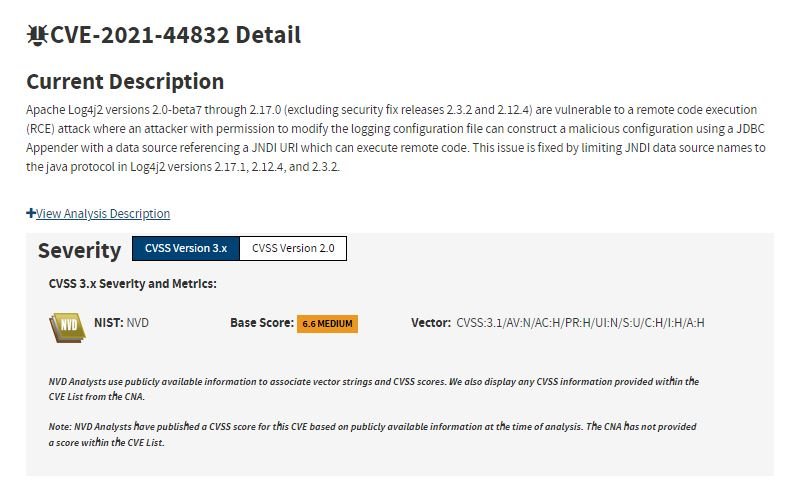
This week, the Apache Software Foundation issued a new set of patches to address remote code execution (RCE) flaws in Log4j, which could be exploited by threat actors to compromise vulnerable systems. Tracked as CVE-2021-44832, the most recent found flaw received a score of 6.6/10 on the Common Vulnerability Scoring System (CVSS) scale and resides on all versions of Log4j from 2.0-alpha7.
According to the report, these versions are vulnerable to remote code execution when an attacker with permissions to modify the log configuration file can construct a configuration using a JDBC Appender with a data source referencing a JNDI UEI capable of executing remote code.
Although Apache did not credit anyone with the report, researcher Yaniv Nizry claims to have presented this report: “This is a more complex vulnerability than the original CVE-2021-44228, as it requires threat actors to have control over the configuration. Unlike Logback, in Log4j there is a function to load a remote configuration file, so arbitrary code could be executed using a Man-in-The-Middle (MitM) attack, “says the expert.
The release of these patches represents the fourth time a security issue has been addressed in Log4j since the discovery of the dangerous Log4Shell vulnerability. Corrected faults include:
- CVE-2021-44228: Remote code execution bug affecting Log4j versions from 2.0-beta9 to 2.14.1
- CVE-2021-45046: Remote code execution and information leakage vulnerability affecting Log4j versions from 2.0-beta9 to 2.15.0
- CVE-2021-45105: Denial of service (DoS) flaw affecting Log4j versions from 2.0-beta9 to 2.16.0
- CVE-2021-4104: Untrusted deserialization error affecting Log4j version 1.2
The problems related to Log4j have only gotten worse; A couple of days ago, the governments of the United States, United Kingdom, Australia and Canada issued a joint alert about the massive exploitation of vulnerabilities detected in this library, so the outlook looks not encouraging for system administrators.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
