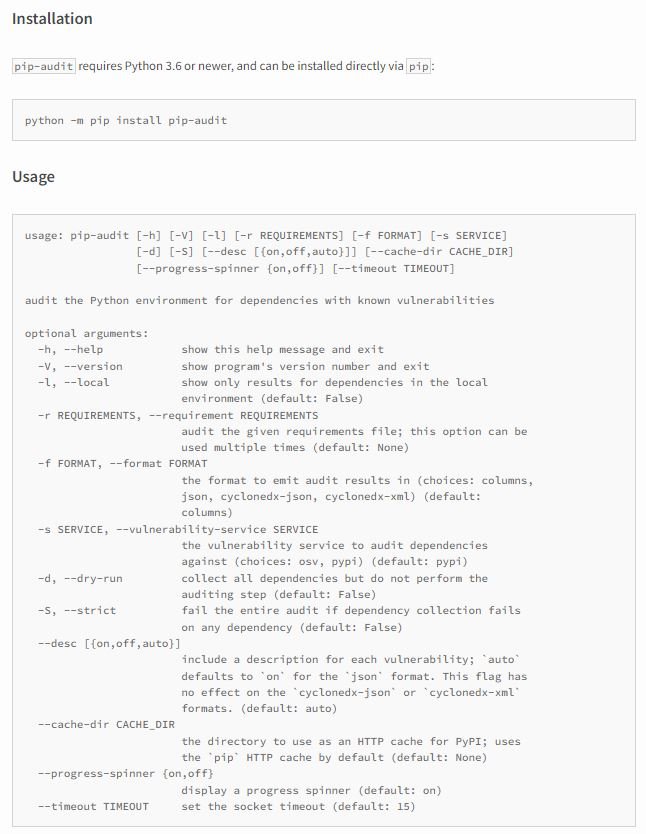
Pip-audit is a tool developed in collaboration with Google for scanning Python environments and detecting possible known security flaws. According to cybersecurity experts, Pip-audit uses the PyPi JSON API for the comparison of dependencies according to Python packaging data, in addition to resorting to large CVE databases, allowing users to audit dependencies for a quick finding of vulnerabilities.
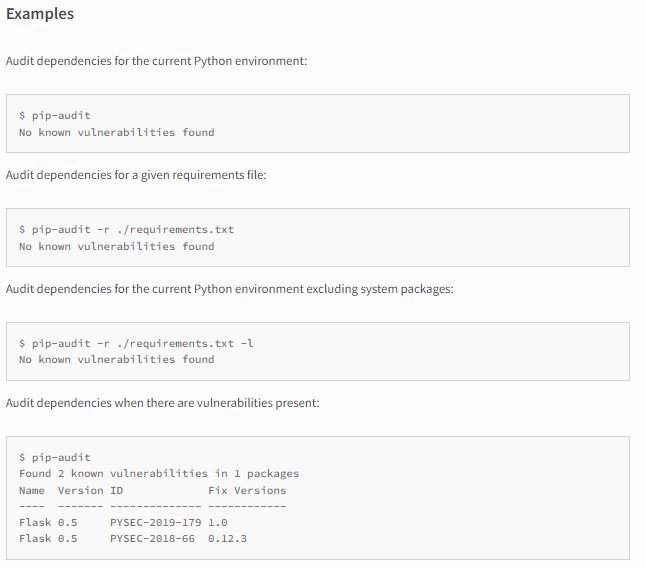
Dependency scanning can be configured based on the needs of users, whether they want to audit with system packages included or excluded from the scan, with or without CVE descriptions, and for a given requirements file. In addition, the scan results include package names, version IDs, fixed versions, and CVE descriptions.
This project, launched on December 1, was developed by William Woodruff and Alex Cameron from cybersecurity firm Trail of Bits, in collaboration with Google’s senior developer developer Dustin Ingram.
According to Woodruff, while there are multiple alternatives to Pip-audit, this project was developed with the idea of avoiding any financial or licensing commitments: “Tools like Snyk and Safety are great additions to the safety ecosystem, although both require a high level of paid subscription to function properly, something that is not available to all researchers.”
The developers also mention that their intention was for their tool to fit correctly into automated workflows, which would greatly facilitate multiple research processes. Finally, they wanted Pip-audit to eventually be integrated into pip: “Pip’s support guarantees and CLI design would have made adapting an earlier tool a serious task,” the developers explain.
Finally, the developers expressed their intention to create a high-quality tool that would consume the information of all the vulnerabilities known and added by PyPi, something that is not unknown to the cybersecurity industry but that is not available to everyone.
The Pip-audit project is one of many open source security initiatives backed by Google. Recently, the company sponsored security reviews of eight open source projects, in addition to collaborating with the National Institute of Standards and Technology (NIST) to create federal government guidelines for the acquisition of secure software, among other examples.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
