Cisco products customers have been alerted with critical high-severity flaw in its email and web security appliances
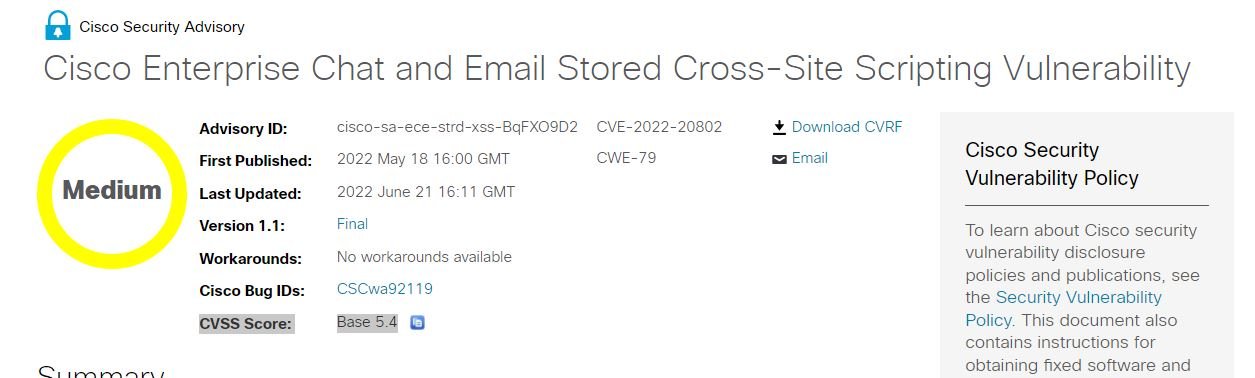
Affected Product: Cisco Enterprise Chat and Email
CVE-2022-20802
Criticality: Medium
Stored Cross-Site Scripting Vulnerability
Description:
A vulnerability in the web interface of Cisco Enterprise Chat and Email (ECE) could allow a remote threat actor to perform a cross-site scripting (XSS) attack against a user of the interface.
This vulnerability is due to insufficient validation of user-supplied input that is processed by the web interface. An attacker could exploit this vulnerability by sending a crafted HTTP request to the affected system.
Result:
A successful exploit could allow the threat actor to execute arbitrary code in the software or steal private data from the browser. To successfully exploit this vulnerability, an attacker would need valid agent credentials.
Mitigation:
Cisco has released software updates that fix this vulnerability.
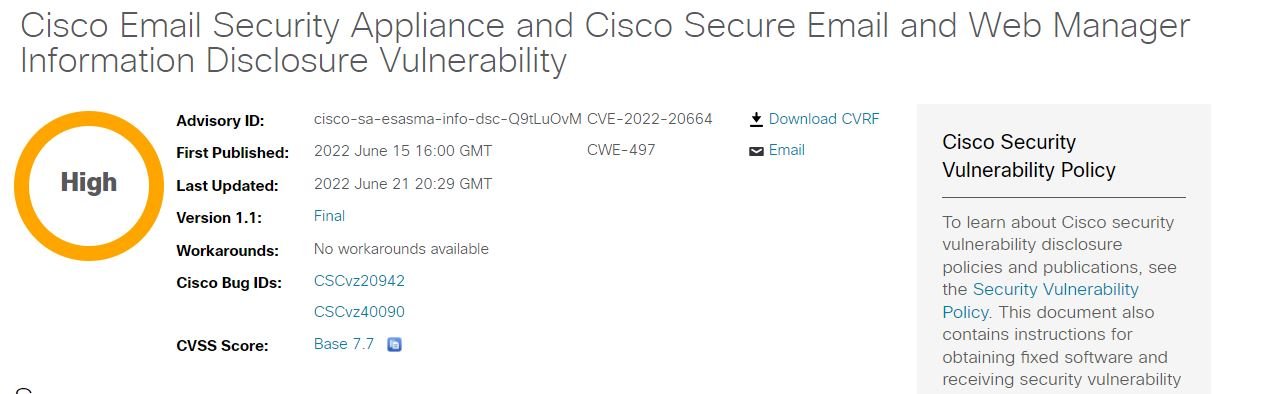
Affected Product: Cisco Email Security Appliance and Cisco Secure Email and Web Manager
CVE-2022-20664
Criticality: High
Information Disclosure Vulnerability
Description:
A vulnerability in the web management interface of Cisco Secure Email and Web Manager, formerly Cisco Security Management Appliance (SMA), and Cisco Email Security Appliance (ESA) permits remote threat actors to steal confidential LDAP data from external authentication servers connected to an affected device.
This vulnerability is due to a lack of proper input sanitization while querying the external authentication server. A threat actor could exploit this vulnerability by sending a crafted query through an external authentication web page.
Result:
A successful exploit could allow the attacker to steal sensitive information, including user credentials. To successfully exploit this vulnerability, an attacker would need valid credentials.
Mitigation:
Cisco has released software updates that fix this vulnerability.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
