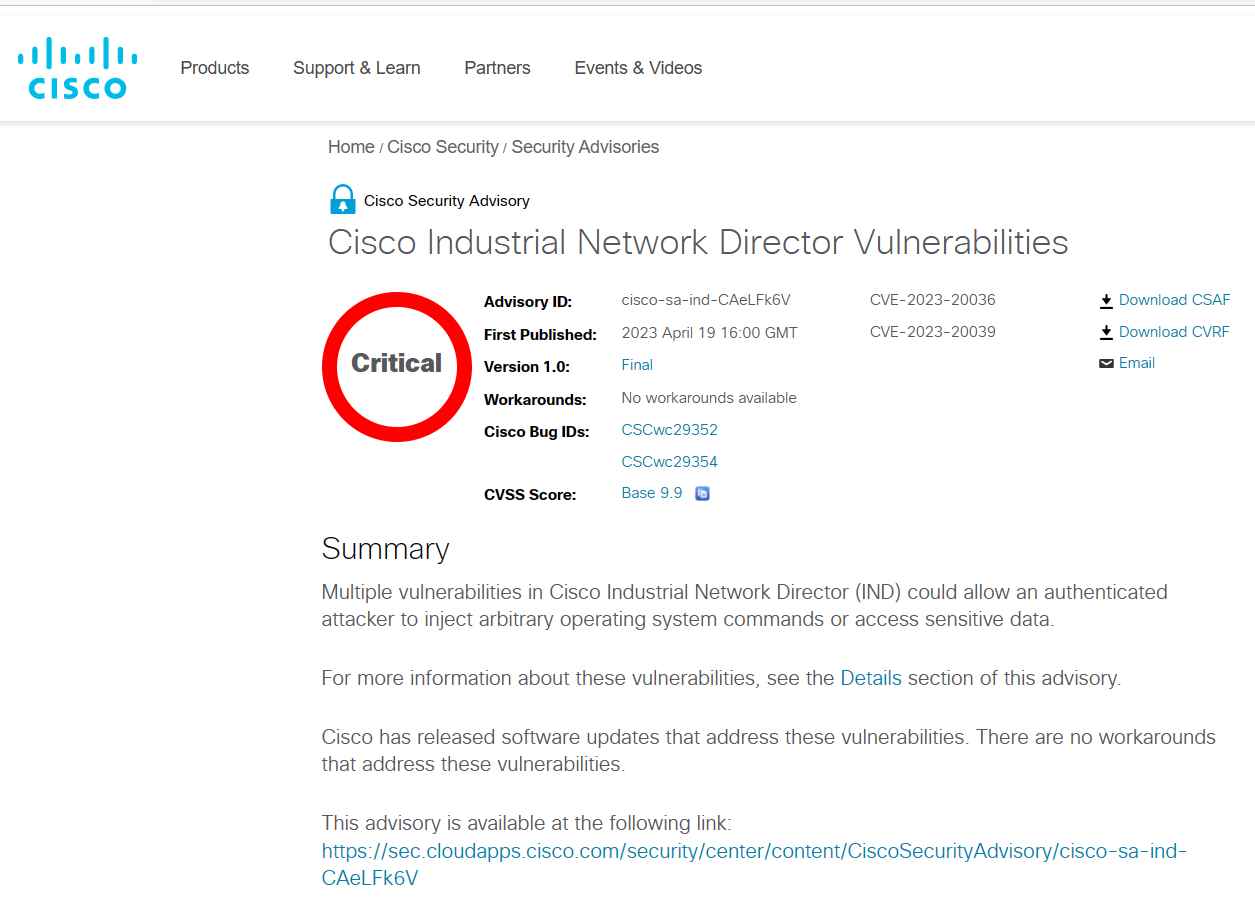
Cisco Industrial Network Director (IND) is an important tool for managing industrial networks, particularly in settings that need high-security standards. This is especially true in situations where there is a need for high-level data protection. Recently, two vulnerabilities that might allow authorized attackers to inject arbitrary operating system instructions or get access to sensitive data were found in IND. Both of these vulnerabilities were discovered quite recently. Cisco has addressed these by releasing software updates; nonetheless, it is critical for enterprises to be aware of the risks and take proper action.
Command Injection Vulnerability, also known as CVE-2023-20036
The Cisco Industrial Network Director Command Injection Vulnerability has a score of 9.9 on the CVSS scale, making it the more serious of the two vulnerabilities. An authorized, remote attacker is able to execute arbitrary commands with administrator capabilities on the underlying operating system of an affected device by exploiting a vulnerability that exists in the online user interface (UI) of Cisco IND.
A lack of sufficient input validation during the uploading of a Device Pack is the root cause of the CVE-2023-20036 issue. In order to take advantage of this vulnerability, attackers must first modify the request that is submitted during the upload process. If the exploit is successful, it gives the attacker the ability to run arbitrary commands on the operating system of the compromised device in the capacity of NT AUTHORITYSYSTEM.
File Permissions Vulnerability, also known as CVE-2023-20039
The permissions on files inside Cisco IND are the subject of the second vulnerability, which has a CVSS score of 5.5. Due to the inadequate default file permissions that were granted to the application data directory, this vulnerability may be exploited by a local attacker who has already been authenticated in order to access application data. An exploit that is successful might provide an attacker access to sensitive information by allowing them to see files located in the application data directory. This could then lead to other security flaws being exploited.
Cisco has published software updates that address both of these vulnerabilities, and enterprises are strongly encouraged to upgrade their systems to the first corrected release, IND version 1.11.3, or a later version of the software. Because there are no known solutions for these vulnerabilities, it is very necessary for users to install software updates as soon as they are made available.
The Product Security Incident Response Team (PSIRT) at Cisco is not aware of any public announcements or malicious exploitation of the vulnerabilities detailed in this advisory at the time that this document was written.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
