Cybersecurity specialists identified a hacker known as “Tortilla” launching powerful ProxyShell cyberattacks against Microsoft Exchange implementations in order to inject the Babuk ransomware variant into the affected systems. The report was submitted by Cisco Talos in mid-October.
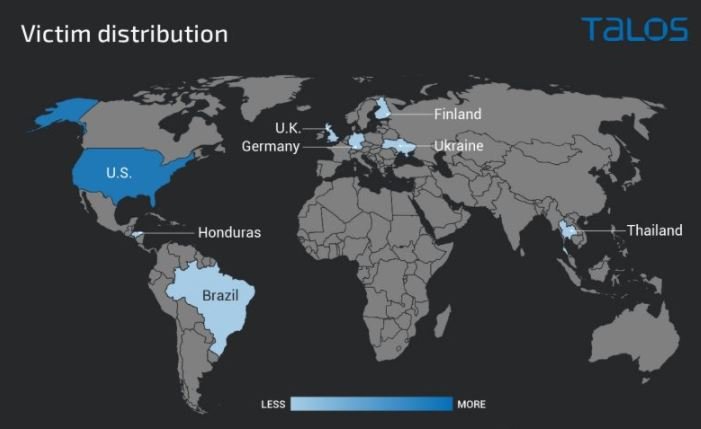
According to experts, the hacker has been active since at least the middle of this year and mainly attacks victims in the U.S., although it has also been detected in Brazil, Honduras, Thailand, Ukraine, the United Kingdom and other countries.
Tortilla has also been identified using other payloads, including PowerCat, a PowerShell-based netcat clone.
As some users will recall, ProxyShell is a set of vulnerabilities whose exploitation would allow threat actors to deploy a remote code execution attack and extract passwords in plain text. Cisco Talos experts note that the threat actor is using an unusual infection chain technique, based on an intermediate unpacking module housed in a clone pastebin.pl in order to deliver Babuk’s payload.
As shown below, Tortilla uses a DLL or .NET executable file to enter the target system, running as a background process to inadvertently invoke the malicious execution shell.
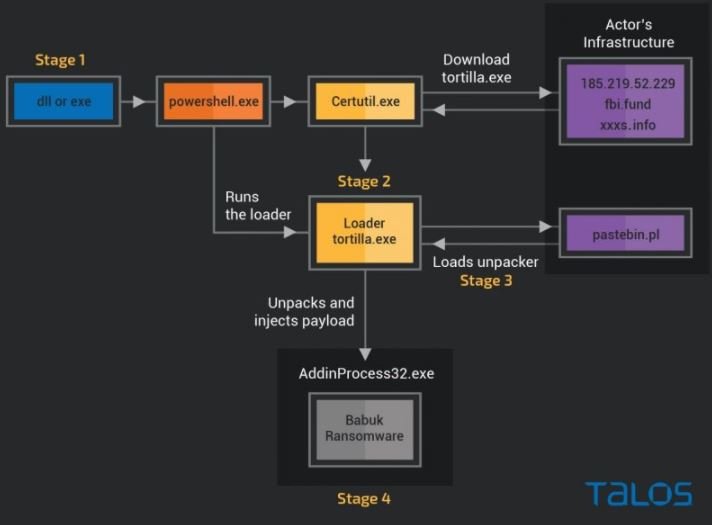
According to experts, the uploader downloads an intermediate stage of unpacking from the PasteBin cloning site pastebin.pl, a site that appears unrelated to the popular pastebin.com. The unpacker concatenates the bitmap images embedded in the Trojan’s resources section and decrypts the payload into memory and then the payload is injected into the AddInProcess32 process and used to encrypt files on the compromised server.
In addition to this site pastebin.pl, Tortilla also uses a Unix-based download server that while considered legitimate, researchers have identified various malicious campaigns linked to it.
The worst part of it all is that Babuk’s recently released decryption tool doesn’t work with this new iteration of the malware, so at the moment victims have no choice but to negotiate with hackers or reset their systems from their backups. Microsoft shared some security guidelines that Administrators of Exchange deployments can follow to protect their systems from this attack variant.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
