In a joint report, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) detailed the detection of an inordinate increase in Conti ransomware attacks, which has already compromised more than 400 organizations in the U.S.
For researchers, this is a critical security risk because threat actors are not limited to encrypting infected files, but also resort to encrypting workstations and servers, in addition to using the tactic of double extortion.
Although Conti is commonly known as a ransomware-as-a-service (RaaS) operation, there are some variations its structure differs from an affiliate model like that of other similar operations. Instead of acting as collaborators with an attacker, Conti’s developers pay the attackers a kind of salary in exchange for the deployment of the attacks, extortion, and negotiations.
Attack chain
According to the report, Conti resorts to multiple initial access tactics to the affected systems:
- Phishing campaigns using emails with malicious attachments or links to insecure websites
- Use of filtered or easy-to-guess Remote Desktop Protocol (RDP) credentials
- Telephone fraud campaigns
- Malicious software advertised as legitimate tools
- Malware distribution networks such as ZLoader
- Vulnerabilities in external assets
During the execution of the ransomware, attackers execute a getuid payload before using a more aggressive payload in an attempt to evade detection by antivirus tools. Hackers also use the Router Scan pentesting tool to search for security cameras, routers, and other Internet of Things (IoT) devices, guessing your passwords with brute-force attacks, and gaining greater access to affected networks.
Conti operators can also exploit legitimate management and monitoring software to use as a backdoor to the affected system, gaining persistence on the network. Threat actors then use tools that are already available on the victim’s network or add additional tools, such as Windows Sysinternals and Mimikatz to obtain access credentials in clear text, allowing privilege escalation attacks.
CISA adds that the discovery of a kind of guide for Conti attacks allowed to identify that the operators of these campaigns exploit flaws known as:
- Vulnerabilities in Microsoft Windows Server Message Block 1.0 server
- CVE-2021-34527: Windows PrintButton Vulnerability
- CVE-2020-1472: Zerologon, the dangerous flaw in Microsoft Active Directory Domain Controller systems
Moreover, this guide identified four IP addresses of the Cobalt Strike server that Conti hackers previously used for their C&C communications:
- 162.244.80.235
- 85.93.88.165
- 185.141.63.120
- 82.118.21.1
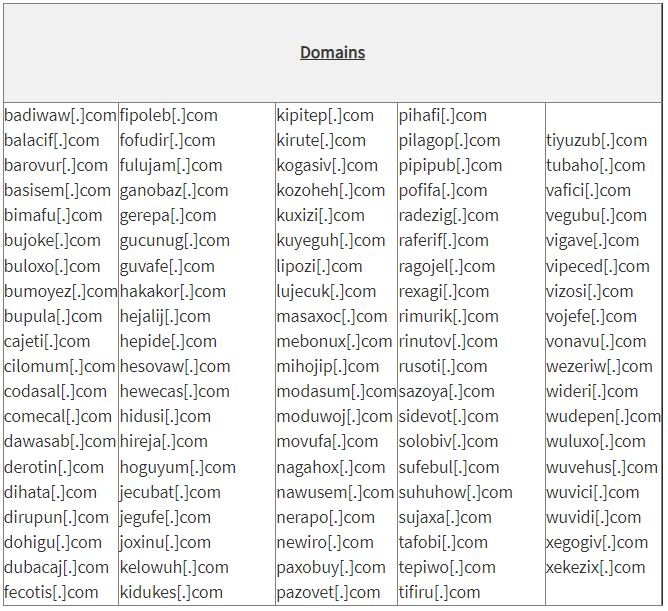
Indicators of Compromise
The report notes that the domains listed below have registration features similar to domains used as part of Conti ransomware attacks. Many of these domains have been used in malicious operations, although some may already be deprecated.
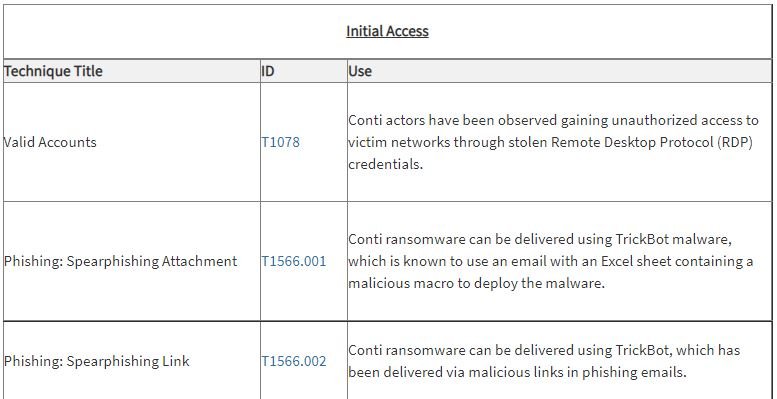
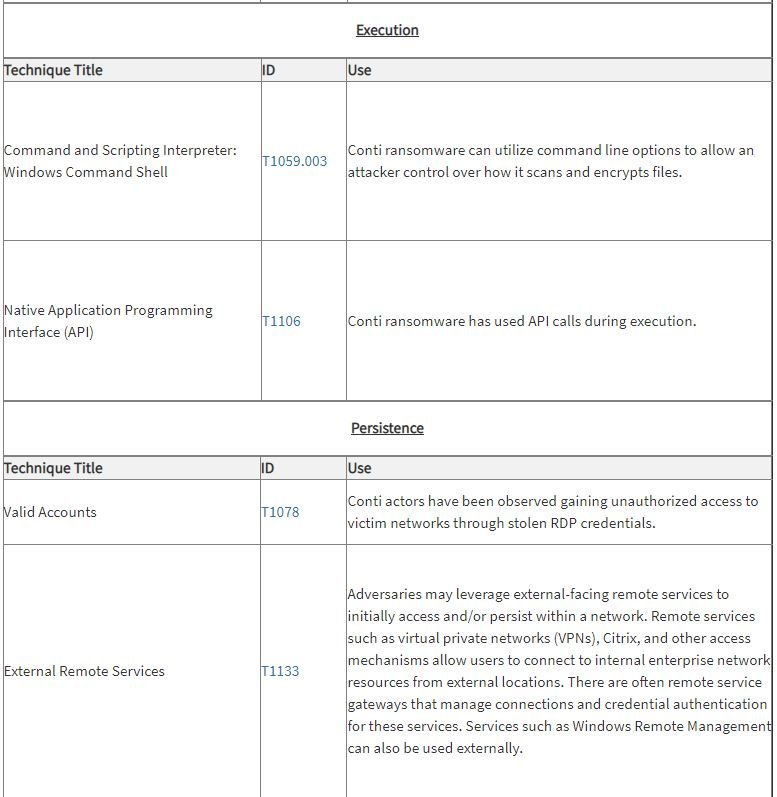
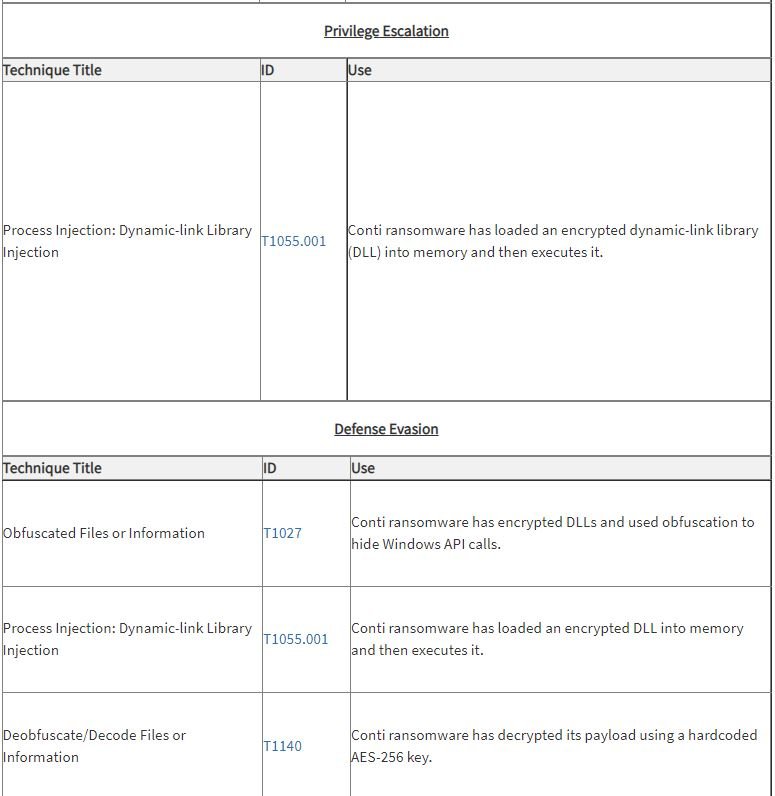
According to CISA and FBI, the operators of the Conti ransomware use some of the following hacking tactics:
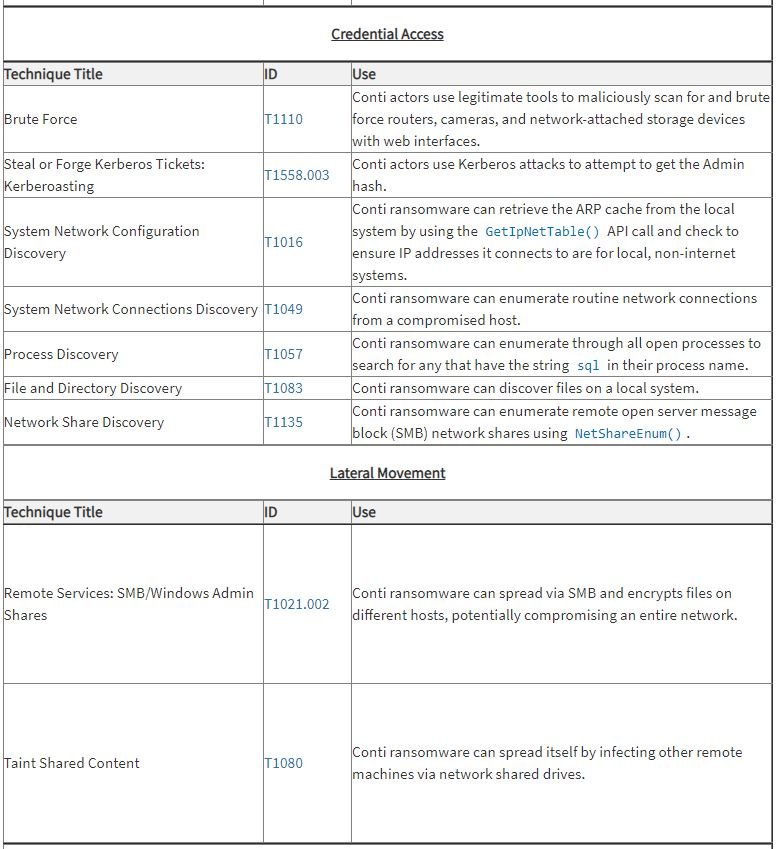
The agencies recommend reviewing the full report to review the best ways to mitigate the risk of infection, as Conti is considered an active and very dangerous cybersecurity threat, so it is necessary to stay protected against these risks.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
