Researchers specializing in phishing campaigns detail the discovery of a new technique that allows threat actors to evade detection of these attacks, all thanks to the use of mathematical symbols in forged logos.
This new method was detected during the investigation of a hacking campaign against some customers of the telecommunications firm Verizon, in which the attackers used a square root symbol (√) and other characters in the company’s logo in order to evade anti-spam mechanisms on the affected systems.
According to experts, the company’s current logo employs an asymmetric “V” after the word “Verizon,” which is exploited by threat actors during the attack: “We found three variants of fake logos, each employing mathematical symbols to supplant the legitimate element employed by the company,” the report states.
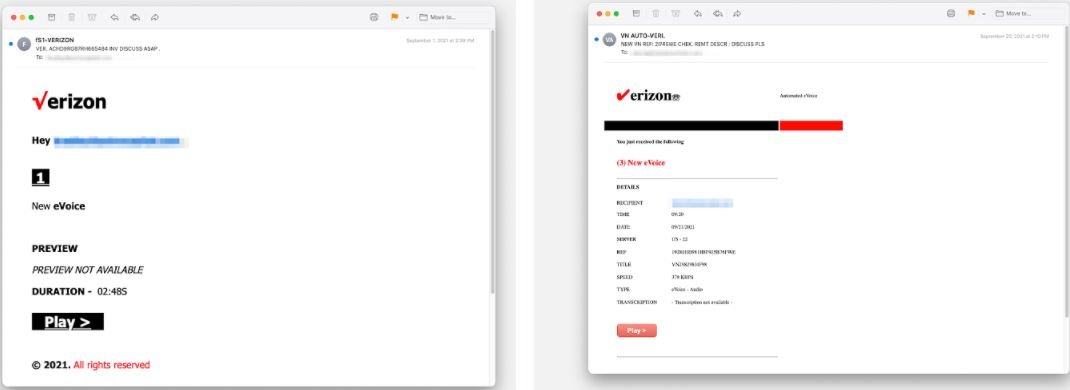
In addition to the square root symbol, the researchers use:
- A NOR logic operator
- A verification symbol
In addition to this ingenious method for avoiding anti-spam techniques, threat actors employed conventional phishing tactics. This includes the use of a voice message allegedly sent by Verizon; selecting the “Play” button will redirect the user to a phishing website where they will be asked to register as if it were the Office365 page.
After entering their credentials on this malicious website, victims will find an “incorrect password” message, so they could re-enter their data to the website: “In this way, the information is stored in the backend,” experts mention. This is a very common technique in phishing attacks, since threat actors seek that the victim correct potential errors when entering their password, or that they try another word of security and thus cover all the possibilities.
Finally, experts point out that the malicious website used in this attack was registered very recently and is riddled with zero-day exploits, so it is possible that this campaign is not limited to the deployment of phishing messages. In any case, evidence of second-stage attacks linked to this campaign has not yet been identified.
For users who have received a message with these characteristics, experts recommend contacting Verizon to rule out any possible damage linked to their accounts, in addition to ignoring any similar messages.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
