A couple of months ago Trustwave researchers detected a new variant of ransomware possibly developed by amateur hackers and based on other, more well-known malware variants. Identified as BlackByte, this variant of Windows-based ransomware is considered unusual.
This group of experts has already developed a decryption tool, available to any user on GitHub.
The researchers mention that the operators of this ransomware only attack systems that are not based on the Russian language and other languages of former Soviet regions, so they assume that the developers are of Russian origin. In addition, these hackers resort to the tactic of double extortion, in which they steal confidential information before encrypting the systems and thus force the payment of the ransom.
Despite the fact that hackers threaten to leak sensitive information if the victim refuses to pay the ransom, Trustwave analyzed some samples of BlackByte and determined that this malware does not have the functionality of data theft, so the threats are unfounded and only seek to generate fear in the victims. It should be noted that this malicious operation also has a dark web platform of leaks, although the information shared by that means does not seem to be legitimate.
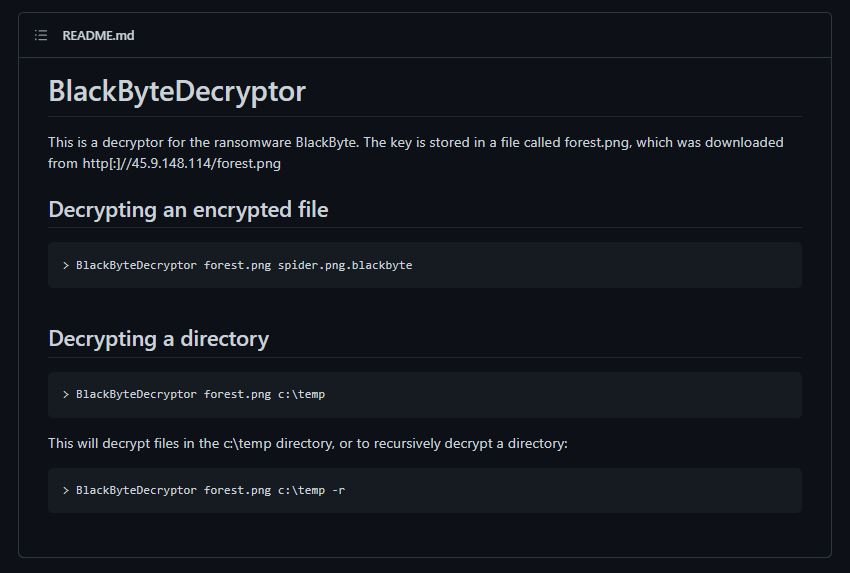
Moreover, the researchers also mentioned that the encryption process employed by BlackEye indicates the lack of experience of its developers, as the malware downloads and executes the same encryption key for files in AES instead of using unique keys for each session as occurs with the most dangerous ransomware operations. If the key cannot be downloaded from your HTTP server, it hides it in a file called forest. PNG, ransomware simply crashes. +
Experts mention that, in order to decrypt a file infected by BlackByte, users simply need to download the raw key from the host: “Whenever the file. PNG that was downloaded remains the same, we can use the same key to decrypt the encrypted files,” the report states.
Finally, experts mention that the ransomware runs in the memory of the affected system and is assigned a victim ID using data from the processor, which will be encoded and sent to the malware’s C&C server. Because any process that can prevent file encryption must be terminated the SetThreadExecutionState API is used to prevent the machine from entering a sleep state.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
