A few hours ago, a leak of an unfinished version of Windows Core Polaris was reported, proving that Microsoft was working on a version of its operating system specifically designed for low-performance devices. A long time ago the company developed a modular version of the Windows system using the code name “Windows Core OS”, designed to work on smartphones, electronic tablets, dual-screen PCs and other devices.
There are two versions of the system created from Windows Core OS:
- Andromeda, designed for mobile devices
- Polaris, available for traditional laptops
The latter would have been done in order to remove legacy Windows elements, such as Control Panel, in addition to replacing Windows 10 in S mode.
This time, Microsoft Polaris version 16299, created in 2018, was leaked, although it does not include shell or Windows applications: “This edition of the OS was designed for desktops and laptops; this is an early picture and does not include much more than the characteristics of the operating system,” a report on the leak mentions.
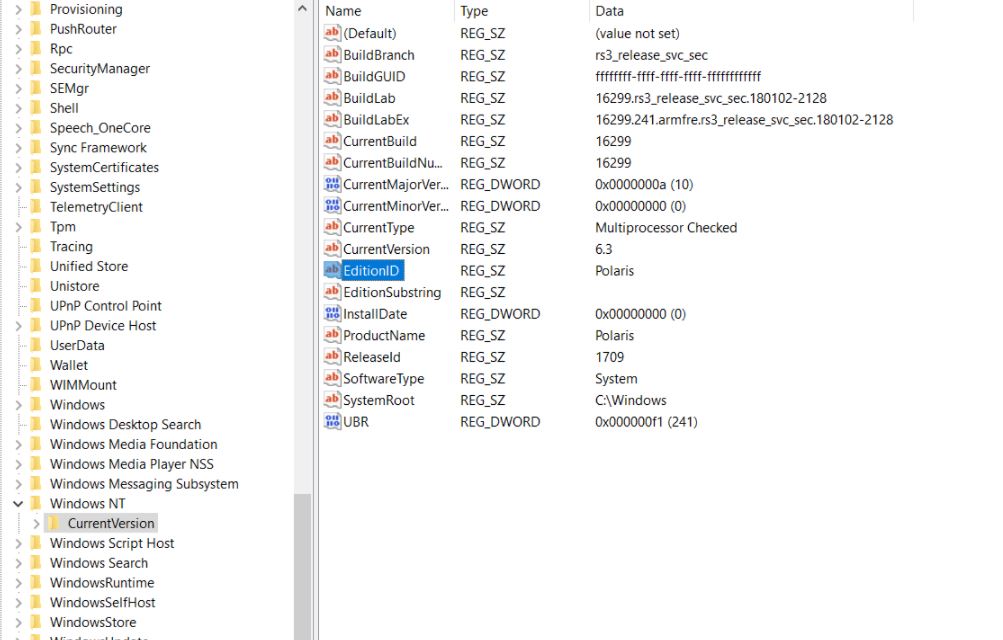
The Scamdisk hacker, responsible for the leak, also notes that an ARM device is required to boot this version, plus the drivers must be downloaded before the first boot: “It is possible to boot the wim, although you must also install it directly”, adds Scamdisk.
As mentioned above, the build was developed in 2018, when Microsoft shifted its focus to Windows Lite/Santorini (now called Windows 10X). Scamdisk has a well reputation as leaker in the hacking community; they has previously leaked sensitive versions of other Microsoft systems, including Windows 7, 8, 10, and Windows Server.
The company canceled this project to start working on Windows 10X, a new SKU that could work on lower-performance devices. Microsoft had already replaced Andromeda with Android on its Surface Duo, and now Polaris has been replaced by Windows 10X. Windows 10X is expected to be released in the first quarter of 2021, and will target casual users with a new UWP version of File Explorer.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
