In recent times, the cybersecurity landscape has witnessed a significant uptick in the exploitation of misconfigured servers across various platforms, including YARN (Yet Another Resource Negotiator), Docker, Confluence, and Redis. Hackers have been leveraging these vulnerabilities to carry out crypto mining operations unlawfully. This article delves into the intricacies of these attacks, exploring the nature of the vulnerabilities, the modus operandi of the attackers, the implications for businesses and individual users, and the measures that can be taken to mitigate such risks.
Understanding the Vulnerabilities
The vulnerabilities exploited by hackers primarily stem from misconfigurations in the server setups of YARN, Docker, Confluence, and Redis. These misconfigurations often occur due to oversight or lack of awareness about security best practices among administrators. For instance, Docker containers might be deployed with default settings without adequate access controls, or Redis databases may be left accessible without password protection.
YARN, a key component of the Apache Hadoop ecosystem, is designed to manage computing resources in clusters and facilitate the execution of distributed applications. When misconfigured, YARN can allow unauthorized access to the cluster, enabling attackers to deploy their own applications, such as crypto mining software.
Docker, a popular containerization platform, can be exploited if containers are run with excessive permissions or if the Docker daemon is exposed to the internet without authentication. Similarly, Confluence, a widely used team collaboration software, and Redis, an in-memory database, become vulnerable when not properly secured, providing attackers with opportunities to inject malicious scripts or commands.
The Modus Operandi of Attackers
Attackers exploit these vulnerabilities by scanning the internet for exposed or misconfigured servers. Upon identifying a vulnerable server, they deploy crypto mining malware, which uses the server’s computing resources to mine cryptocurrencies like Bitcoin or Monero. This process is often automated using scripts that exploit known vulnerabilities or default credentials to gain access.
The crypto mining software operates silently in the background, making it difficult for administrators to detect its presence. The only noticeable effect might be a degradation in performance or an unusual increase in electricity consumption. However, by the time these symptoms are noticed, the attackers may have already mined significant amounts of cryptocurrency.
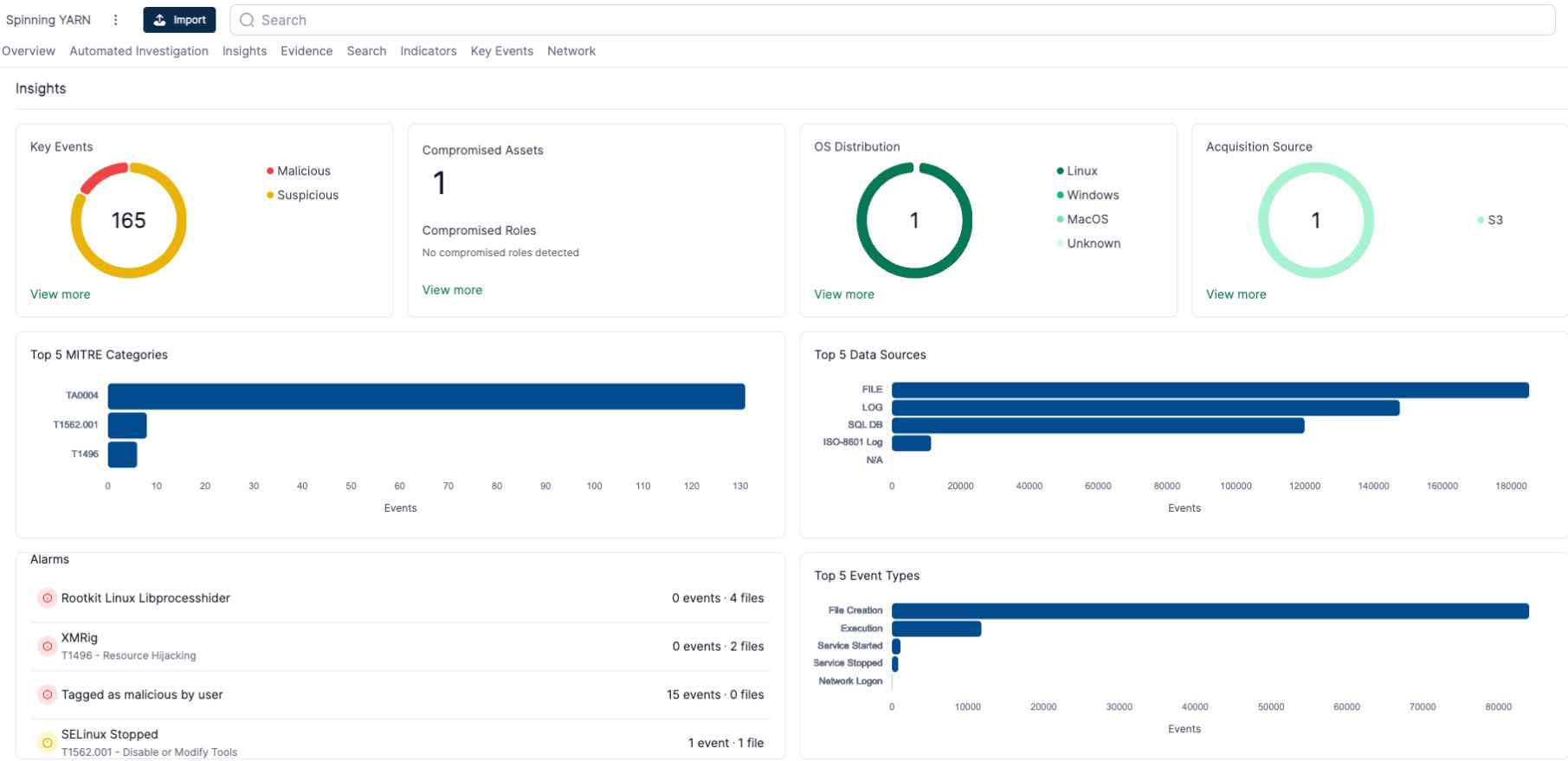
Malware Campaign Overview
The attackers behind this campaign have developed a sophisticated mechanism to exploit common misconfigurations and known vulnerabilities, such as CVE-2022-26134 in Confluence, to conduct Remote Code Execution (RCE) attacks. The initial access is usually achieved through Docker Engine API honeypots, where attackers spawn a new container based on Alpine Linux, creating a bind mount to write files directly to the underlying host. This method is exploited to execute a series of base64-encoded shell commands, ultimately leading to the deployment of a cryptocurrency miner, spawning a reverse shell, and enabling persistent access to the compromised hosts.
Unique Payloads and Techniques
The campaign utilizes four novel Golang payloads designed to automate the identification and exploitation of the targeted services. These payloads serve as tools for issuing exploit code and infecting new hosts by taking advantage of misconfigurations and exploiting the n-day vulnerability in Confluence for RCE attacks.
For Docker compromises, attackers spawn a container and escape from it onto the underlying host. They also deploy an instance of the Platypus open-source reverse shell utility to maintain access to the host. Additionally, multiple user-mode rootkits are deployed to hide malicious processes, further complicating detection and mitigation efforts.
Initial Access and Payload Delivery
The initial access observed by Cado Security Labs involved a Docker command received from an IP address that spawned a new container, leveraging the container to write out an executable and registering a Cron job to execute base64-encoded shell commands. This executable, identified as vurl, establishes a TCP connection with the attacker’s Command and Control (C2) infrastructure, facilitating the retrieval of the first-stage payload.
The primary payload, cronb.sh, is a straightforward shell script that defines the C2 domain and URL where additional payloads are located, checks for the existence of the chattr utility, and retrieves the next payload based on the current user’s privileges.
System Weakening and Anti-Forensics
The malware employs a variety of system weakening and anti-forensics commands, including disabling firewalld and iptables, deleting shell history, disabling SELinux, and ensuring outbound DNS requests are successful. It also installs a number of utilities, such as masscan for host discovery, and proceeds to run commands that weaken the system’s security posture and cover the tracks of the attackers.
This malware campaign highlights the evolving threat landscape and the sophistication of attackers in exploiting cloud-based infrastructures for cryptomining. The use of unique payloads, exploitation of known vulnerabilities, and deployment of anti-forensics techniques underscore the need for heightened vigilance and robust security measures to protect against such sophisticated threats.
Implications for Businesses and Users
The exploitation of misconfigured servers for crypto mining poses several risks to businesses and individual users. First and foremost, it leads to unauthorized use of computing resources, resulting in increased operational costs and potential disruption of critical services. For businesses, this can translate into financial losses and damage to reputation if services become unavailable or if sensitive data is compromised during the breach.
Moreover, the presence of unauthorized software on a server can be a gateway for further malicious activities, including data theft, ransomware attacks, or the establishment of a foothold for future attacks. The security breach can also lead to regulatory compliance issues, especially for businesses subject to strict data protection laws.
Mitigation Measures
To protect against the exploitation of misconfigured servers, businesses and administrators must adopt a proactive approach to cybersecurity. This includes:
- Regular Audits and Assessments: Conducting regular security audits and vulnerability assessments to identify and rectify misconfigurations or outdated software.
- Adherence to Security Best Practices: Implementing security best practices, such as using strong, unique passwords, enabling two-factor authentication, and applying the principle of least privilege to server access.
- Network Segmentation: Isolating critical systems and services from the rest of the network to limit the spread of malware or an attacker’s movement within the network.
- Monitoring and Detection: Deploying monitoring tools to detect unusual activity, such as spikes in CPU usage that could indicate crypto mining activities. Implementing intrusion detection systems can also help identify and block malicious traffic.
- Education and Awareness: Educating administrators and users about the risks associated with misconfigured servers and the importance of following security guidelines.
The exploitation of misconfigured YARN, Docker, Confluence, and Redis servers for crypto mining highlights the critical importance of cybersecurity vigilance. As attackers continue to evolve their tactics, businesses and administrators must stay informed about potential vulnerabilities and implement robust security measures to protect their digital assets. By taking proactive steps to secure server configurations and monitor for suspicious activity, it is possible to mitigate the risks associated with these types of cyber attacks.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
