A database that formerly belonged to the cybercrime platform known as RaidForums but has since been shut down has been exposed on a new hacker forum known as Exposed. The database includes the personal information of 478,000 different RaidForums users. As a consequence of the multinational law enforcement operation known as TOURNIQUET, which was managed by the European Cybercrime Centre of Europol, the illicit dark web marketplace known as RaidForums was taken down and its infrastructure was seized in the month of April 2022.
RaidForums was established in 2015, and since then, its community has grown to include more than 500,000 members. The selling of high-profile database leaks belonging to a number of US firms operating in a variety of sectors contributed significantly to the marketplace’s rise to prominence. Following the closure of Raidforums, members rushed to a new website named Breached, where they could carry on selling stolen datasets. Breached, however, went down in March 2023 when its creator and owner, Pompompurin, was taken into custody by the FBI. This caused the site’s other administrator to become afraid that government authorities had access to their servers.
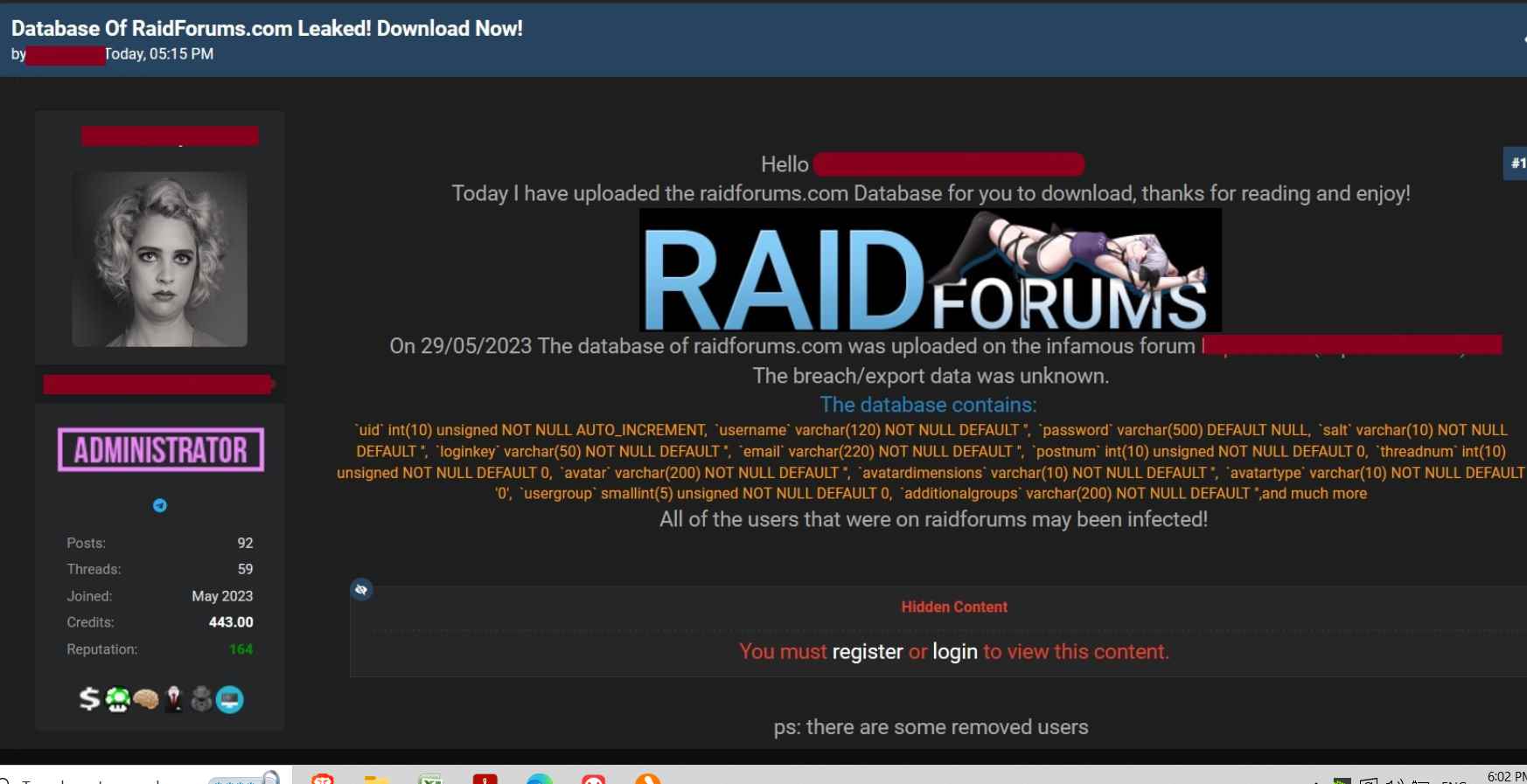
It seems that the database is current as of September 2020. In it, you’ll find listings not just for moderators and well-known users, but also for the site’s owner, Omnipotent. We did some random checks on the database, and we came across users that had the same email addresses, Jabber IDs, and usernames that we already knew.
The administrator who submitted the breach included a comment to the effect of “ps: there are some removed users.” They did not make it clear if they were the ones who deleted people from the database or whether others did so.
There is currently no evidence to suggest how this database was leaked, who was the first person to disclose it, or the reason why it is only now being made public for the first time.Despite the fact that it is very probable that law enforcement already has possession of the database as a result of the forum being seized, this information may still be valuable to security researchers who often construct profiles of threat actors.
Researchers are able to learn more about the threat actors by using the stolen registration information, which also allows them to possibly connect the threat actors to further harmful operations.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
