The Common Weakness Enumeration team has just announced the publication of a list titled 2023’s Top 25 Most Dangerous Software Weaknesses. This year’s CWE Top 25 vulnerabilities include cross-site scripting (XSS), SQL injection, and out-of-bounds writes, all of which were included last year as well.
The CWE Top 25 is comprised of software issues that have been chosen for inclusion based on their prevalence as well as their capacity to inflict harm. Attackers “can often exploit these vulnerabilities to take control of an affected system, obtain sensitive information, or cause a Denial-of-Service condition,” the Cybersecurity and Infrastructure Agency stated in its announcement of the availability of the vulnerability patch.
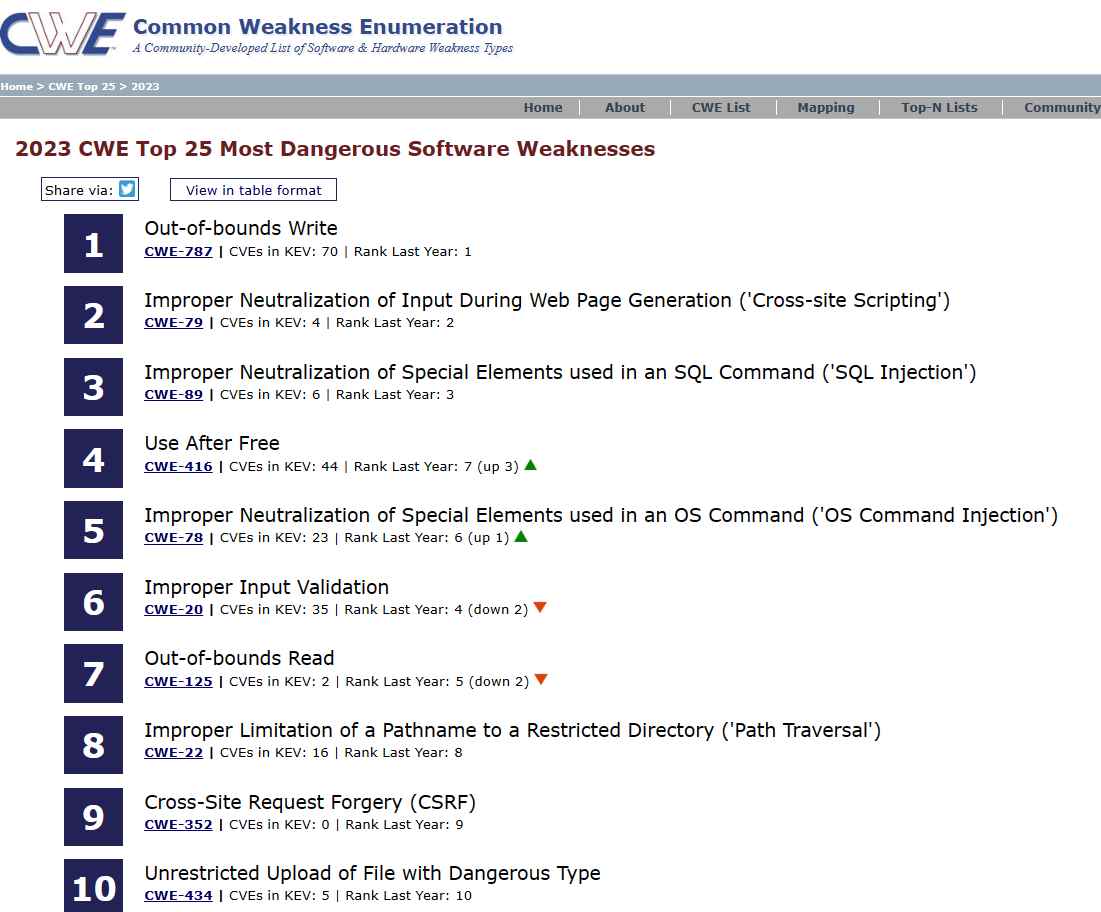
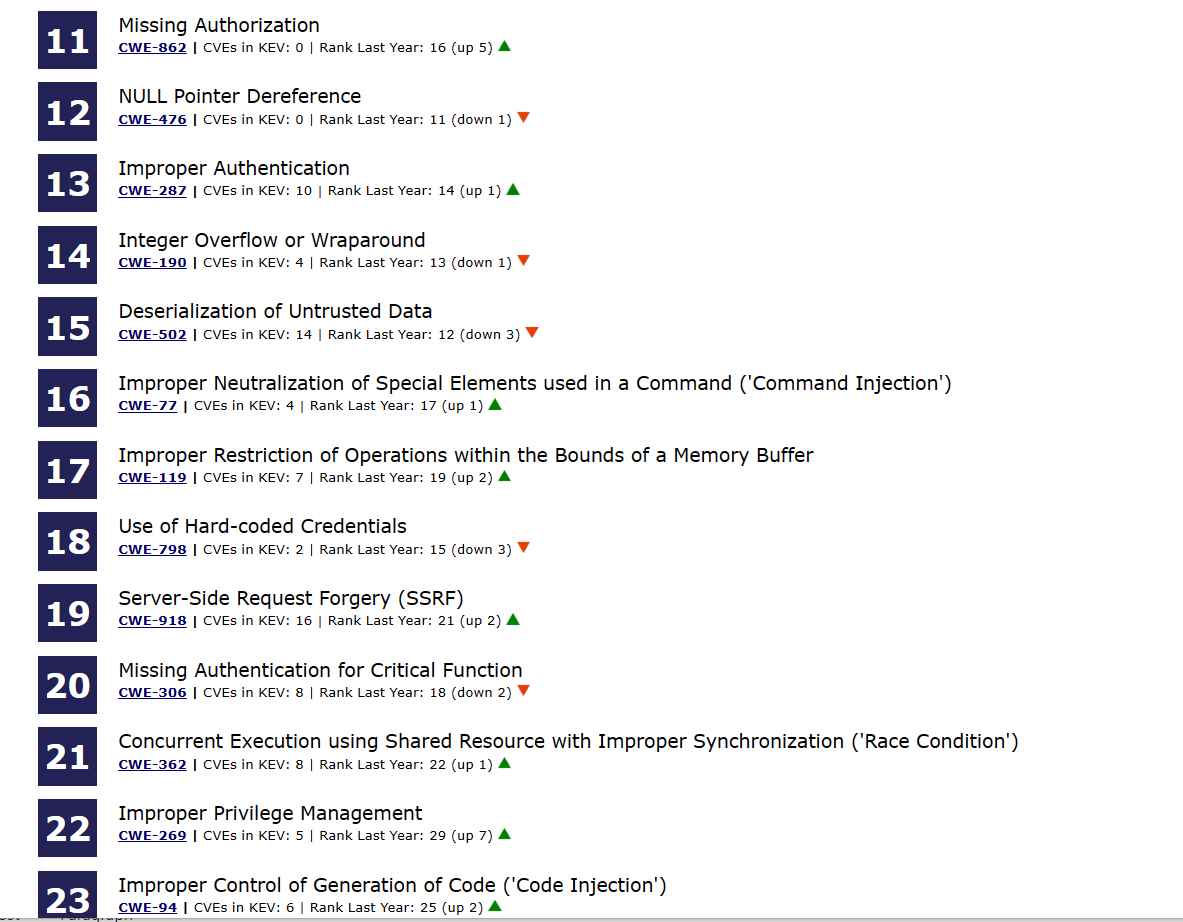
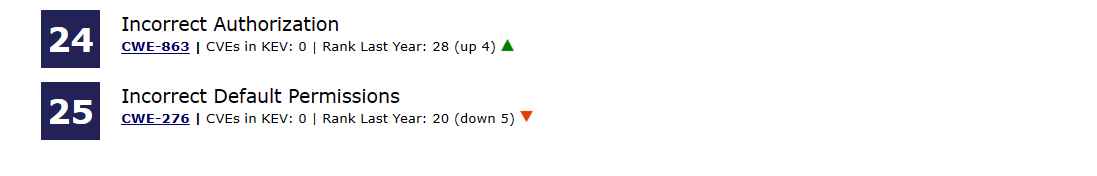
After analyzing 43,996 CVE entries from NIST’s National Vulnerability Database (NVD) for vulnerabilities discovered and reported across 2021 and 2022, with a focus on CVE records added to CISA’s Known Exploited Vulnerabilities (KEV) catalog, MITRE assigned a score to each vulnerability based on its severity and prevalence in order to compile this list. The CVE entries were analyzed for vulnerabilities discovered and reported across 2021 and 2022. The severity and frequency of software flaws are assessed, and the results of those ratings are used to decide where the vulnerabilities fit on the list.
SQL injection came in third place, behind out-of-bounds writes and cross-site scripting, which have occupied the top two slots on the list .
This year a thorough collection of the top 15 vulnerabilities that were regularly exploited in attacks over the whole year was made public as the result of a joint effort by cybersecurity authorities from across the globe. The National Security Agency and the Federal Bureau of Investigation were both participants in this collaborative project.
In addition, the Cyber Intelligence Sharing and Analysis Center (CISA) and the Federal Bureau of Investigation (FBI), in collaboration with the Australian Cyber Security Centre (ACSC) and the National Cyber Security Centre (NCSC) of the United Kingdom, revealed a list of vulnerabilities that are commonly exploited.
CISA and the FBI have collaborated to compile a list of the top 10 security vulnerabilities that have been targeted the most often from 2016 through 2019.
In their examination of the changes that have occurred this year, the CWE team made the following observation: “As with previous years, there is a continued transition in the Top 25 to more specific base-level weaknesses,” and it added that there has also been “a slow decline in the number of unique class-level weaknesses.”
Base-level vulnerabilities are stated in sufficient depth to identify precise detection and avoidance strategies, while class-level problems are very high level and often aren’t tied to a particular language or technology. The CWE program thinks that by placing a greater focus on base-level vulnerabilities in the CWE Top 25, it will be easier for software professionals to find specific strategies to reduce their exposure to cyber risk.
The CWE team said that the program’s objective is to help users who are striving to better understand and manage the problems that provide a more immediate operational danger to today’s systems. When compared to higher, class-level vulnerabilities, “weaknesses at the base level are more informative and conducive to practical mitigation.”
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
