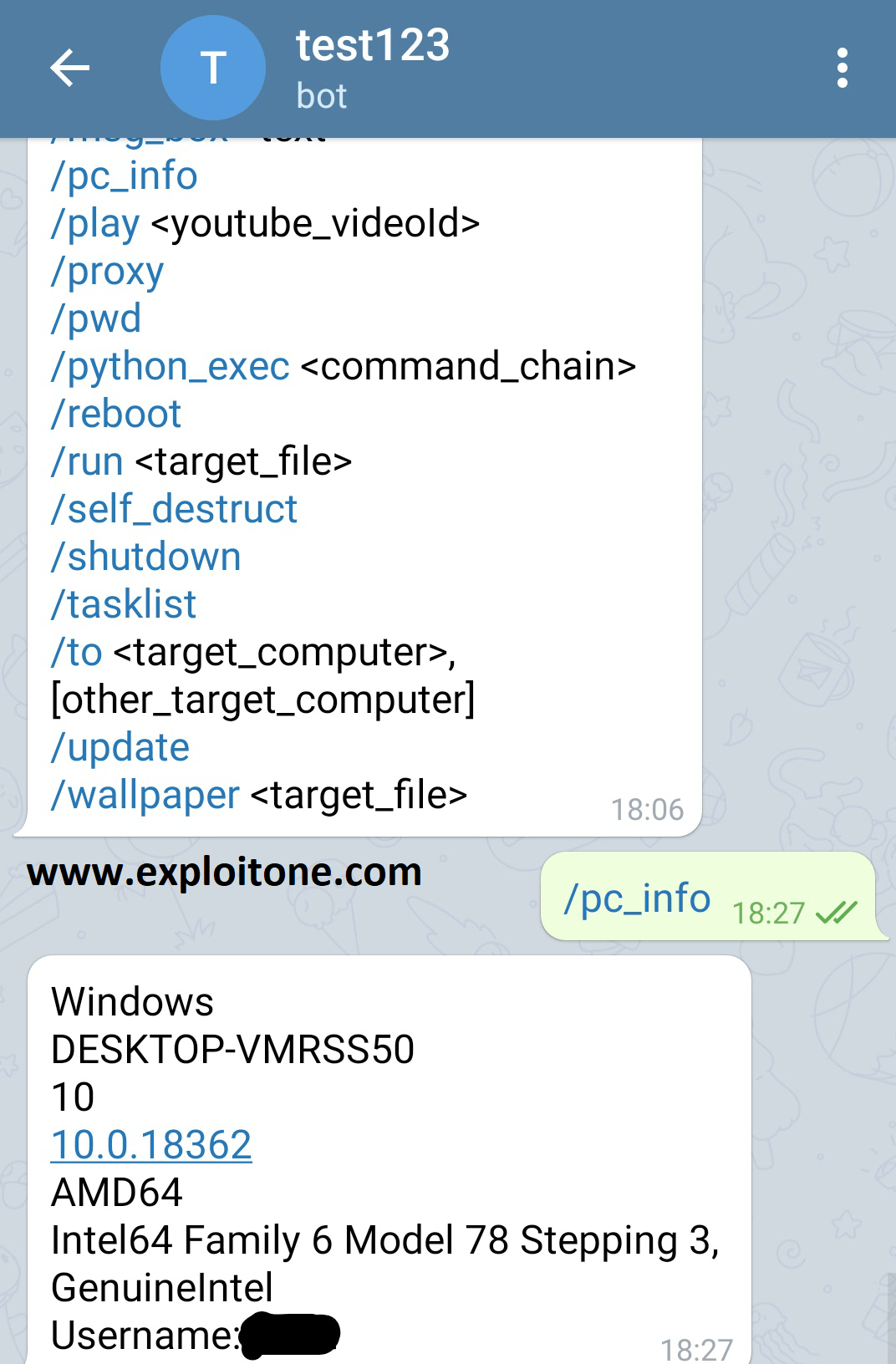
Foreign intelligence agents are using videoconferencing apps to spy on Americans
We all know that the Coronavirus Outbreak has forced all the officials whether they are from government agencies or from the private firms to work from home. Thus, to getRead More →