Advantech, a major manufacturer of industrial automation and Internet of Things (IoT) chips, has confirmed a ransomware attack on its networks that resulted in the theft of low-priority sensitive information. This was made known by the company through a statement.
A group of cybersecurity specialists claims that Conti ransomware operators are behind this attack, demanding around $14 million to restore the company’s systems to normal. Advantech is a world leader in its field, exceling in the manufacture of network devices, IoT equipment, servers for the medical industry, among other solutions.
Cybercriminals demand 750 Bitcoin (about $12.6 million) to remove encryption from the company’s networks and remove stolen data from its servers. Conti operators even offered to remove encryption from some of the compromised files to prove that their tool actually works. Subsequently, hackers threaten to disclose compromised information if their demands are not met within a certain time frame.
A few days ago, hackers leaked some samples of this information on their website, starting with 2% of the information compromised in a ZIP file. Still, the ransomware operators ensure that if the ransom is paid shortly they will remove the backdoors installed on Avantech’s networks so that the company does not suffer similar attacks again.
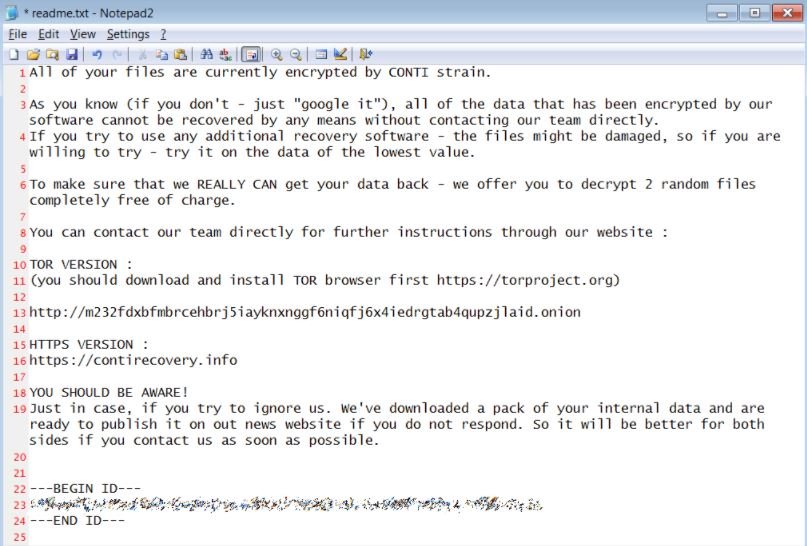
Although the company initially refused to make statements, a screenshot with the ransom note sent by the hackers began to be posted on various specialized platforms, so eventually Avantech’s executives decided to acknowledge the incident. A statement signed by the company’s spokesman confirms the ransomware attack although no further details are given: “Some measures have been implemented to contain the infection. We activate and update our computer security and protection mechanisms.”
The Conti ransomware was first detected in isolated incidents in late December 2019, taking up activities in mid-2020. This ransomware shares code with the popular Ryuk ransomware and began to be distributed via reverse shells opened by the TrickBot Trojan after Ryuk’s activity decreased in July 2020.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
