After revealing the detection of multiple cyberattack attempts, the chain of stores Tesco suffered a disruption in multiple computer services, including its website. The company’s online platforms are already up and running, although its security teams are still trying to mitigate the consequences of this incident.
It all started when dozens of users started reporting that features on Tesco’s website to make purchases and track their orders seemed not to work. Although at first the company only mentioned that the flaws were being addressed, an update of the incident confirmed an undue interruption to its systems.
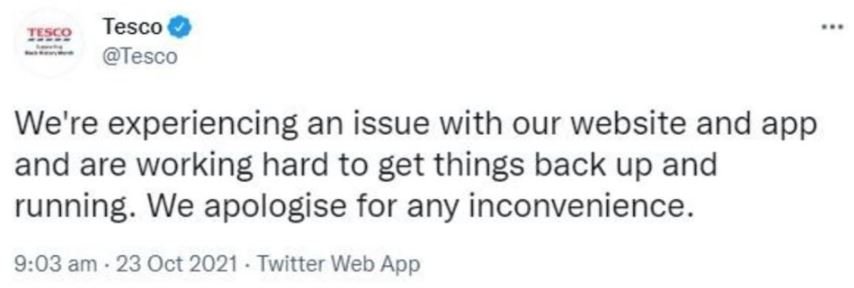
Through its Twitter account, Tesco confirmed that its mobile application and website would be restored as soon as possible, although they were taking measures to manage the huge volume of traffic detected in these implementations. The company identified this incident as an “attempted compromise,” though it did not specify further details about the attack.
Downdetector, a platform specializing in monitoring downed websites, says reports of Tesco’s service failures began Saturday morning, gradually increasing over the next few hours until peaking Sunday afternoon. The extent of the interruption is still unknown.
A few hours ago, a Tesco spokesperson noted that there is no evidence to assume that the problem reached a national scale, adding that customer information was not compromised during this incident. Finally, the spokesperson mentioned that users could experience minor failures over the next few days.
This is not the first time Tesco has faced a similar problem. In 2014, more than 2,000 user accounts were deactivated after the company detected the compromise of thousands of login credentials, an incident linked to a previous data breach.
These kinds of incidents are becoming more and more common; in early 2021, meat distribution giant JBS disrupted nearly 25% of its systems following an unprecedented cyberattack. Critical infrastructure is an attractive target for malicious actors, specially ransomware operators.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
