Information security experts report that StripChat, one of the largest webcam platforms for adults, was the target of a cybersecurity incident that led to a data breach, affecting millions of users and models. According to renowned researcher Bob Diachenko, the leak took place between November 4 and 7, when StripChat left its Elasticsearch database exposed without a password.
After analyzing the compromised information, Diachenko concluded that the incident would have exposed the profiles of some 65 million users and 421,000 models, which include details such as profile name, IP addresses, email addresses and fees, in addition to a record of more than 130 million transactions made on the platform and almost 1 million direct messages.
The company removed improper access to the database a couple of days after receiving the notification, though so far no StripChat representative or executive has mentioned anything about it.
Based in Cyprus, StripChat could be in severe breach of the rules set out in the General Data Protection Regulation (GDPR), as everything indicates that the incident was not reported to the relevant government entity or to the customers and models on the platform. To make matters worse, Diachenko believes that it is highly possible that some threat actor had access to the database during the time it remained exposed, although this is yet to be confirmed.
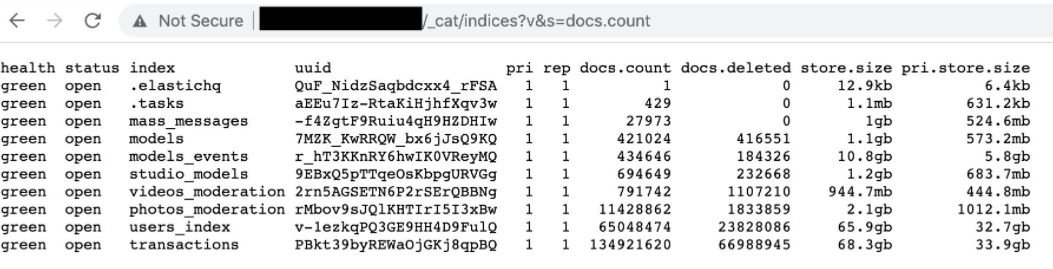
Specialists believe that, in the wrong hands, this information could represent a severe risk for those involved in StripChat, since a couple of data such as IP address and email are enough to follow up on a person, whether a webcam model or website user. So far this database has not appeared on hacking forums, although Diachenko assures he will keep monitoring the incident.
This is the third time a website of this nature has been involved in a data breach incident; in 2020, operators of the pushyCash webcam platform confirmed that a threat actor managed to extract the information from more than 4,000 models, while a couple of months later Cam4 revealed the theft of more than 7TB of personal data stored in their systems.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
