A Sophos security report details the finding of a new ransomware variant specifically targeting on-premises Microsoft Exchange servers without updating. Identified as “DearCry”, experts mention that this is an unsophisticated malware and apparently created by beginners or amateur hackers, although some successful attacks have been already identified.
The operators of this ransomware variant manage to infect the target systems by exploiting CVE-2021-26855, a flaw in proxy login on Exchange email servers; this was one of four zero-day vulnerabilities fixed by Microsoft on March 2. However, an undetermined number of Exchange deployments appear to be operating without the corresponding updates, which has allowed exploitation in the wild incidents.
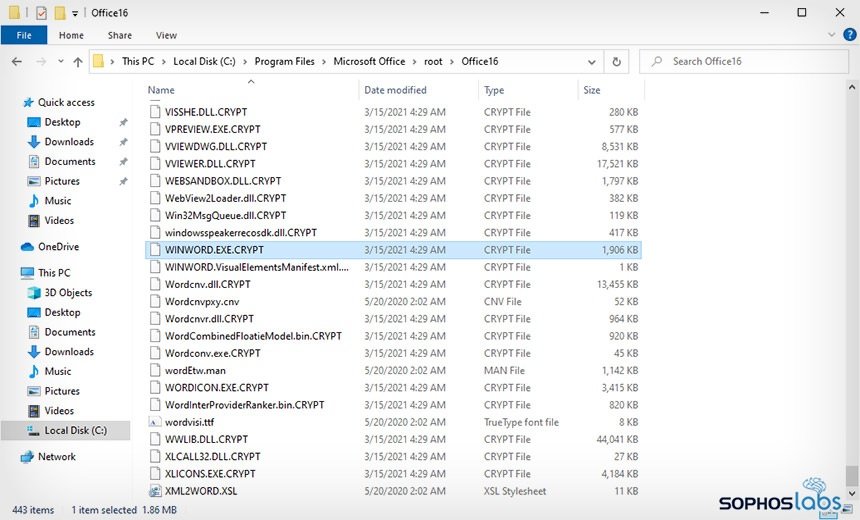
Although it has a wide attack range, DearCry’s main weakness is its poor coding. Experts believe that, in order to start the malicious campaign before the release of the updates, the developers decided to hasten the release of the malware, resulting in an imperfect version.
Mark Loman, Sophos researcher, says: “The creators of this malware seem to be releasing new binaries for new victims; this means that hackers should update their source code unusually quickly, possibly to fix code errors or add new functionality on the fly.”
Moreover, the expert mentions that DearCry uses an unusual approach to encrypting the infected system; to begin with, the malware creates an encrypted copy of the target file and subsequently tries to overwrite the original file using the previously created one. This is a significant difference from other ransomware variants like Ryuk, REvil or BitPaymer, although it is a practice similar to that of another dangerous malware variant: “The only known ransomware that employs a similar tactic is WannaCry, which caused severe damage worldwide a couple of years ago,” adds Loman.
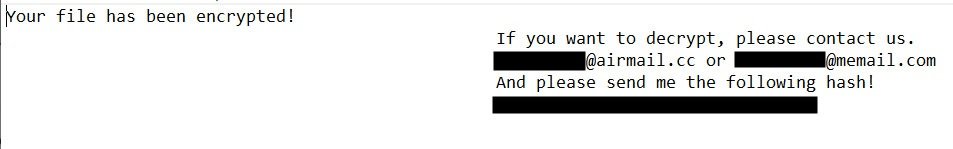
Still, the expert mentions that there is no evidence of any link between DearCry and WannaCry: “Beyond the use of hybrid approach and being designed to exploit a specific flaw, there are notable differences between the two variants; for example, DearCry uses an RSA encryption key, but does not use a C&C server and is not able to deploy over the infected network.”
The risk of exploitation remains active, so some government agencies have already begun to take action on the matter. For example, the UK National Cyber Security Centre issued a security alert inviting users from affected deployments to install security patches as soon as possible: “Organizations running an unsupported version of Exchange Server must upgrade to a supported version as soon as possible. Remember that Exchange Online, as part of Microsoft 365, is not affected.”
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
