnerability prioritization process. Learn from past incidents and adapt to evolving cloud architectures and emerging threats. Example: After experiencing a breach due to a misconfiguration, the company reviews and updates its cloud security policies and control implementation, learning from the incident to prevent similar occurrences.
- Training and Awareness: Ensure that your team is trained and aware of best practices in cloud security. Regular training and updates can significantly reduce the risk posed by human error or oversight. Example: The organization conducts regular training sessions for its developers on secure coding practices and cloud security best practices to minimize vulnerabilities in software they deploy to the cloud.
- Regulatory Compliance: Always align your vulnerability management practices with relevant regulatory requirements and industry standards to ensure compliance. Example: The organization conducts regular training sessions for its developers on secure coding practices and cloud security best practices to minimize vulnerabilities in software they deploy to the cloud.
Automated and Manual Systems for Vulnerability Prioritization
Automated systems for vulnerability prioritization offer several advantages over manual methods, particularly in addressing challenges related to scale, speed, and consistency. However, each approach has its own strengths and limitations. Let’s explore these in more detail:
Automated Systems for Vulnerability Prioritization
- Scalability: Automated systems can handle vast amounts of data and scan large networks efficiently, making them well-suited for organizations with extensive IT infrastructure.
- Speed: They provide near real-time identification and prioritization of vulnerabilities, which is crucial for timely responses to emerging threats.
- Consistency: Automation ensures a standardized approach to vulnerability assessment, reducing the risk of human error or oversight.
- Integration with Other Tools: Automated systems can be integrated with other security tools like threat intelligence platforms, enhancing the overall security posture.
- Resource Optimization: By automating routine tasks, they free up security personnel to focus on more complex and strategic activities.
Challenges Addressed
- Volume of Vulnerabilities: Manual methods struggle with the sheer volume of vulnerabilities in large systems. Automation can process and prioritize these at scale.
- Rapid Response: Automated systems can quickly identify and prioritize new vulnerabilities, a critical factor in fast-paced threat environments.
- Consistent Assessment: Manual assessments can be subjective and inconsistent. Automation applies uniform criteria to all vulnerabilities.
- Resource Allocation: Manual methods are resource-intensive. Automation allows for more efficient use of human resources.
Limitations of Automated Systems
- Contextual Understanding: Automated systems may lack the ability to fully understand the specific business context or the nuanced implications of a vulnerability on business operations.
- Over-reliance on Quantitative Metrics: Automation often relies on quantitative metrics like CVSS scores, which might not fully capture the unique risks to a specific organization.
- Potential for False Positives/Negatives: Automated tools might misclassify or overlook certain vulnerabilities, necessitating human oversight.
Manual Methods
- Deep Contextual Analysis: Manual prioritization can consider specific business contexts, regulatory requirements, and unique operational nuances.
- Expert Judgment: Experienced security professionals can apply their judgment to assess complex scenarios that automated tools might not accurately interpret.
Which is Better?
- Complementary Approach: The most effective strategy is often a combination of both. Automation can handle the heavy lifting of initial identification and basic prioritization, while human experts can refine this with insights based on business context and strategic considerations.
- Depends on Organization Size and Complexity: For smaller organizations with fewer assets, manual methods might suffice. In contrast, larger enterprises with more complex infrastructures will benefit significantly from automated systems.
In summary, while automated systems provide efficiency, scale, and speed, they are most effective when complemented by the nuanced understanding and strategic oversight that human expertise offers. The optimal approach depends on the specific needs, size, and complexity of the organization.
Formula for vulnerability prioritization
When building a formula for vulnerability prioritization, organizations should consider a range of factors that contribute to understanding the risk posed by each vulnerability. These factors not only help in assessing the severity of vulnerabilities but also guide the urgency and approach for remediation efforts. Here are key factors to consider:
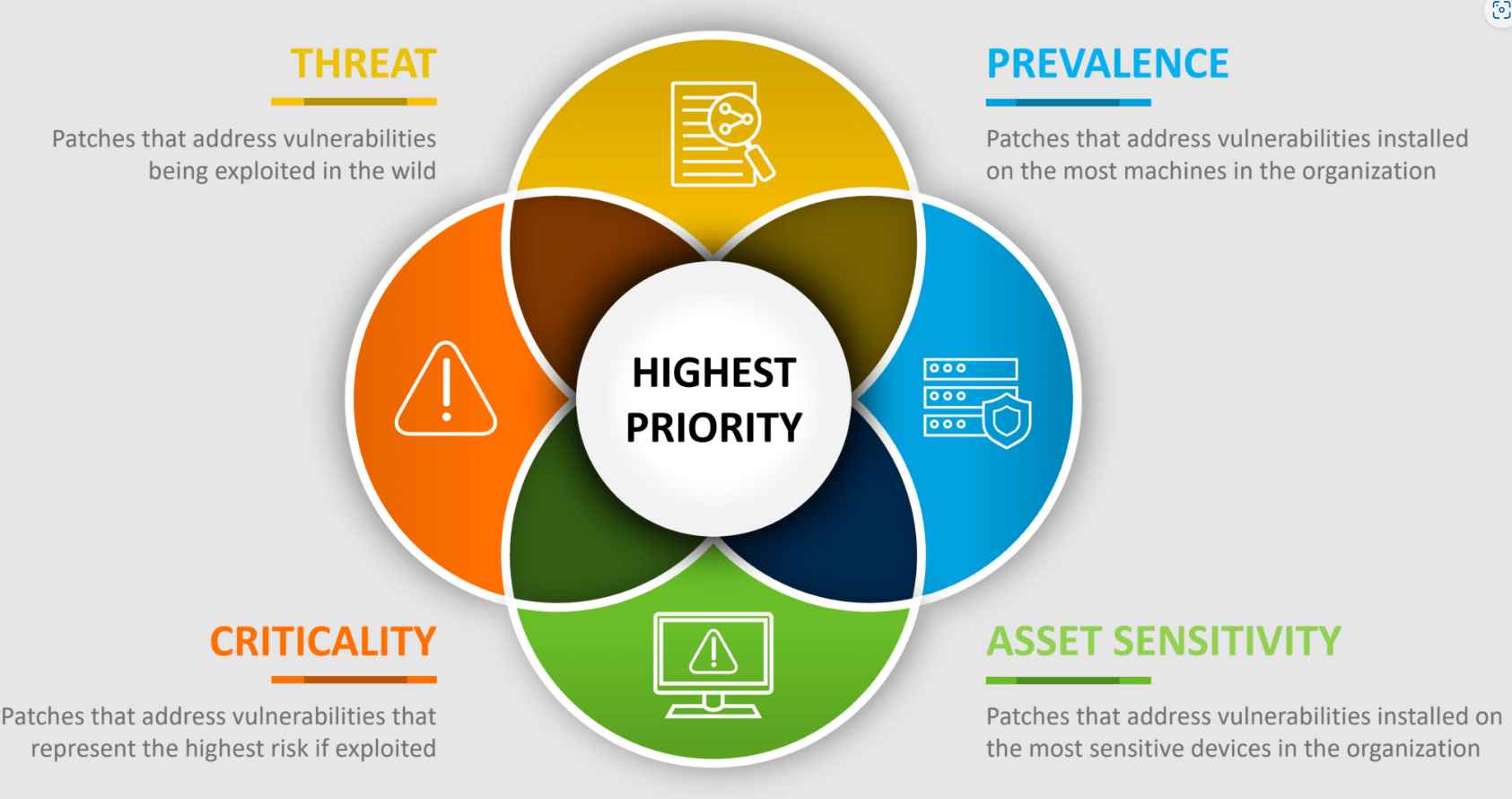
- Severity of the Vulnerability:
- Description: Based on metrics like the Common Vulnerability Scoring System (CVSS), this factor assesses the technical severity of the vulnerability.
- Interplay: Higher severity vulnerabilities typically require more urgent remediation.
- Exploitability:
- Description: Considers how easy it is for an attacker to exploit the vulnerability. Factors include the complexity of the exploit, whether it requires local or remote access, and if user interaction is needed.
- Interplay: Easier-to-exploit vulnerabilities might be prioritized for quicker remediation.
- Availability of Exploits:
- Description: Determines if an exploit is publicly available or being actively exploited in the wild.
- Interplay: Vulnerabilities with known exploits are often remediated urgently to reduce the window of opportunity for attackers.
- Business Criticality of the Affected Asset:
- Description: Assesses how important the affected system or data is to the organization’s operations.
- Interplay: Vulnerabilities in critical systems (like financial systems or customer databases) are prioritized higher.
- Data Sensitivity:
- Description: Evaluates the type of data involved and its sensitivity. For instance, vulnerabilities that affect systems holding personally identifiable information (PII) or intellectual property may be deemed more critical.
- Interplay: Higher sensitivity often translates to a higher priority for remediation.
- Compliance and Legal Implications:
- Description: Considers whether the vulnerability might lead to non-compliance with laws or industry regulations, potentially resulting in legal penalties or fines.
- Interplay: Compliance-related vulnerabilities might be prioritized to avoid legal repercussions.
- Potential Impact:
- Description: Evaluates the potential consequences of an exploit, such as data loss, service disruption, or financial loss.
- Interplay: The greater the potential impact, the higher the urgency for remediation.
- Remediation Cost and Complexity:
- Description: Assesses the resources needed to fix the vulnerability, including time, cost, and the potential for service disruption during remediation.
- Interplay: High-cost or complex fixes might be scheduled differently, but if the risk is high, they may still be prioritized.
- Public Perception and Reputation Impact:
- Description: Considers how public knowledge of an exploit might affect the organization’s reputation.
- Interplay: High reputational risk can increase the urgency of addressing a vulnerability.
- Patch Availability:
- Description: Determines if a patch or fix is readily available for the vulnerability.
- Interplay: Vulnerabilities with available patches may be remediated more quickly.
How These Factors Interplay:
In practice, these factors don’t operate in isolation but interplay in a dynamic way to guide prioritization:
- Balancing Act: Organizations often have to balance between the severity of the vulnerability and the criticality of the affected system. For instance, a high-severity vulnerability in a non-critical system might be prioritized lower than a medium-severity vulnerability in a critical system.
- Dynamic Prioritization: As new information emerges (like the release of a patch or the discovery of an exploit in the wild), the prioritization of vulnerabilities can change.
- Risk Thresholds: Organizations might set certain thresholds for action. For example, any vulnerability above a certain CVSS score or affecting a system with highly sensitive data might automatically be flagged for immediate action.
By considering these factors and understanding their interplay, organizations can develop a more nuanced and effective approach to vulnerability prioritization, ensuring that they are not just reacting to vulnerabilities, but doing so in a way that aligns with their overall risk management strategy and business objectives.
Example: A Financial Services Company
Scenario: A financial services company operates a complex IT infrastructure with various applications and databases, some of which handle sensitive customer financial data.
- Vulnerability Identified: A vulnerability is discovered in their online banking platform. Let’s break down the prioritization using key factors:
- Severity of the Vulnerability:
- Description: The vulnerability is rated 9.0 on the CVSS scale, indicating a high severity.
- Interplay: This high score elevates the priority for remediation.
- Exploitability:
- Description: The vulnerability can be exploited remotely without user interaction.
- Interplay: The ease of exploit increases the urgency for fixing it.
- Availability of Exploits:
- Description: There are no known exploits in the wild yet.
- Interplay: While the lack of active exploits slightly reduces immediate pressure, the high severity still demands quick action.
- Business Criticality of the Affected Asset:
- Description: The online banking platform is critical for customer transactions and operations.
- Interplay: The criticality of this platform increases the need for rapid response.
- Data Sensitivity:
- Description: The platform handles sensitive financial data.
- Interplay: The sensitivity of the data adds to the urgency due to potential risk of data breach.
- Compliance and Legal Implications:
- Description: The platform must comply with financial regulations like GDPR and PCI DSS.
- Interplay: Non-compliance risks add pressure for timely remediation to avoid legal penalties.
- Potential Impact:
- Description: A breach could lead to significant financial loss and customer data exposure.
- Interplay: The high potential impact drives a higher prioritization.
- Remediation Cost and Complexity:
- Description: The patch requires system downtime to implement.
- Interplay: Despite the downtime cost, the high risk necessitates immediate action.
- Public Perception and Reputation Impact:
- Description: A breach could severely damage customer trust and the company’s reputation.
- Interplay: This reputational risk adds to the urgency of addressing the vulnerability.
- Patch Availability:
- Description: A patch is readily available from the software vendor.
- Interplay: The availability of a patch enables immediate action.
- Severity of the Vulnerability:
- Decision and Action: Given the high severity, ease of exploitability, criticality of the system, sensitivity of the data, compliance requirements, and potential impact, the company decides to prioritize this vulnerability at the highest level. Despite the cost and complexity of remediation, the urgency is driven by the need to protect sensitive customer data, comply with regulations, and maintain customer trust. The patch is scheduled for immediate deployment during a time window that minimizes impact on customers.
- Outcome: The prompt action prevents any exploitation of the vulnerability, ensuring the security of customer data and maintaining regulatory compliance and customer trust.
In this example, the interplay of various factors, from technical severity to business impact, shapes the decision-making process. The company’s approach illustrates how an effective vulnerability prioritization strategy takes into account not just the technical aspects of a vulnerability but also its broader implications on business operations, legal compliance, and reputational risk. This holistic view is essential in managing cybersecurity risks in a way that aligns with business priorities and objectives.
In conclusion, effective vulnerability prioritization is a critical component of cybersecurity management, particularly in complex and dynamic IT environments. The key to successful prioritization lies in a comprehensive understanding of both the technical aspects of vulnerabilities and their broader business implications. Factors such as the severity of the vulnerability, exploitability, the criticality of affected assets, data sensitivity, compliance requirements, potential impact, remediation costs, public perception, and patch availability must all be considered in concert to determine the urgency and approach for remediation.
The interplay of these factors can significantly vary across different organizations and scenarios, as seen in the example of the financial services company. This complexity underscores the importance of a tailored approach that aligns cybersecurity efforts with an organization’s specific risk profile, operational needs, and strategic objectives.
By integrating automated tools with expert judgment, organizations can efficiently manage the large volume of vulnerabilities while also ensuring that the unique context of each vulnerability is appropriately considered. This balanced approach helps in effectively mitigating risks, maintaining regulatory compliance, protecting sensitive data, and upholding customer trust and organizational reputation. Ultimately, vulnerability prioritization is not just about addressing technical weaknesses but is a strategic function integral to the overall health and resilience of an organization.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
