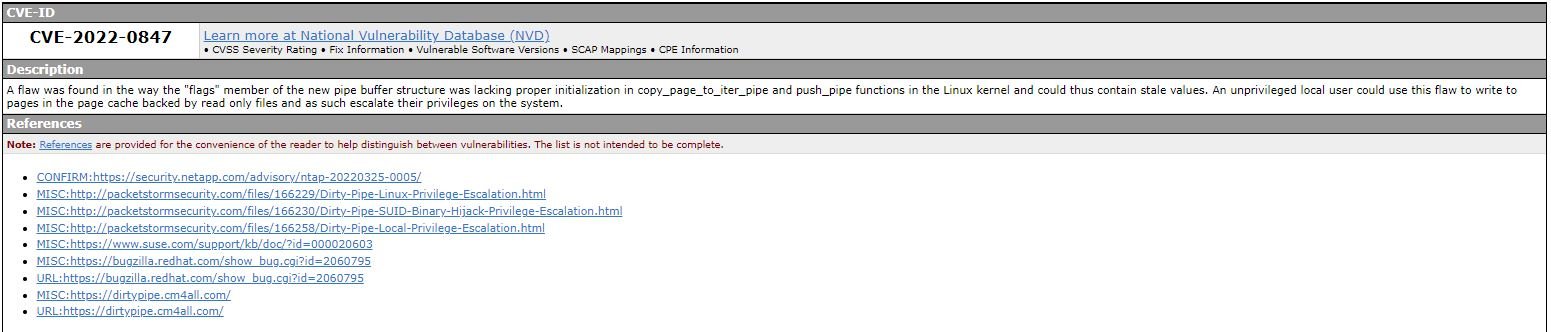
Cybersecurity specialists report the detection of a new Linux vulnerability that also impacts Android 12 devices, including Samsung Galaxy S22 and Google Pixel 6 smartphones. Tracked as CVE-2022-0847 and also known as Dirty Pipe, this flaw could cause severe damage to vulnerable implementations.
The flaw was discovered by security researcher Max Kellermann, who mentions that any application that can read files on a vulnerable device could make arbitrary modifications and even execute malicious code. The attack has been demonstrated on some laptops with Linux operating system, although its ease of exploitation on Android devices has yet to be determined.
It should be remembered that the reading of files in the system is a permission requested by most Android applications, so this failure represents a considerable potential risk.
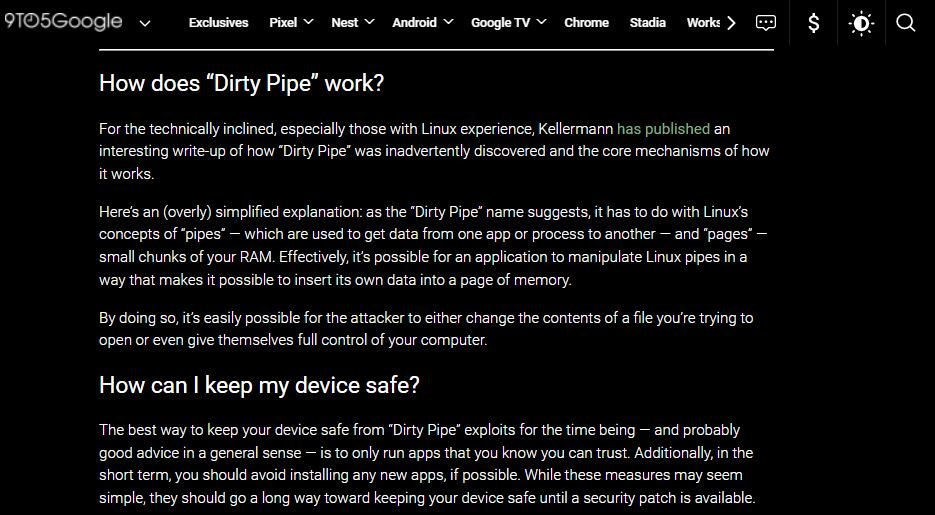
The scope of Dirty Pipe is not limited to computer equipment and smartphones with Linux, but could impact other implementations such as Google Chromecast, smart speakers, screens and other Internet of Things (IoT) devices. The vulnerability was introduced with version 5.8 of the Linux kernel, remaining unnoticed for nearly two years.
Although this is a considerable security risk, mobile security specialist Ron Amadeo specifies that only devices that were released with Android 12 system could be affected, so previous versions of the Linux kernel present on previous devices are not at risk.
For now there are no known cases of active exploitation of this flaw, although the cybersecurity community has already created dozens of proofs of concept (PoC), demonstrating that the exploitation of Dirty Pipe is relatively trivial. A recently released video shows how the vulnerability allows root access to Pixel 6 and Galaxy S22 devices using a specially crafted app.
Considering this, many experts believe that it is only a matter of time before attempts at exploitation begin to be reported in real scenarios.
In this regard, Google has just released a patch for Pixel 6 devices and other smartphones in the line. However, reports and security updates for Android make no mention of Dirty Pipe, so patches to address this flaw on mobile devices could take until next month.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
