A new strain of ransomware written in Golang called “Agenda” has been detected in-the-wild, targeting health and education entities in Indonesia, Saudi Arabia, South Africa, and Thailand.
“Agenda can reboot systems in safe mode, attempts to stop many server-specific processes and services, and has multiple modes to run in, Trend Micro researchers said in an analysis last week.
Qilin, the threat actor that advertises the ransomware on the dark web, is said to provide affiliates with options to customize binary payloads for each victim, allowing operators to decide the ransom note, encryption extension, as well as the list of processes and services to terminate before starting the encryption process.
Additionally, the ransomware incorporates techniques to evade detection by taking advantage of a device’s “safe mode” feature to continue its file encryption routine undetected, but not before changing the user’s default password and enabling login. automatic.
Upon successful encryption, Agenda renames the files with the configured extension, drops the ransom note in each encrypted directory, and reboots the machine in normal mode. The amount of ransom money requested varies from company to company, ranging from $50,000 to $800,000.
Agenda, in addition to leveraging local account credentials to run the ransomware binary, also comes with capabilities to infect an entire network and its shared drivers.
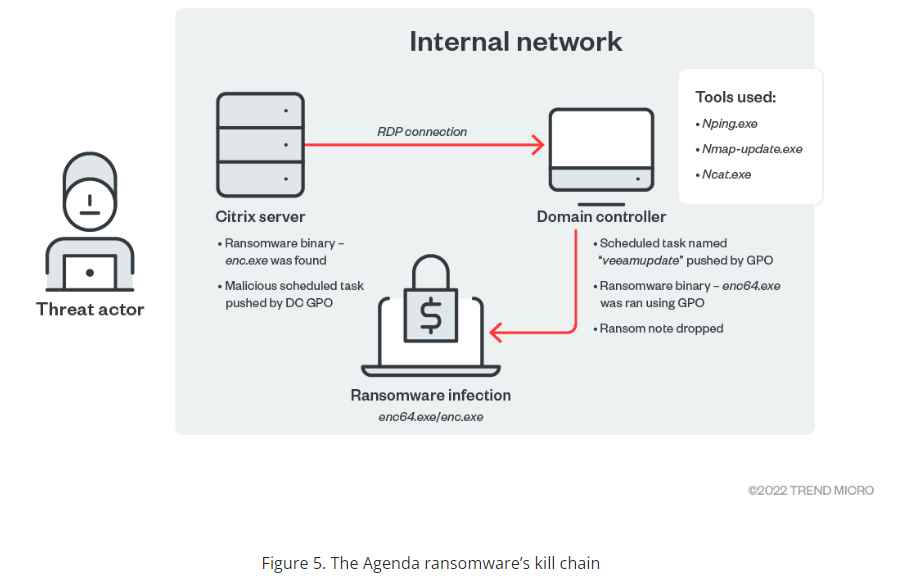
In one of the observed ransomware-related attack chains, a public-facing Citrix server served as the entry point to deploy the ransomware in less than two days.
Trend Micro said it observed similarities in the source code between Agenda and the Black Basta, Black Matter and REvil (also known as Sodinokibi) ransomware families.
Black Basta, which first emerged in April 2022, is known to employ the double extortion technique of encrypting files on the systems of targeted organizations and demanding a ransom to make decryption possible, while threatening to publish the sensitive information. stolen if a victim chooses not to pay the ransom.
As of last week, the Black Basta group has compromised more than 75 organizations, according to Palo Alto Networks Unit 42, up from 50 in June 2022.Agenda is also the fourth variety after BlackCat, Hive and Luna to use the Go programming language. “Ransomware continues to evolve, developing more sophisticated methods and techniques to infect organizations,” the researchers said.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
