A group of threat actors is deploying a fraudulent scheme targeting users of the popular Twitch streaming platform. According to Group-IB specialists, scammers are creating profiles identical to those of some streamers in order to deceive victims and extract their personal and financial information.
Such platforms have experienced an unusual increase in popularity since restrictions began to limit the spread of coronavirus. In the case of Twitch, the average number of users increased by an average of 1.5 million, which has also meant an increase in profits for streamers. However, this increase in popularity attracted the attention of cybercriminals.
In this fraudulent scheme cybercriminals look for popular channels on the platform to create a cloned account that is practically the same as the original. Scammers even download full streams from the original channel though by inserting their own banner, which can fool any user. In the material embedded by the attackers, potential victims are offered the possibility to enter a sweepstakes or invest in a business with unrealistic yields.
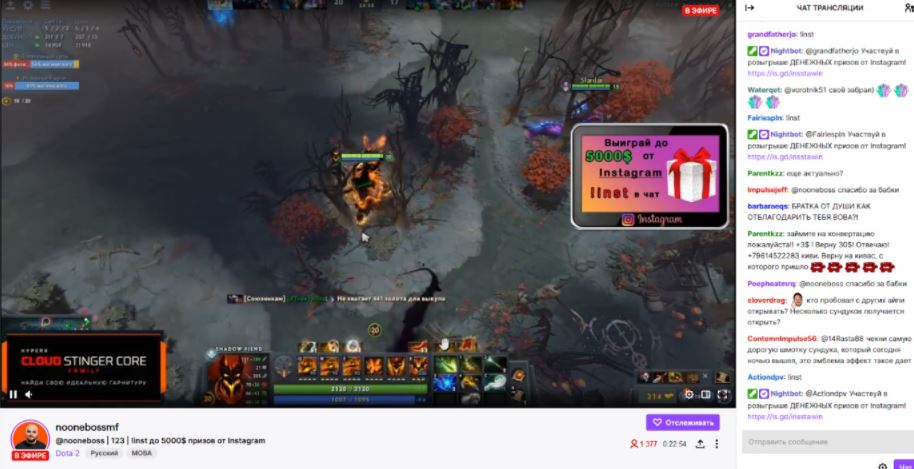
As Group-IB experts pointed out, cybercriminals post a special command in chat, sending users who click on the banner to a fraudulent website (https://winstainq[.]Dub/draw).
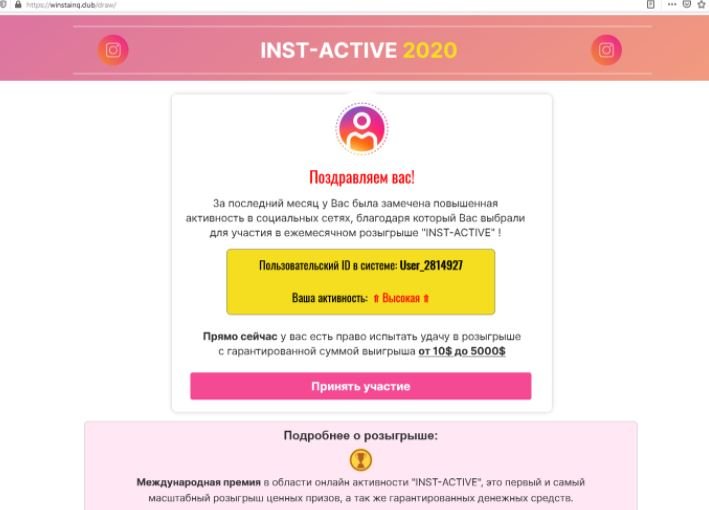
On this website the victim is offered a payment of up to 5 thousand dollars, requesting in return a commission for services that must be covered by sharing the details of his payment card (number, expiration date, security key). If users fall into the trap, threat actors will fully seize their credit cards. Criminals even post reviews of fake winners of these prizes, adding a little more credibility to the trap.
Users of streaming platforms, e-commerce sites, social media and any other online resources are requested not to share their information with anyone, as in many cases scammers will always be vigilant to steal their information.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
