A team of specialists led by Italian researcher Massimiliano Brolli reported the discovery of three new vulnerabilities affecting Oracle GlassFish and Nokia NetAct.
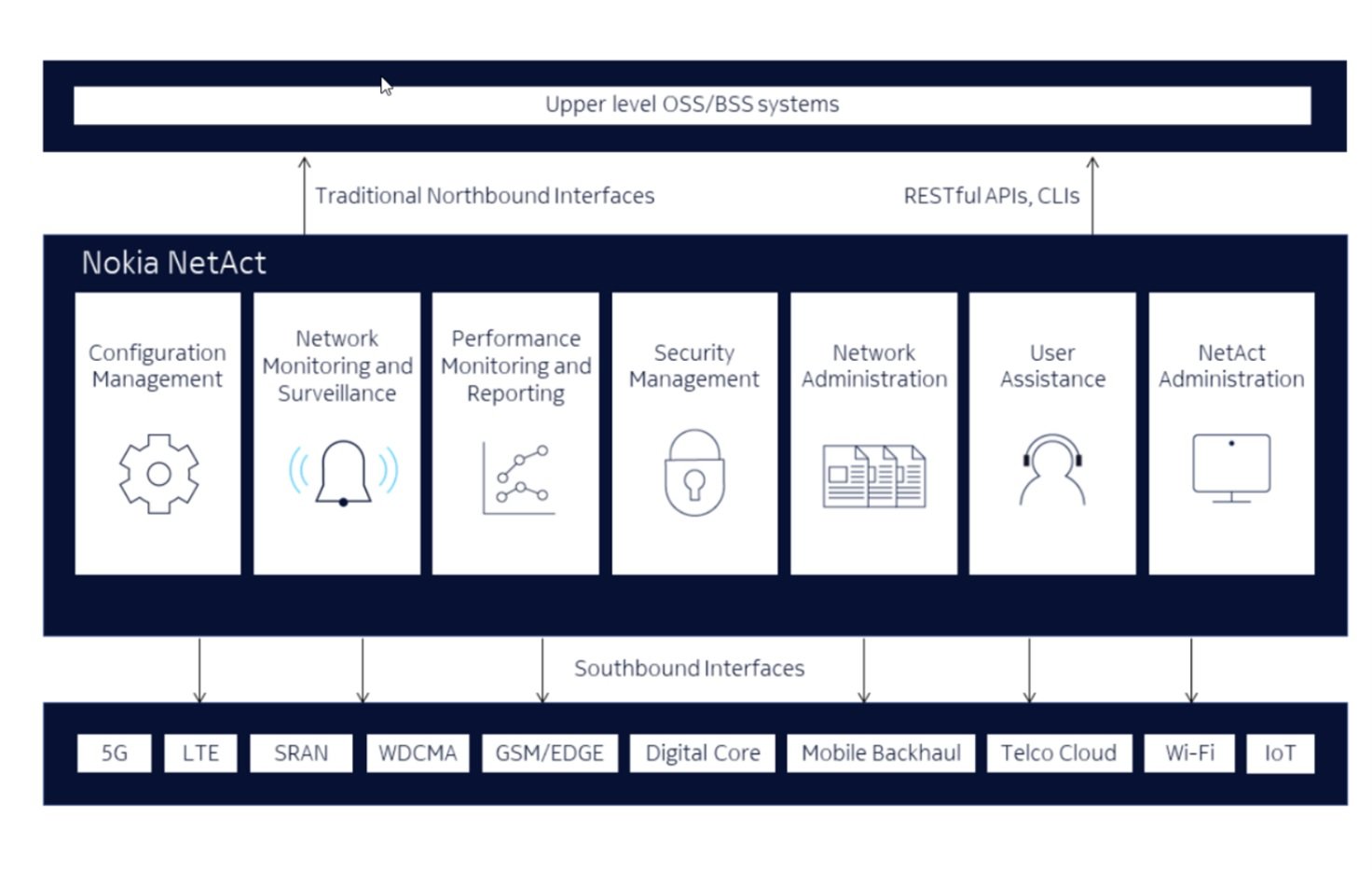
According to the report, two of these flaws affect Nokia NetAct, a mobile network management system that supports 5G, 4G, 3G and 2G technologies. This system also supports network elements in mobile radio and core network, WiFi, Internet of Things (IoT), public safety and telecommunications cloud.
On the other hand, the third flaw was found in GlassFish, an Oracle product that offers full support for Java EE 8 specifications with the latest API versions for technologies such as Java Servlet 4, JavaServer Pages and Enterprise JavaBeans.
Tracked as CVE-2021-26597, the first of the flaws was described as an unrestricted file upload error in Nokia NetAct 18A which would allow a remote user authenticated on the NOKIA NetAct website to visit the Site Configuration Tool section to upload potentially malicious files without any restriction using the /netact/sct dir parameter.
The second flaw, tracked as CVE-2021-26596, was described as improper neutralization of the input during the generation of the web page in Nokia NetAct 18A. Malicious users could rename a file in order to include JavaScript code that could eventually be stored and executed in the victim’s web browser.
Finally, CVE-2021-3314 resides on Oracle GlassFish Server and is described as a cross site scripting (XSS) vulnerability that exists due to improper neutralization of inputs when generating a web page.
Threat actors can cause an administrator to provide dangerous content to the vulnerable page, which is then reflected off the user and executed by the web browser. This flaw only affects products that have already reached the end of their support.
The flaws reportedly affect all sorts of companies, including Nokia, Oracle, Siemens, IBM, Selesta, Johnson & Controls, Schneider Electric and other members of the technology industry.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
