It was only recently revealed that the well-known Dark Web marketplace Genesis’s Clearnet site was taken over by authorities. Now, another online marketplace that is just as infamous as the others, known as Styx, has appeared.
Researchers working for the cybersecurity company Resecurity have discovered a new market on the Dark Web known as Styx. This market specializes in a broad variety of criminal activities, some of which include the theft of identities, financial fraud, and money laundering. Cash-out services, data dumps, SIM cards, DDOS, 2FA/SMS bypass, false and stolen ID papers, banking malware, and a great deal more are some examples of the particular service offers that are sold on STYX. Bad actors are able to make a profit from credential theft in the online banking and e-commerce sectors thanks to financial fraud, which is one of the most important catalysts in the commercial cybercriminal ecosystem. The marketplace started at some point around January 19, 2023, however investigators discovered previous allusions of its inception on the Dark Web in the early years of 2022. Whilst this was going on, the people behind STYX Marketplace were developing the built-in escrow module of the platform. This feature facilitates the brokering of transactions between buyers and sellers of illegal cybercriminal items and services.
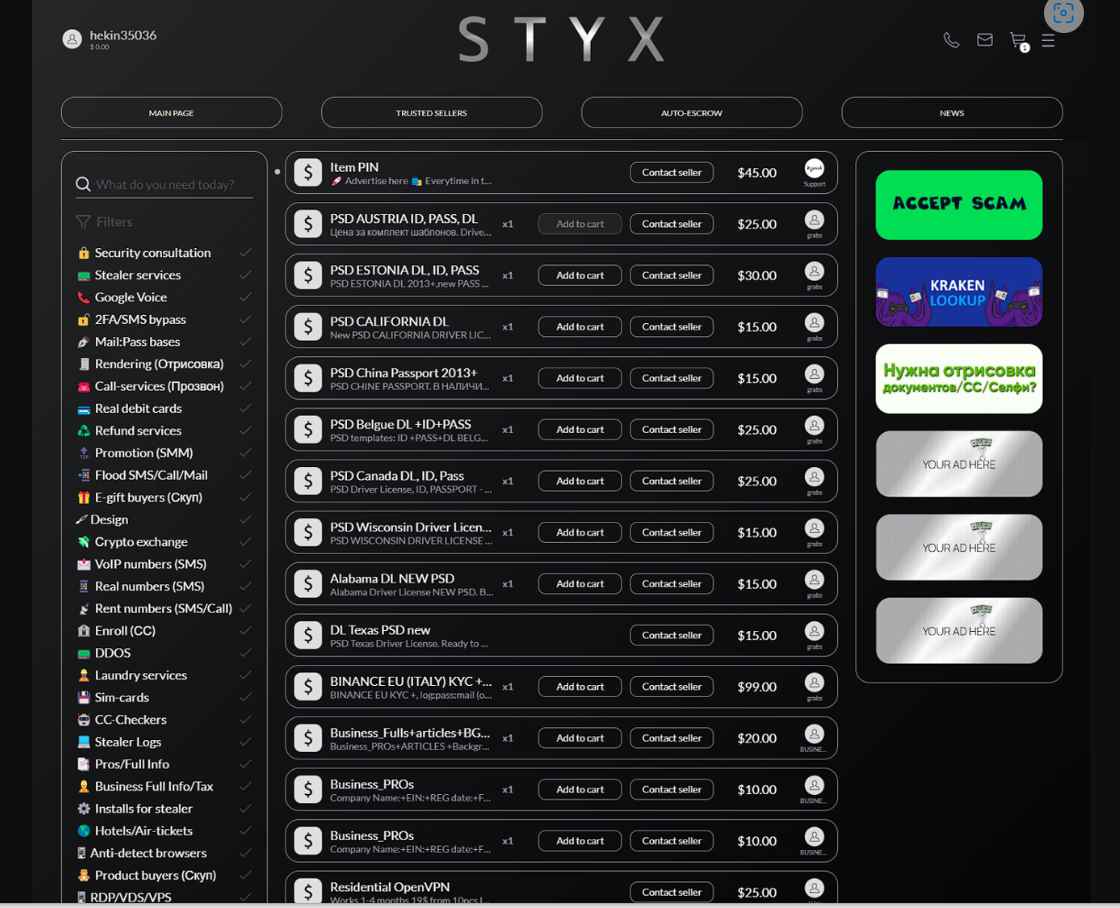
The vast majority of vendors on the STYX Marketplace are experts in providing fraud and money laundering services directed against well-known digital banking systems, online marketplaces, electronic commerce, and other payment applications. The United States, the European Union, the United Kingdom, Canada, Australia, and a number of nations located in Asia and the Middle East are among of the countries that are specifically targeted by these threat actors.
Money laundering services, which were marketed on STYX and other marketplaces, began to serve additional countries, including those in the Middle East. These jurisdictions were not previously extensively apparent in cybercriminal service listings. Because of the widespread use of online banking and shopping, financial firms in the Middle East are likely to run into the same difficulties with customer identification and fraud as businesses in North America, the European Union, and the United Kingdom.
Analysts first came across mentions of STYX Marketplace in a number of different Telegram groups. These groups offered members private access to various tools, such as anti-detects, device fingerprint emulators, and spoofers, that are frequently used in the commission of online banking theft and fraud.
These kinds of technologies are used by cybercriminals in order to circumvent anti-fraud measures and get access to compromised accounts. These fraud tools trick anti-fraud systems used by online retailers and banks by exploiting detailed digital identifiers such as stolen cookie files, physical device data, and network settings. This allows the tools to spoof real consumer logins and mislead anti-fraud systems.
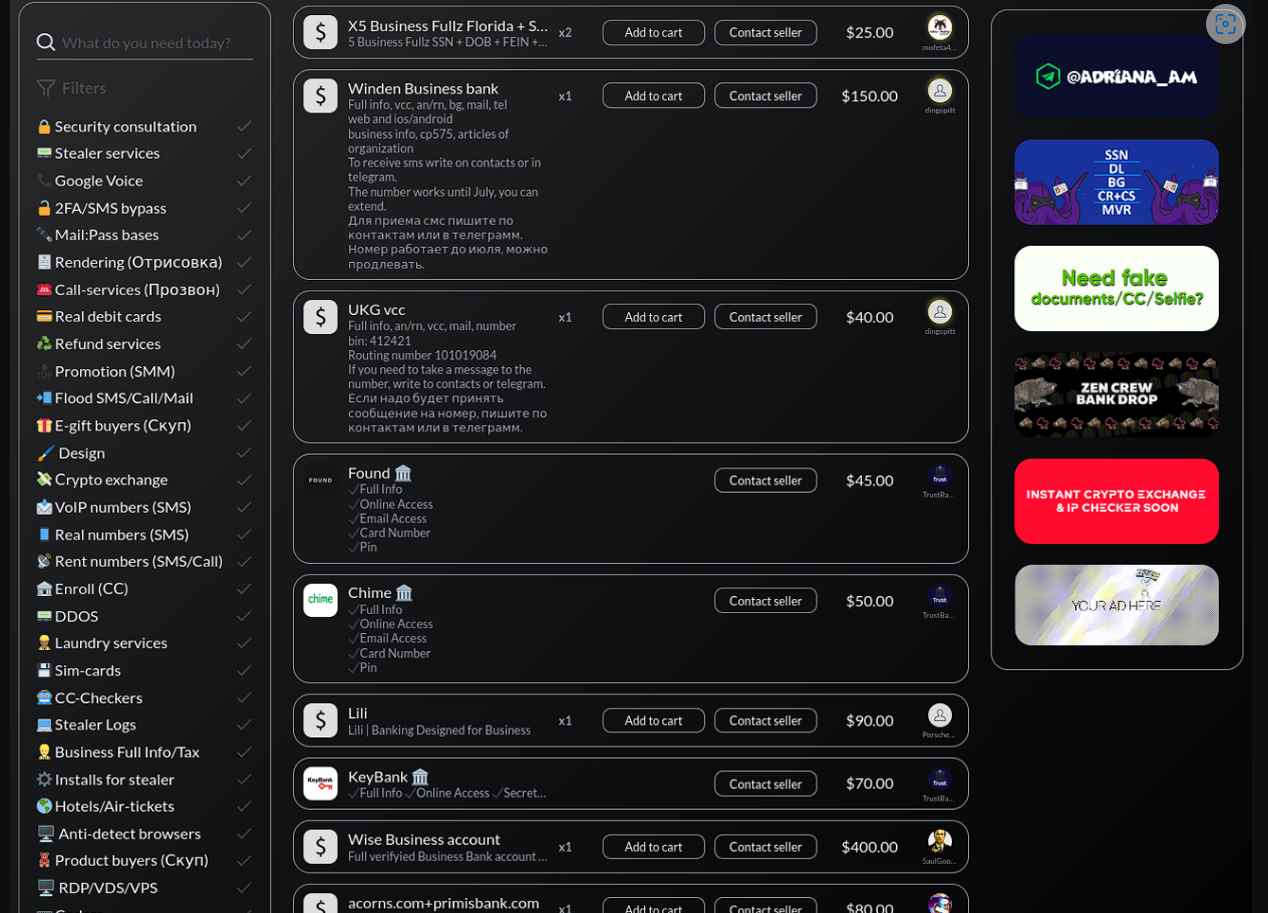
Enclave Service, a respected Dark Web business that offers tools for identity spoofing and anti-fraud bypass, lists one prominent STYX Marketplace offering.
Analysts also found various “checking services,” which enable threat actors to obtain information about a specific person and are used to collect that information. In most cases, bad actors make use of these sites as tools for doing reconnaissance on potential victims in order to increase their chances of successfully breaching their bank or credit card accounts.
Kraken is a well-known lookup service that has been offered on STYX Marketplace almost from the moment the site was first made available to users.
The service can be used using Telegram, and it gives users the ability to search for a victim using either their Social Security Number (SSN) or driver’s license (DL). In addition, Kraken is able to extract Credit Reports, which may be done on either persons or corporations. In most cases, fraudsters make advantage of hacked or obtained access through a third party associated with a respectable credit agency in order to utilize the services of the credit bureau for unlawful reasons. By perpetrating fraud, fraudsters are able to more easily pass numerous verifications and validate the identities of their victims thanks to the data offered by Kraken and other suppliers in a similar vein.
Another important STYX Market seller category is those that provide phone and email flood services. When the bank account of the victim has already been hacked and the fraudster wants to prevent the account owner from having any communication with the institution’s anti-fraud team, these services are incredibly helpful. In situations involving exploitation, this compliance unit could send an email or text message to a victim in order to confirm suspicious behavior on their account, or they might phone them.
Flooding services are used by fraudsters in order to prevent a customer engagement from taking place. These services inundate the phone and email accounts of a victim with a huge frequency of calls and messages, which might potentially drown out bank interactions.
Laundering money is one of the most important aspects of the STYX Marketplace. Several underground merchants offering cash-out services from compromised virtual credit card accounts, online banking accounts, e-commerce merchant accounts, and cryptocurrency exchange accounts.
In addition to that, there is a treasure mine of guides about cybercrime and fraud on STYX Marketplace. It’s possible that reading through any of these materials can assist raise knowledge about cybersecurity and improve risk management. The lessons include information on how to conduct tax fraud, establish new accounts in digital banks and e-commerce platforms, and use ChatGPT for harmful reasons.
STYX Marketplace is a prominent example of a newly developing kind of cybercriminal platform. This type of site caters to financially-motivated threat actors who are engaged in online bank theft as well as other fraudulent activities. The introduction of this marketplace on the dark web provides further evidence that the threat actor category is still experiencing a high level of activity and is positioned for major expansion.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
