KELA cybersecurity researchers, dedicated to monitoring illegal activity on the dark web and on the conventional Internet, report the detection of a new black market platform that has recently appeared but has increased its activity exponentially since its launch. Identified as 2easy, this is an automated platform where all kinds of vendors offer confidential records stolen in security incidents, including information collected by botnets and logs stored by web browsers around the world.
The report notes that there are at least 18 active sellers on the platform, all of them dedicated to the sale of stolen sensitive information, especially login credentials. KELA estimates that the vast majority of the information available on this platform is valid and could pose severe security threats. At least half of the vendors on 2easy use RedLine information theft malware to collect the records sold.
Constant growth
According to the report, 2easy administrators began announcing the launch of the platform on multiple Russian hacking forums in mid-2020. The domain registration indicates that 2easy has been online since 2018, although the platform experienced its highest point of activity during the most recent months.
Proof of the growth of the platform is that by mid-2020 sellers offered information collected by about 28,000 bots, while currently the data is searched and collected by almost 600,000 bots. In addition, prices on 2easy are considerably more accessible than on other similar platforms, such as Genesis and Russian Market.
By accessing 2easy, interested users will have advantages such as:
- Access to all URLs where infected machines logged in
- Search for specific URLs
- Navigation through a list of infected machines
- Access to scores received by sellers
- Sale of access credentials for specific purposes
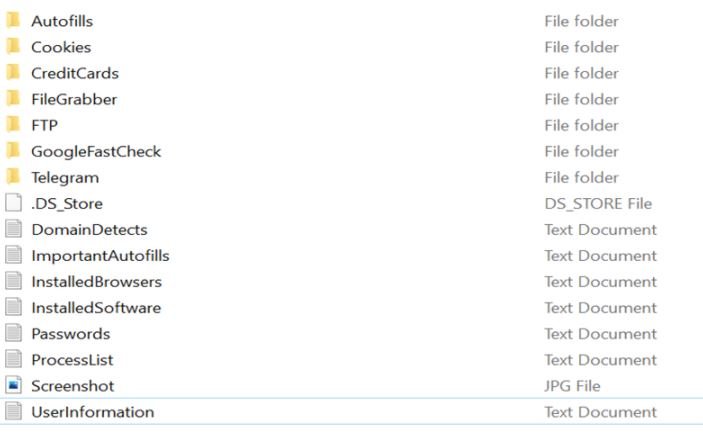
When purchasing a bot, users receive a ZIP file containing folders and files with maliciously collected information, including login credentials, credit card numbers, details about the victim’s system, and some records about the user. The type of data received by the buyer depends on the malware methods and variants used by the sellers.
The platform also offers an option to refund purchases if users consider that the quality of the information received is poor, no longer active, or has been used by other hacking groups before.
Sellers in 2easy
The platform’s administrators also frequently announce the opportunity to enter the market as sellers, in what seems to be the first stage of a major expansion plan, as 4 of the 18 current 2easy top sellers are monopolizing more than 90% of the bots listed on the platform.
About the malware used by these hackers, KELA reports that a unique piece of malware associated with the source code of RedLine, a recognized tool for information theft, was detected. While this tool is used by top marketers on the platform, other marketers turn to tools like Raccoon, another popular tool among the cybercriminal community.
Moreover, the top sellers on 2easy were identified as active members of multiple Russian hacking forums, such as Exploit, LolzTeam and XSS. One of these vendors uses the name Mayson_logs and has been identified as mayson147 in other cybercriminal communities; this vendor uses a service known as Univer City to provide access to various hacking and information collection tools.
Despite being a recently growing platform, 2easy seems to enjoy good popularity among various cybercriminal groups. On several occasions some sellers have been accused of fraud, although after internal investigations among the administrators it was determined that these accusations were inaccurate.
This shows that 2easy administrators try to evaluate and keep track of the activities of sellers, which will eventually increase the reputation of the platform. While 2easy’s activity level is still very low compared to other illegal platforms, its steady growth and efficient information theft methods seem to be enough to ensure that this could become one of the most important dark web black markets.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
