Developers addressed a command injection vulnerability in asciidoctor-include-ext, a popular Ruby library that allows users to parse and convert AsciiDoc files. According to the report, this vulnerability allows remote code execution (RCE) attacks on subjacent systems, which would allow threat actors to take full control of the entire application and its data.
Security engineer Joern Schneeweisz, in charge of the report, mentions that it is possible to force remote code execution in asciidoctor-include-ext by feeding specially designed input strings: “The library made use of ‘open’/’IO.foreach’ to include files and URLs. Both methods can be used to execute commands when a pipeline symbol such as ‘|some_command –some argument’ is prepended to read from the standard output of that command instead of a file.”
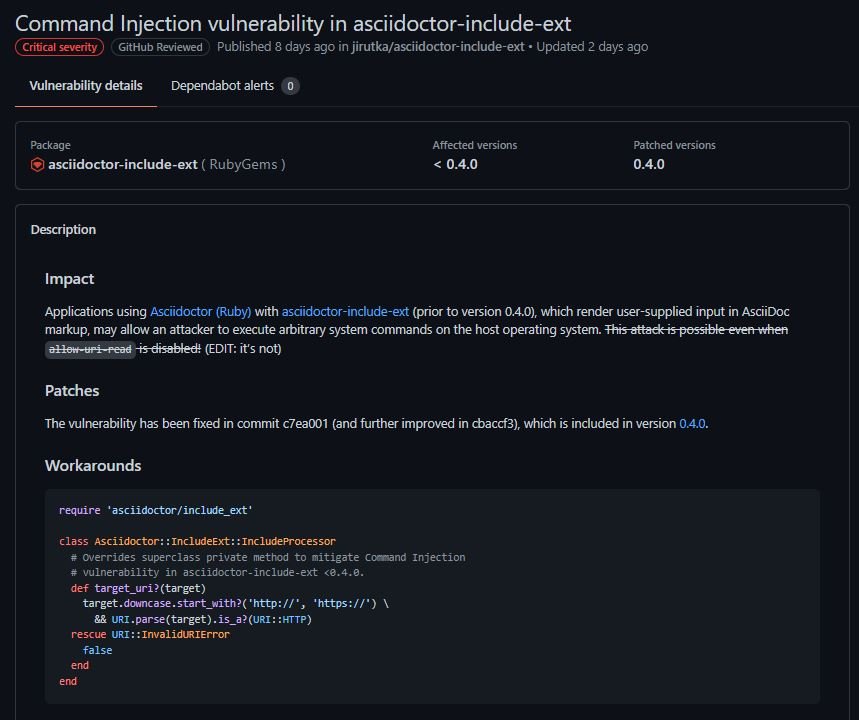
Successful exploitation would allow threat actors to obtain the rights granted to the committed process. The flaw received a score of 10/10 according to the Common Vulnerability Scoring System (CVSS): “The attack is quite easy and there is an exploit publicly disclosed,” Schneeweisz adds.
This type of vulnerability was first confirmed in 2015, when researcher Egor Homakov detailed how Ruby container libraries, such as those used in asciidoctor-include-ext, could be exploited in remote code execution attacks. According to the expert, the default behavior of open-uri is very dangerous and highly prone to failures like this.
For Homavok, this library should have been removed or divided into different functions, for example, openSystem, openURI and openFile, thus eliminating the ambiguities and security risk associated with these tools; despite these reports, the vulnerabilities were not fixed until now, in a decision criticized by the entire cybersecurity community.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
