This week, Wordfence research teams detected an increase in infected websites hosted on the WordPress service managed by web hosting firm GoDaddy, which includes MediaTemple, tsoHost, 123Reg, Domain Factory, Heart Internet, and Host Europe Managed WordPress sites.
Apparently, these websites are affected by an almost identical backdoor prepended on the wp-config.php file. Of the 298 sites that have been recently infected, at least 281 are hosted with GoDaddy.
According to the report, the backdoor used in this campaign has been in use since at least 2015. This malicious development is capable of generating Google search results with spam and includes custom resources for the infected site. The main backdoor is added at the beginning of wp-config.php and looks as shown in the following screenshot:
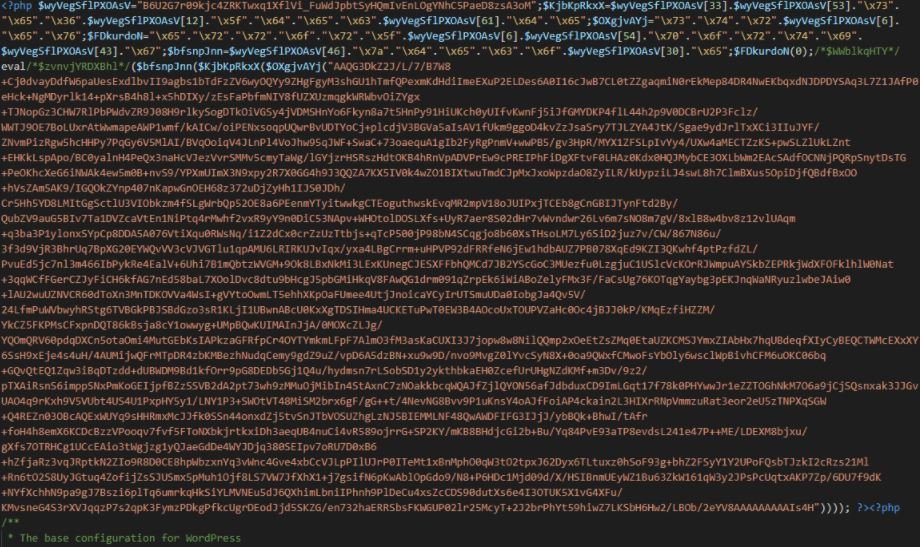
Below is a decoded version of the backdoor:
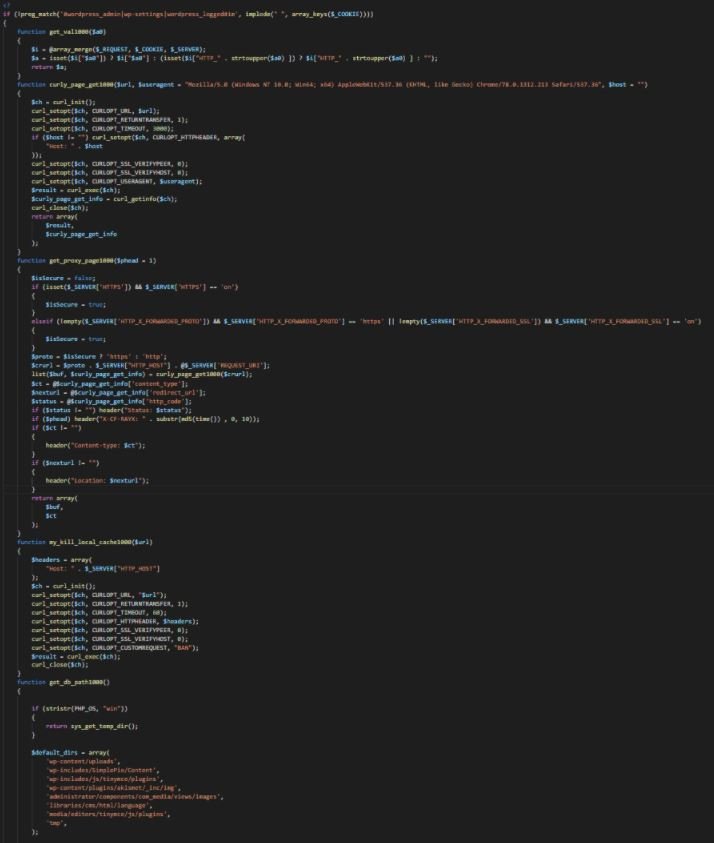
The Wordfence report adds that, if a request with a cookie set to a certain base64-encoded value is sent to the target site, the backdoor will download a spam link template from a C&C domain (t-fish-ka.ru), saving it in a file encoded with a name set to the MD5 hash of the infected site’s domain. For example, the file encoded for ‘examplesite.com’ would be called 8c14bd67a49c34807b57202eb549e461, which is a hash of that domain.
Although the C&C domain has a Russian TLD, at the moment there is no indication that this campaign is politically motivated or related in any way to the Russian military campaign in Ukraine. The domain shows a blank web page, but it was known that a couple of years ago it offered what appears to be adult content.
Here is a sample of the coded spam link template:
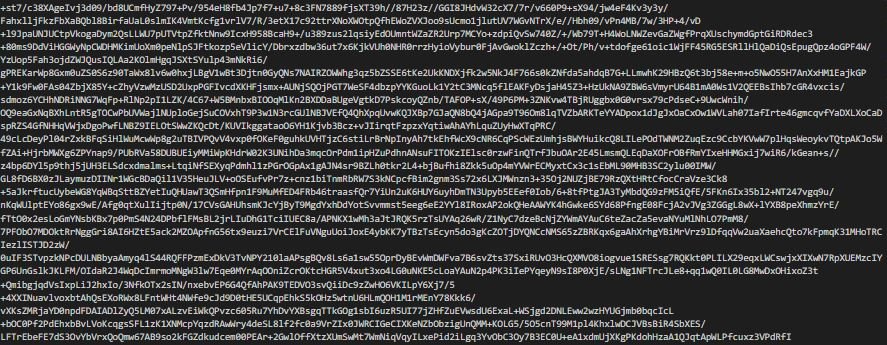
The attack vector used in this campaign is still unknown, although a year ago GoDaddy confirmed that an unidentified attacker had accessed its systems to provision the company’s managed WordPress sites, impacting up to 1.2 million of its WordPress customers. Researchers believe the two campaigns could be identical.
Faced with this scenario, the researchers recommend that users whose websites are hosted on these platforms manually check the wp-config file.php of their website, or run a scan with a malware detection solution.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
