This week, Drupal administrators announced the release of security updates in order to address some security flaws that could lead to access bypass and data overwriting attacks.
In its report, the open-source content management system (CMS) notes that the first of these flaws is described as an access evasion error that exists due to a generic entity access API incorrectly implemented for entity reviews.
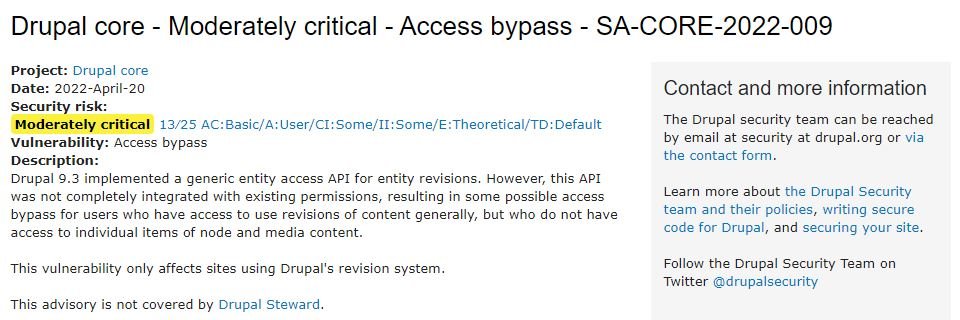
Apparently, this API was not fully integrated with existing permissions, resulting in possible access evasion for users who have access to use content revisions in general, but who do not have access to individual node elements and multimedia content.
The flaw only resides in Drupal version 9.3 and affects only websites where the Drupal patch system is actively used.
On the other hand, the second flaw resides in the Drupal core forms API and is described as incorrect input validation on certain custom or contributed module forms. Because of this error, threat actors could inject disallowed values or arbitrarily overwrite data.
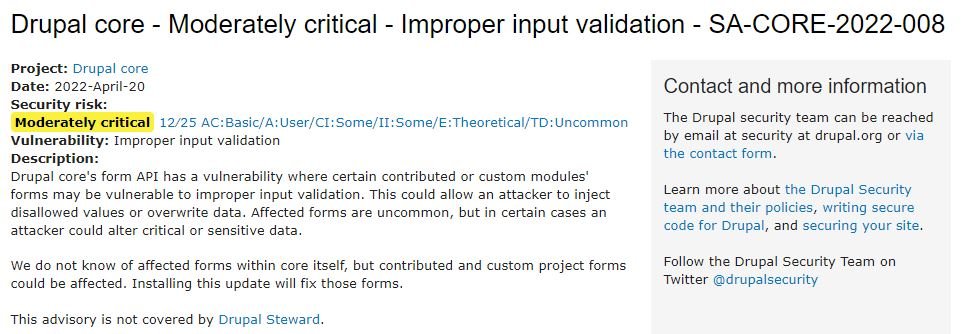
Affected forms are rare, but Drupal notes that in specific cases flaws would allow threat actors to modify critical or sensitive data. While Drupal says it doesn’t know which forms have been affected within the core itself, custom and contributed project forms could be compromised.
Both flaws received high severity scores, so users of this CMS are advised to apply the available patches as soon as possible. The issues were addressed with the release of Drupal 9.3.12 and Drupal 9.2.18. Versions of Drupal 9 earlier than 9.2.x and Drupal 8 have already reached the end of their life cycle, so they will not receive updates. Drupal 7 is not affected by these flaws.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
