Researchers from Cisco Talos have uncovered a novel and very sophisticated phishing-as-a-service (PaaS) offering, which they have given the name “Greatness.” Greatness is a service that has been operational since at least the middle of 2022. It includes evasion of multi-factor authentication (MFA), IP filtering, and interaction with Telegram bots. At the moment, it concentrates on phishing via Microsoft 365, which makes it a serious risk for enterprises all around the globe. Greatness gives its customers access to a link and attachment builder, which allows them to create plausible fake login sites and decoys. It is able to pre-fill victims’ email addresses and show relevant corporate logos and backgrounds, which makes it more effective against business users who are unaware they are being targeted. Companies in the United States of America, the United Kingdom of Great Britain, Australia, South Africa, and Canada have been the principal targets thus far, with the manufacturing, healthcare, and technology industries being targeted the most often. It is interesting to note that Greatness seems to have a little regional concentration in each campaign; nonetheless, when looking at all targets together, more than half of them are headquartered in the United States.

Affiliates are given a phishing kit by Greatness, which contains an API key that enables even inexperienced actors to take use of the service’s more complex capabilities. This is how the company functions. The phishing kit and API work together to impersonate the Microsoft 365 authentication system and steal the victim’s credentials through a “man-in-the-middle” attack. This is accomplished by serving as a proxy to the authentication system.
The attack is carried out in a number of phases. At first, victims are sent a malicious email that contains an HTML file that seems to be a shared document. When the attachment is opened, obfuscated JavaScript code is executed, which then retrieves the HTML code of the phishing website from the server controlled by the attacker. After that, the website will take the victim to a plausible login page for Microsoft 365, which will already have the victim’s email address as well as the company’s branded backdrop and logo pre-filled.

As soon as the victim inputs their password, the PaaS establishes a connection to Microsoft 365, where it then pretends to be the victim and tries to log in. If multi-factor authentication (MFA) is enabled for the service, the user will be prompted to authenticate using MFA. After it has been given the MFA, it will go on with the impersonation, finish the login procedure, and collect the authenticated session cookies. After that, they are sent to the affiliate either via their Telegram channel or directly through the web panel, depending on which method they choose.
Phishing kit (which includes an admin panel), application programming interface (API) for the service, and a Telegram bot or email address are the three components that make up the service. The phishing kit sends the HTML/JavaScript code for each stage of the attack to the PaaS API, transmits the credentials obtained from the victim to the PaaS API, and gets instructions on which page it should send to the victim when it has finished delivering the previous page. Additionally, the kit saves the stolen credentials for the affiliate and, if the affiliate’s Telegram channel is enabled to receive them, it posts the credentials there.
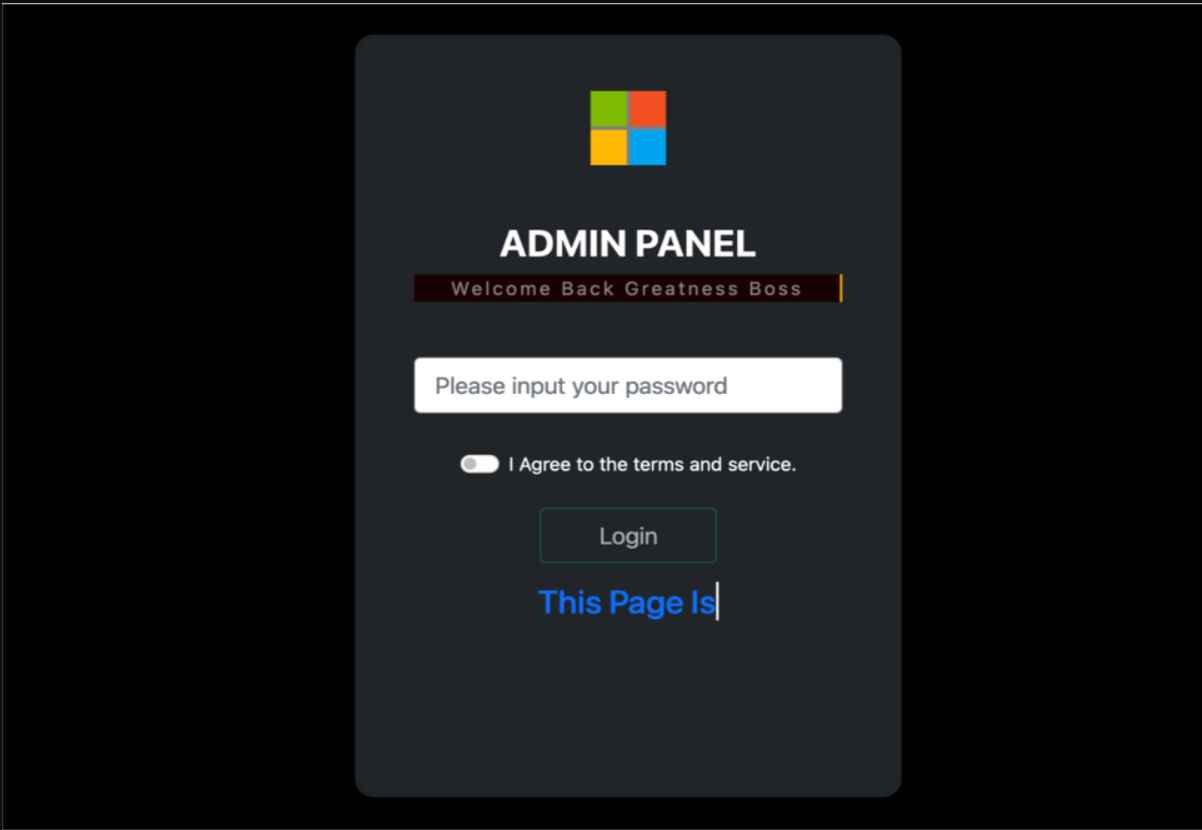
Through the use of an administrative panel, the affiliate may monitor stolen credentials and configure the API key for the service as well as the Telegram bot. Additionally, it creates potentially harmful files or URLs that are sent to the victims of the attack.
To summarize, the Greatness phishing service poses a big new risk to companies all around the globe. Because of its sophisticated capabilities and the fact that it is tailored specifically for Microsoft 365 customers, it is a powerful weapon in the hands of hackers. Companies have a responsibility to be aware of this new risk and to take extensive precautions to protect the confidentiality of their proprietary information.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
