Recent research shows that activating the mute function available in the various video conferencing applications might not have the effect expected by users, as the microphone could continue to work even with this feature enabled. According to researchers at the University of Wisconsin-Madison and Loyola University in Chicago, the mute function activated does not prevent the servers of these applications from receiving audio signals continuously or periodically.
This activity is not documented in the privacy policies of these platforms, so it is impossible for users to understand how the mute function works. This lack of information stood out in the first stage of the research, in which more than 200 users of various video calling platforms were surveyed.
The researchers conducted a full-time binary analysis of selected applications to determine what type of data each application collects and its implications related to user privacy. The research focuses on apps such as Zoom, Slack, Microsoft Teams/Skype, Google Meet, Cisco Webex, BlueJeans, WhereBy, GoToMeeting, Jitsi Meet and Discord.
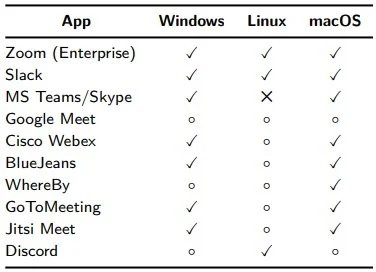
Experts tracked the raw audio streamed from applications to the underlying operating system’s audio driver and to the network in order to find out what exactly happens when a user activates the mute feature. The study found that, all apps analyzed occasionally collect audio logs, except web clients; in all other cases, applications take audio samples intermittently without a clear explanation.
An alarming case is that of Zoom, probably the most popular video conferencing application in the world. According to experts, the app actively tracks whether the user is talking, even when the mute feature is enabled.
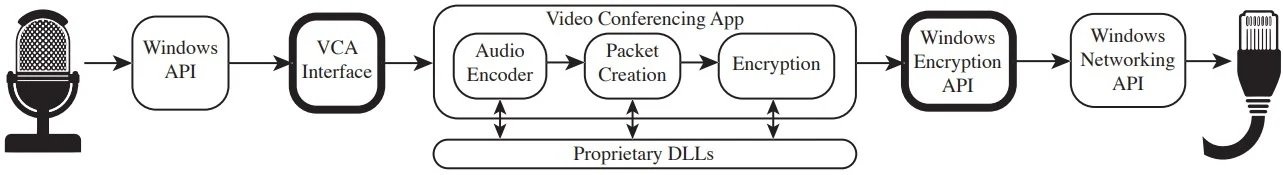
However, the worst-case scenario could be Cisco Webex, which continues to collect audio data and transmit it to the provider’s servers regardless of whether the microphone is turned on or off.
While most of these apps collect only small audio samples when the microphone should be off, research shows that it’s possible to use this information to decrypt users’ conversations for more than 80% of the time these apps use by using a machine learning algorithm.
The analyzed applications are already aware of these reports and are expected to take action on the matter as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
