VMware released a critical security alert to address various vulnerabilities found in Workspace ONE Access, VMware Identity Manager (vIDM), vRealize Lifecycle Manager, vRealize Automation, and VMware Cloud Foundation products.
According to the report, all users of Workspace ONE Access or any product that includes vIDM components are affected by these issues. Below are brief descriptions of the reported flaws, in addition to their respective tracking keys and scores assigned under the Common Vulnerability Scoring System (CVSS).
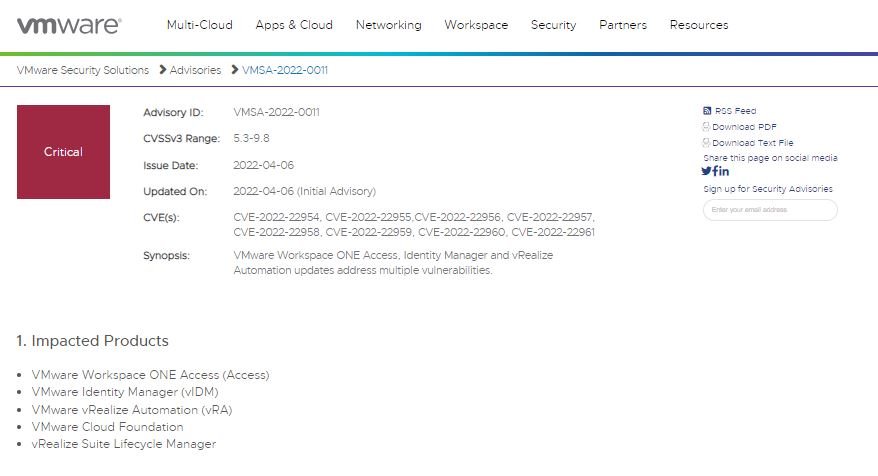
CVE-2022-22954: A remote code execution (RCE) vulnerability in VMware Workspace ONE Access and VMware Identity Manager that exists due to server-side template injection. The flaw received a CVSS score of 9.8/10.
The vulnerability must be corrected as soon as possible, since the risks derived from its exploitation are considerable. Apparently, a threat actor with network access can trigger template injection and eventual remote code execution.
CVE-2022-22955/CVE-2022-22956: These are authentication bypass errors in the OAuth2 ACS framework that affect VMware Workspace ONE Access. These flaws received CVSS scores of 9.8/10.
Threat actors could evade the authentication mechanism and execute any operation because of endpoints exposed in the authentication framework. It should be noted that these issues only affect Workspace ONE Access.
CVE-2022-22957/CVE-2022-22958: VMware Workspace ONE Access, Identity Manager, and vRealize Automation products are affected by two RCE flaws that received CVSS scores of 9.1/10.
According to the report, a malicious actor with administrative access could trigger a deserialization of unverified data, leading to the code execution scenario.
CVE-2022-22959: Threat actors can deploy server-side request forgery (SSRF) attacks to validate malicious JDBC URIs.
This vulnerability affects VMware Workspace ONE Access, Identity Manager, and vRealize Automation, and received a CVSS score of 8.8/10.
CVE-2022-22960: A local privilege escalation would allow threat actors to gain root access to the affected system. The vulnerability resides in VMware Workspace ONE Access, Identity Manager and vRealize Automation, and received a CVSS score of 7.8/10.
CVE-2022-22961: VMware Workspace ONE Access, Identity Manager, and vRealize Automation contain an information disclosure vulnerability due to excessive data return. The flaw received a CVSS score of 5.3/10.
The vendor has already made available security updates for all the products listed above. VMware concluded its report by assuring that so far no active exploitation attempts have been detected, although they will continue to monitor the situation until it is considered that the risk has been mitigated.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
