For reasons of safety, computers that are separated by an air gap are not connected to the Internet or any other network. Typically, they are used in energy infrastructures, government institutions, military installations, and other similarly delicate settings.
In order for a cyberattack to be successful against such systems, the attacker must first get physical access to the air-gapped device or network. Malware might be installed on the machines that are the target of the intrusion. And we are aware that occurrences of this kind have taken place in the past: a security breach occurred at an Iranian uranium enrichment plant, and a military site in the United States was infected with Agent.BTZ.
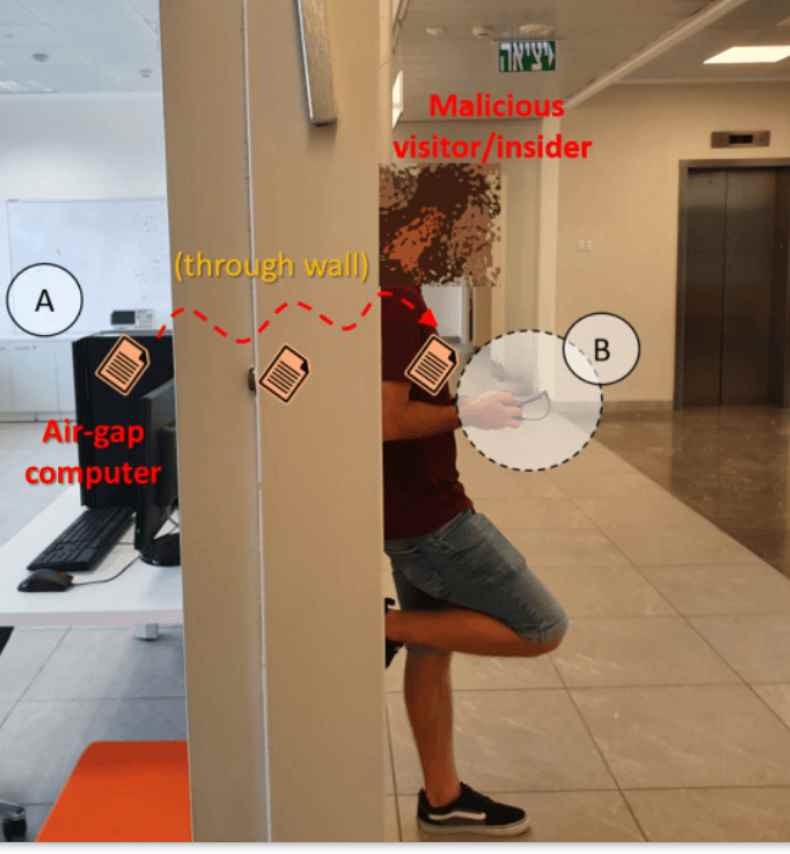
COVID-bit is a novel attack tactic that makes use of electromagnetic waves to break into air-gapped computers. It has a data transmission range of at least two meters and can penetrate air-gapped computer systems (6.5 ft).
The exfiltrated data is able to be received by a nearby smartphone or laptop, even if the two devices are physically separated by an obstacle such as a wall.
Mordechai Guri, a researcher at Ben-Gurion University, is the one who uncovered this particular technique of attack.
Researchers developed a program that, in order to carry out the COVID-bit attack technique, “regulates CPU load and core frequency in a certain way to make the power supply on air-gapped systems emit electromagnetic radiation on a low-frequency band” (0 – 48 kHz).
The internal architecture of SMPS as well as the switching characteristics of these power supplies are the key reasons why they emit electromagnetic radiation. During the conversion from AC to DC and DC to AC, the MOSFET switching components are responsible for producing a square wave by turning on and off at precise frequencies.
These electromagnetic waves are able to send raw data to a receiver, which may be a computer or a mobile device like a smartphone. In order for the receiver device to pick up the signal, it requires a loop antenna that is linked to the 3.5mm audio connector, much like headphones or earbuds. After that, a noise reduction filter is used, followed by the demodulation of raw data and the decoding of the information.
Testing Results
“with three sorts of systems: PC workstations, laptops, and embedded devices,” was how the COVID-bit approach was evaluated during testing. During the testing process, the zero-bit error rate was maintained on desktop computers and embedded devices for up to 200 bps, and it was maintained on laptops for up to 100 bps.
Laptops fared poorly due to their energy-saving profiles and signals that were not powerful enough, while embedded devices had a restricted distance due to their insufficient power supply. Desktop PCs had the best transmission rate, which was up to 500 bps for a bit error rate between 0.01% and 0.8%.
At the highest transmission rate that was ever tested, which was 1,000 bps, it would take 80 seconds to send a file that was 10 kilobytes in size, a 4096-bit RSA encryption key could be sent in as little as four seconds or as long as ten minutes, and the raw data from an hour’s worth of keylogging would be delivered to the receiver in just 20 seconds.
Even at transmission rates as low as five bits per second, live keylogging would still operate in real time to record keystrokes.
Despite the fact that these preventative methods also have certain drawbacks, they provide you with a foundation around which you may build your defense plan.
Even if this does not eliminate the dangers that are already present on the network, you may protect your devices and network from this kind of attack by imposing stringent access restrictions on the devices and so preventing the installation of any malware.
Monitoring the utilization of the CPU cores and the behavior of the machine for any unusual trends might also be helpful in this situation. This security strategy involves evaluating large amounts of data and results in a large number of false positives.
Or, you may set the frequency of the CPU core to a fixed value, with the intention of making it more difficult, if not impossible, to generate the signal that carries the data, and perhaps even blocking it entirely. Taking this strategy has the drawback of either lowering the speed of the CPU or squandering a significant amount of energy, depending on the lock frequency.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
