Cisco security teams announced the release of 33 security updates to fix critical flaws. Critical vulnerabilities include two remote code execution flaws (CVE-2020-3323 and CVE-2020-3321), an authentication bypass (CVE-2 020-3144), a privilege escalation (CVE-2020-3140) and a default credential error (CVE-2020-3330).
Affected devices include multiple RV series router models, RV110W series VPN firewall, and Cisco Prime license manager. Detected flaws can lead to multiple problems, such as turning the device unable to resolve its core functions: keeping unauthorized users out of protected networks.
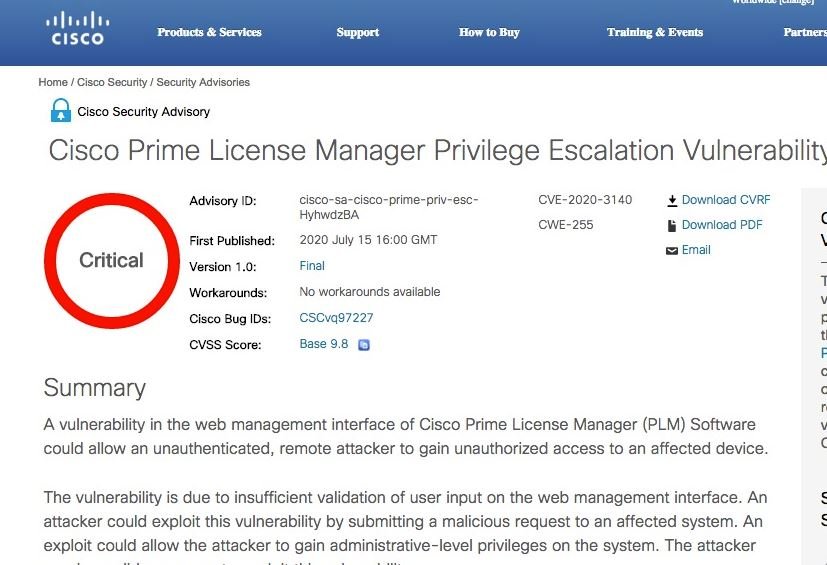
In addition to critical flaws, the company released fixes for 11 other vulnerabilities considered high security, including:
- CVE-2020-3180: static credentials
- CVE-2020-3351: denial of service (DoS)
- CVE-2020-3385: denial of service (DoS)
- CVE-2020-3387: Remote code execution
- CVE-2020-3381: directory climbs
- CVE-2020-3369: denial of service (DoS)
- CVE-2020-3388: command injection
Other minor severity flaws include errors that allow threat actors to execute code remotely, deploy denial of service (DoS) attacks, which affect VR routers.
The remaining 15 patches will be applied for low security bug fixes in solutions such as WebEx, SD-WAN, and Datacenter Manager. Cisco recommends that affected deployment administrators install updates as soon as possible. So far no attempts at exploitation have been reported in real-world scenarios.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
