CWE Top 25 Most Dangerous Software vulnerabilities for 2023
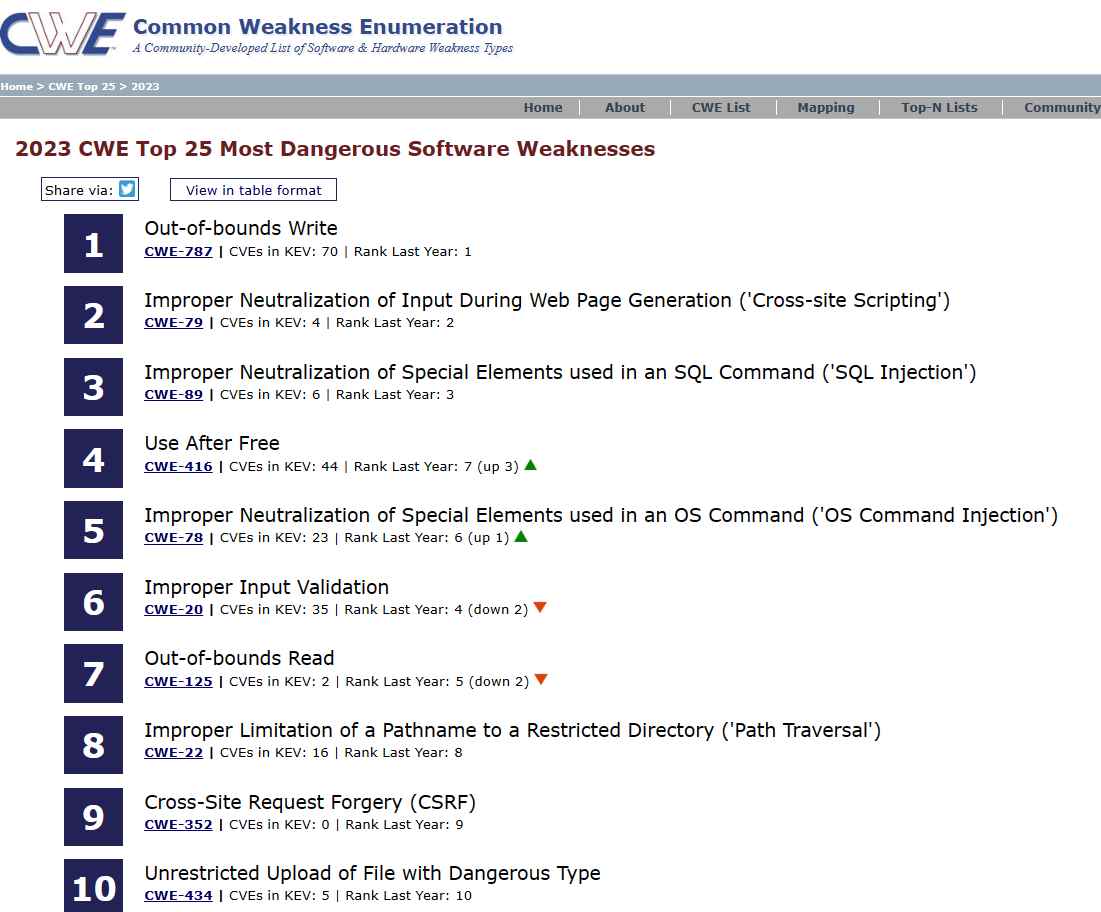
The Common Weakness Enumeration team has just announced the publication of a list titled 2023’s Top 25 Most Dangerous Software Weaknesses. This year’s CWE Top 25 vulnerabilities include cross-site scriptingRead More →